There was a time when networks were secure islands, used to connect PCs to services they consumed and each other. The network was protected from the outside world by a perimeter firewall: there was only one way in and out.
With the explosion in wireless networking and the use of personal devices in corporate environments, the security perimeter has dissolved. More open access to the corporate network has massively increased the attack surface for potential bad actors.
In order to secure the network, we now look to the access network and identify potential threats as they connect. Enter 802.1X - the IEEE standard which describes the use of Extensible Authentication Protocol (EAP) on the LAN. This provides a method of proving the identity of a client device and/or user. We can then provide a security policy enforcement point at the edge of the network.
Typically, this is a fraught rollout process. Firstly, a pilot phase is used to check that different combinations of network hardware and endpoint devices are able to work together. This often highlights specific issues with certain types of endpoint or operating system, leading to more detailed analysis.
Next, policies are built to allow or deny access based on the results of the authentication. Templates are then built for configuration and policy, and a phased rollout schedule defined.
Typically, there are two stages to each rollout phase. The first is putting the ports into "monitoring" mode - enforcing the authentication to take place, but not the policy associated. If there are problems with authentication, users can still access the network. Policy enforcement is later enabled after a period of monitoring, allowing authentication issues to be ironed out.
A key part to the rollout process is documenting both the configuration templates and the extent of the rollout activity, in both monitoring and enforcement modes. From a support perspective, rollout of 802.1X is a significant change and a potentially painful one due to the interaction of endpoint with network, and the potential impact of failure. If a client can't authenticate, the user will lose access to all network services!
So how to verify where 802.1X is configured, and that it is behaving as expected? Without accurate detailed documentation, the only way to confirm this is to:
Clearly a complex and long-winded process!
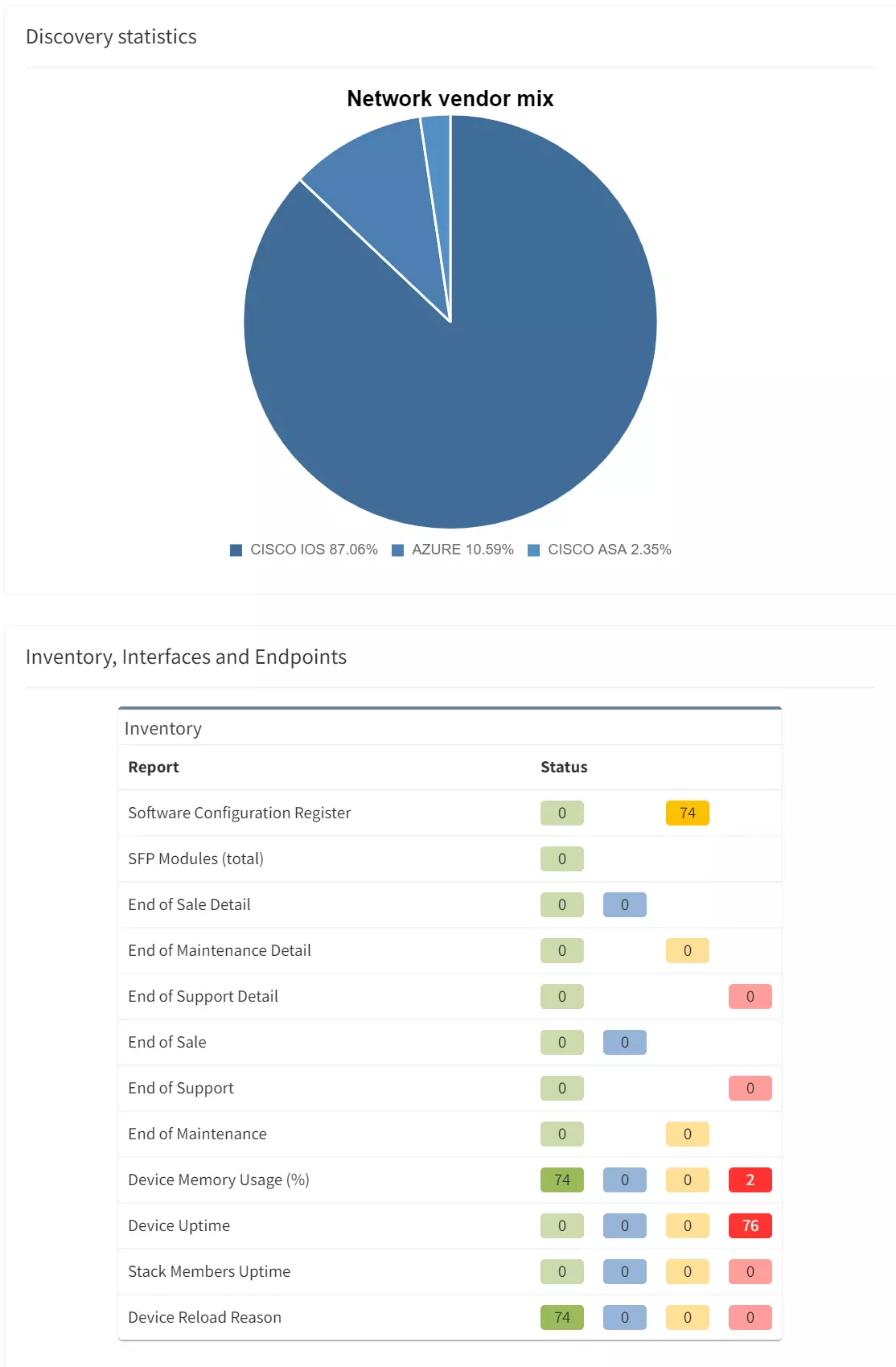
The IP Fabric discovery process identifies "edge" ports by detecting where hosts are directly connected. Once we have that information, we also collect whether those edge ports are configured for 802.1X. And so we have instant access to the information simply by filtering the appropriate table in IP Fabric:
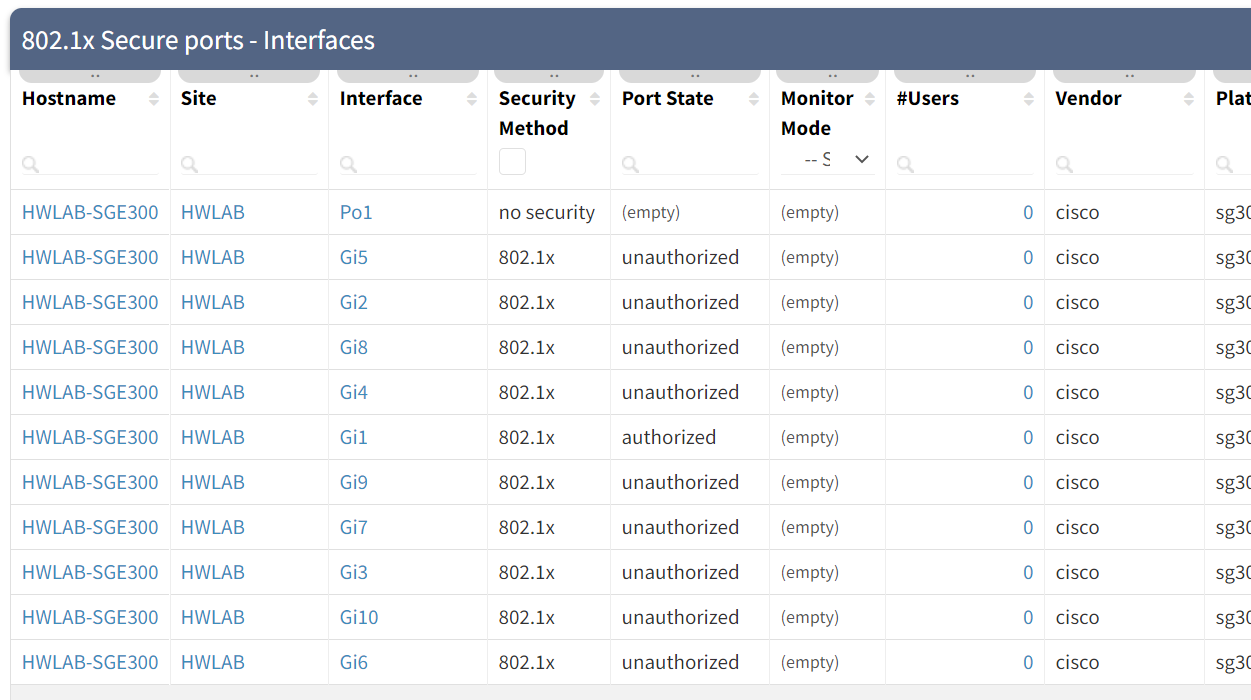
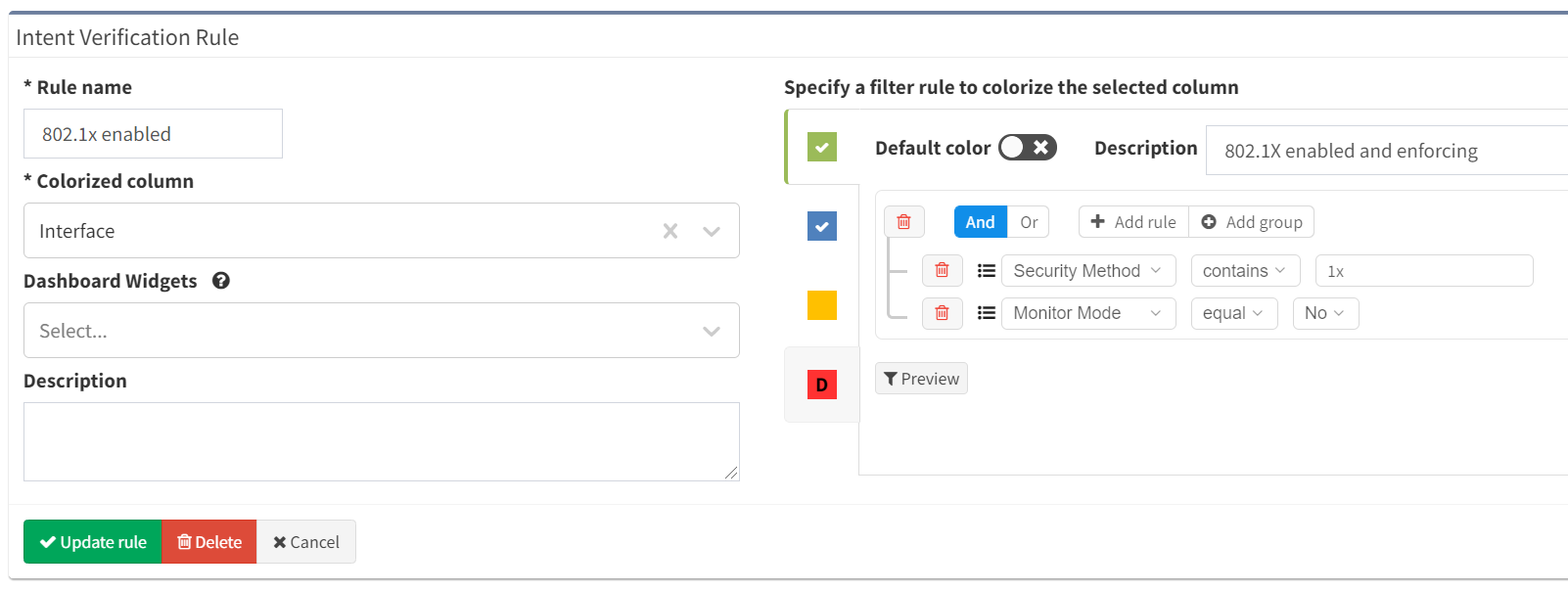
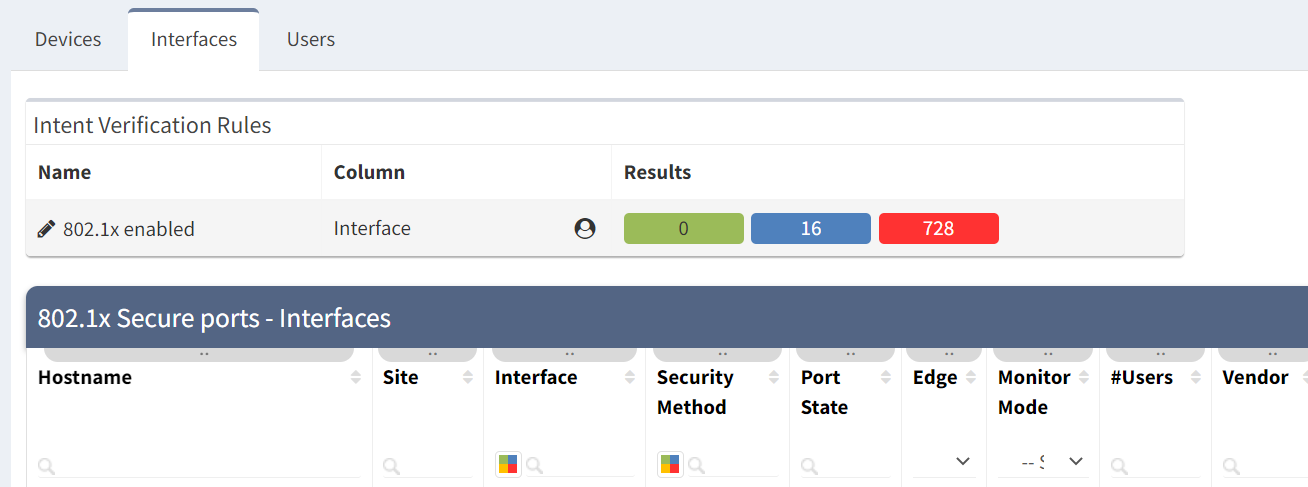
You can also see from the table that we can track whether those interfaces are in monitor mode or not. Using this information, we can create an intent verification check to track how many interfaces are configured for 802.1X and enforcing:
or remain in monitoring mode:
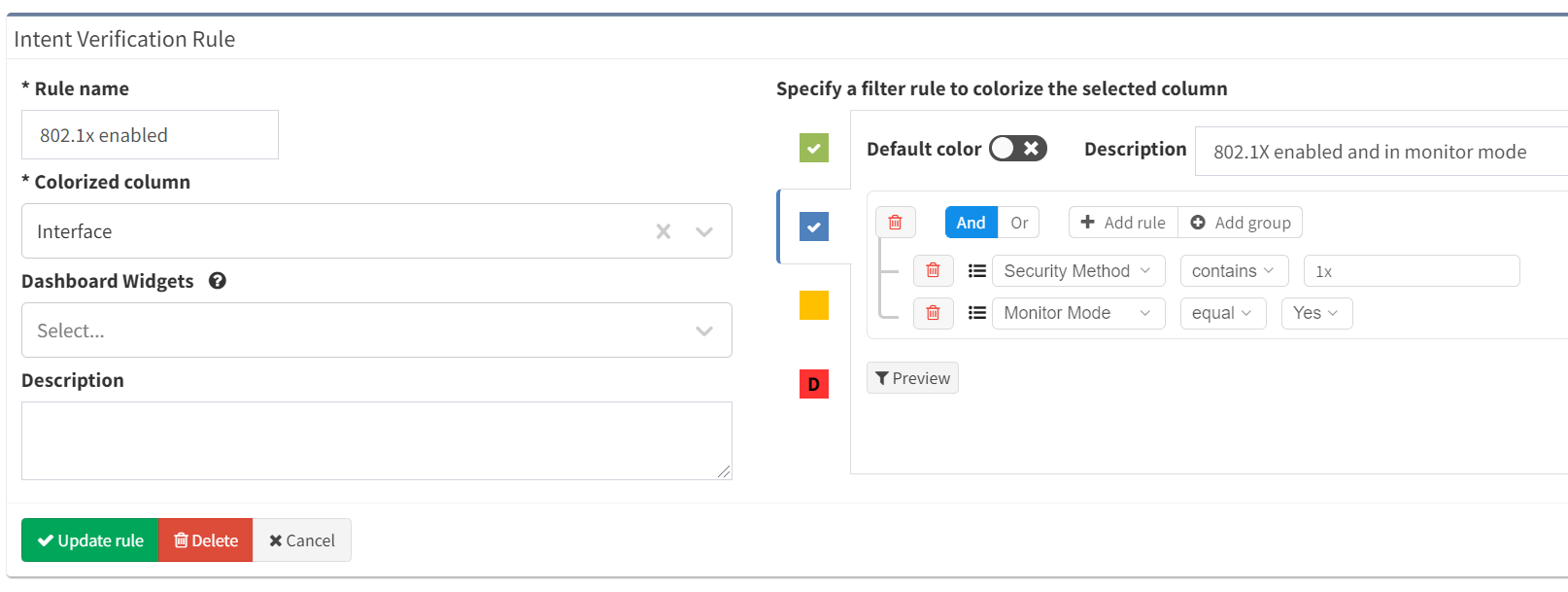
The summary displayed above the table shows the number of matches to each rule:
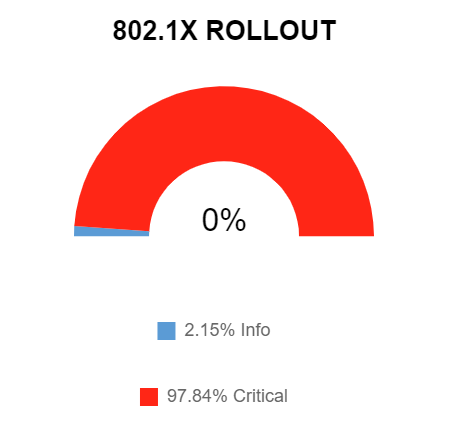
Using that same data, we can also build a dashboard widget to show progress of the rollout of configuration. For example, the widget below shows that most ports aren't configured with the remaining 2% enabled but in monitoring mode. You can see how this visualisation would be useful to track the project status, using data captured by IP Fabric automatically.
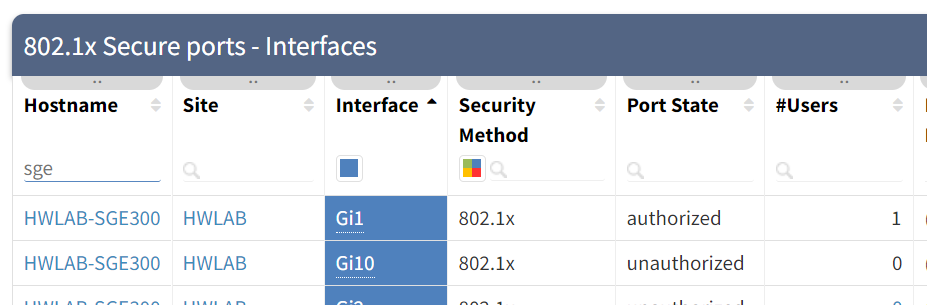
Once the rollout is progressing, the table will be updated at each snapshot with the state of each port, showing whether endpoints are authorised and users are able to join the network:
IP Fabric will even show you user details if they have used their username and password to authenticate! So you can see that we have you covered for rolling out and operating an 802.1X secured network!
If you have found this article helpful, please follow our company’s LinkedIn or Blog, where more content will be emerging. If you would like to test our solution to see for yourself how IP Fabric can help you manage your network more effectively, please contact us through www.ipfabric.io.
There was a time when networks were secure islands, used to connect PCs to services they consumed and each other. The network was protected from the outside world by a perimeter firewall: there was only one way in and out.
With the explosion in wireless networking and the use of personal devices in corporate environments, the security perimeter has dissolved. More open access to the corporate network has massively increased the attack surface for potential bad actors.
In order to secure the network, we now look to the access network and identify potential threats as they connect. Enter 802.1X - the IEEE standard which describes the use of Extensible Authentication Protocol (EAP) on the LAN. This provides a method of proving the identity of a client device and/or user. We can then provide a security policy enforcement point at the edge of the network.
Typically, this is a fraught rollout process. Firstly, a pilot phase is used to check that different combinations of network hardware and endpoint devices are able to work together. This often highlights specific issues with certain types of endpoint or operating system, leading to more detailed analysis.
Next, policies are built to allow or deny access based on the results of the authentication. Templates are then built for configuration and policy, and a phased rollout schedule defined.
Typically, there are two stages to each rollout phase. The first is putting the ports into "monitoring" mode - enforcing the authentication to take place, but not the policy associated. If there are problems with authentication, users can still access the network. Policy enforcement is later enabled after a period of monitoring, allowing authentication issues to be ironed out.
A key part to the rollout process is documenting both the configuration templates and the extent of the rollout activity, in both monitoring and enforcement modes. From a support perspective, rollout of 802.1X is a significant change and a potentially painful one due to the interaction of endpoint with network, and the potential impact of failure. If a client can't authenticate, the user will lose access to all network services!
So how to verify where 802.1X is configured, and that it is behaving as expected? Without accurate detailed documentation, the only way to confirm this is to:
Clearly a complex and long-winded process!
The IP Fabric discovery process identifies "edge" ports by detecting where hosts are directly connected. Once we have that information, we also collect whether those edge ports are configured for 802.1X. And so we have instant access to the information simply by filtering the appropriate table in IP Fabric:

You can also see from the table that we can track whether those interfaces are in monitor mode or not. Using this information, we can create an intent verification check to track how many interfaces are configured for 802.1X and enforcing:

or remain in monitoring mode:

The summary displayed above the table shows the number of matches to each rule:

Using that same data, we can also build a dashboard widget to show progress of the rollout of configuration. For example, the widget below shows that most ports aren't configured with the remaining 2% enabled but in monitoring mode. You can see how this visualisation would be useful to track the project status, using data captured by IP Fabric automatically.

Once the rollout is progressing, the table will be updated at each snapshot with the state of each port, showing whether endpoints are authorised and users are able to join the network:

IP Fabric will even show you user details if they have used their username and password to authenticate! So you can see that we have you covered for rolling out and operating an 802.1X secured network!
If you have found this article helpful, please follow our company’s LinkedIn or Blog, where more content will be emerging. If you would like to test our solution to see for yourself how IP Fabric can help you manage your network more effectively, please contact us through www.ipfabric.io.