To address Cobit 2019 certification we need to make sure we have an understanding of what Cobit stands for, "Control Objectives for Information and Related Technology". First of all, it was mainly focused on auditing, specifically helping financial auditors navigate IT environments. Now it is the leading framework for the governance and management of enterprise IT. It includes breadth of tools, resources and guidance. Its main value is leveraging proven practices to inspire IT innovation and fuel business success.
The network infrastructure is the most critical underlay for any applications running in enterprise environments. In addition, data security is critical to any organization. That's the reason why at least some information security standard must be incorporated. This applies to anyone who aims to keep the data well protected.

Any value created in the digital world automatically attracts those who intend to capture its value. Of course without any necessary permission. It can be a hacker or medium-skilled student with malicious intent. But it's not important who desires to access your data or why. Without following any security best practices, you are out in the open.
Moreover, in our previous post related to security audits automation, other relevant information related to Cobit can be found. In this article, we will focus on how the IP Fabric platform can assist with network security management. Further, bringing benefits to everyday operations.
At first, the IT domain needs to be perfectly specified and well-aligned with the business goals. The starting point for further security practices development in any certification is to be aware of all its infrastructure elements.
The infrastructure elements may include all active network devices (routers, switches, firewalls, load-balancers, etc.), a full inventory of end-points (virtual or physical servers) communicating on the network or entry points to the network (available physical interfaces, wireless access points and more). All in all, an up-to-date detailed inventory is the most important factor for any enablement.

For the IP Fabric platform, the full and up-to-date inventory of any elements on the network is an easy task. It provides its users with complete visibility. Moreover with multiple views and end-of-life information, with automated protocol level diagrams fresh every day. Apart from that, all data is easily exportable manually or by any integrated system via API.
The definition above relates to mapping existing information flows across routed or switched networks with clear security objectives. Firewalls with properly configured security policies are the key components in building secure networks and preventing unwanted access.
However as the network grows in complexity, more teams participate in network security policies administration. Hence, the restrictive rules may be violated with unauthorized or temporary changes on firewalls or access-lists.
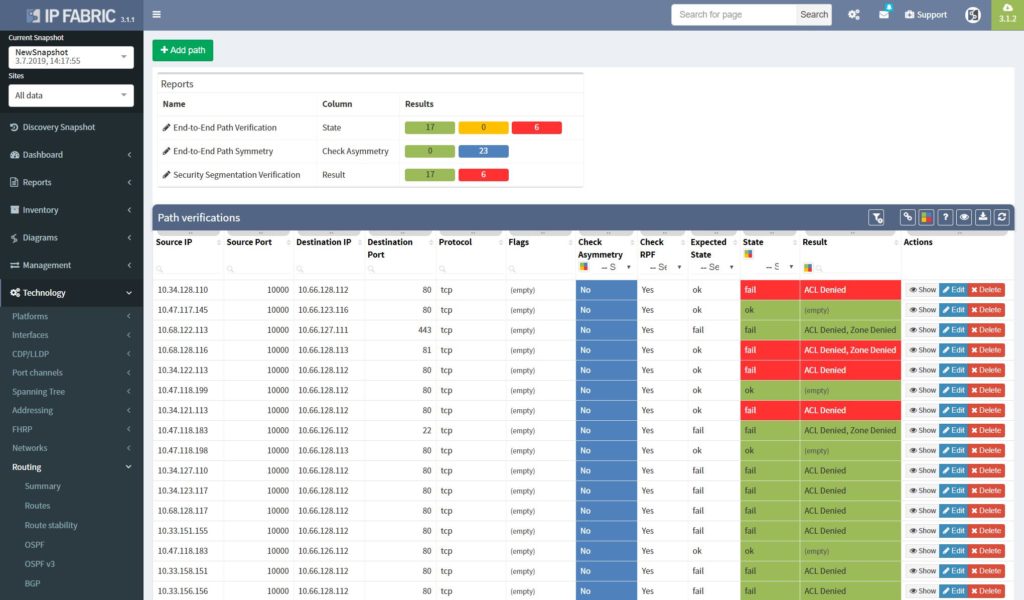
The best approach to a stable security environment that meets the high standards is continuous security policies and end-to-end path verification. In addition, with the IP Fabric platform, users are provided with the tool that can help with both. The platform reads and stores all security policies from selected vendors. As well as, immediately detecting changes and providing historical data. Besides, with the end-to-end path testing feature available, it can store hundreds of defined path checks, that are being continuously verified with every new network snapshot.
The network management misconfigurations are maybe one of the most discovered with the IP Fabric tool at the first run. What we often detect with automated verifications is legacy Simple Network Management Protocol (SNMP) configurations, old TACACS+ or RADIUS servers left in or outdated access-lists (ACL) applied to management interfaces.
If you have found this article resourceful, please follow our company’s LinkedIn or Blog, where there will be more content emerging. Furthermore, if you would like to test our platform to observe how it can assist you in more efficiently managing your network, please write us through our web page www.ipfabric.io
International standard or ISO 27001 certification is helping organizations to better understand network and security area administration. It also defines models for increasing network and security resilience and other features.
To begin with, the network infrastructure has become more and more important for many organizations. Hence, nothing is more valuable than data being transferred between the systems or stored within the secured perimeter. That's why the information security standard should be incorporated by anyone who aims to keep the data well protected.

Furthermore, any value created in the digital world automatically attracts those who intend capturing the value without any necessary permission. It can be a hacker or medium-skilled student with malicious intent. But it's not important who desires to access your data or why. Without following any security best practices, you are out in the open.
In addition, our previous post related to security audits automation, provides other relevant information to ISO 27001 certification . Further, in this article we will focus on how the IP Fabric platform can assist with network security management. Hence, bringing benefits to everyday operations.
"ISO/IEC 27001 formally specifies an Information Security Management System (ISMS), a suite of activities concerning the management of information risks (called ‘information security risks’ in the standard). The ISMS is an overarching management framework through which the organization identifies, analyzes and addresses its information risks."
From https://www.iso27001security.com/html/27001.html
The definition above perfectly describes the starting point for further security practices development in ISO 27001 certification. However, to proceed with the next steps of the standardization, the company needs to be aware of all infrastructure elements.
The infrastructure elements may include all active network devices (routers, switches, firewalls, load-balancers, etc.). Furthermore, a full inventory of end-points (virtual or physical servers) communicating on the network or entry points to the network. These are available physical interfaces, wireless access points and more. To summarize the point, an up-to-date detailed inventory is the most important factor for any enablement.

For the IP Fabric platform, the full and up-to-date inventory of any elements on the network is an easy task. It provides its users with complete visibility with multiple views and end-of-life information, with automated protocol level diagrams fresh every day. Apart from that, all data is easily exportable manually or by any integrated system via API.
"It recommends information security controls addressing information security control objectives arising from risks to the confidentiality, integrity, and availability of information. Organizations that adopt ISO/IEC 27002 must assess their own information risks, clarify their control objectives and apply suitable controls (or indeed other forms of risk treatment) using the standard for guidance."
From https://www.iso27001security.com/html/27002.html
The definition above relates to mapping existing information flows across routed or switched networks with clear security objectives. Firewalls with properly configured security policies are the key components in building secure networks and preventing unwanted access.
However as the network grows in complexity, more teams participate in network security policies administration. As a result, the restrictive rules may be violated with unauthorized or temporary changes on firewalls or access-lists.

The best approach to a stable security environment that meets the high standards is continuous security policies and end-to-end path verifications. With the IP Fabric platform, users are provided with the tool that can help with both. The platform reads and stores all security policies from selected vendors, it can immediately detect changes and provide historical data. Besides with the end-to-end path testing feature available, it can store hundreds of defined path checks, that are being continuously verified with every new network snapshot.
The network management misconfigurations are maybe one of the most discovered with the IP Fabric tool at the first run. What we often detect with automated verifications is legacy Simple Network Management Protocol (SNMP) configurations, old TACACS+ or RADIUS servers left in or outdated access-lists (ACL) applied to management interfaces.
The operations security is clearly described in Section 12 in ISO 27002 and is essential to any environment compliant with the standard.

If you have found this article resourceful, please follow our company’s LinkedIn or Blog, where there will be more content emerging. Furthermore, if you would like to test our platform to observe how it can assist you in more efficiently managing your network, please write us through our web page www.ipfabric.io
A network security audit is a systematic evaluation of the security of a company’s information systems or network intermediary devices. We evaluate the secureness of the network using a few different sets of criteria, including measuring how well the devices conform to a set of established rules.
A thorough security audit typically assesses the system’s physical configuration, environment, software, information handling processes, and user practices. Traditionally, this process uses up a lot of valuable work hours, and can easily give inaccurate results if a tiny mistake is made anywhere along the way. But today, thanks to IP Fabric, teams can perform this security audit in just under an hour.
Let’s take a look at some of the ways that IP Fabric can help you conduct a network security audit quickly.
When it comes to successfully exporting security policies from SRX, IP Fabric gives you plenty of options.
The very easy one is to export the configuration between security zones to a text file and upload and send them to a customer. But it could be time-consuming for non-Juniper technicians or managers. Also, for some people, it may be difficult to comprehend all the information in the configuration file.
Another option may be buying Junos Space software with the Security Director plugin. Or we could develop any customized script using Junos PyEZ library and export policies to multiple file formats. Both have their downsides.
"As a DC service provider, we have implemented a robust firewall cluster that currently supports more than 2000 clients. These clients request the security reports on a daily basis. The reports have to include the most current security policies configuration as well.
As a result of using the IP Fabric platform, we can create and export a comprehensive report anytime. Typically, fulfilling this request would take all day, but with IP Fabric, this entire process takes mere seconds to finish."
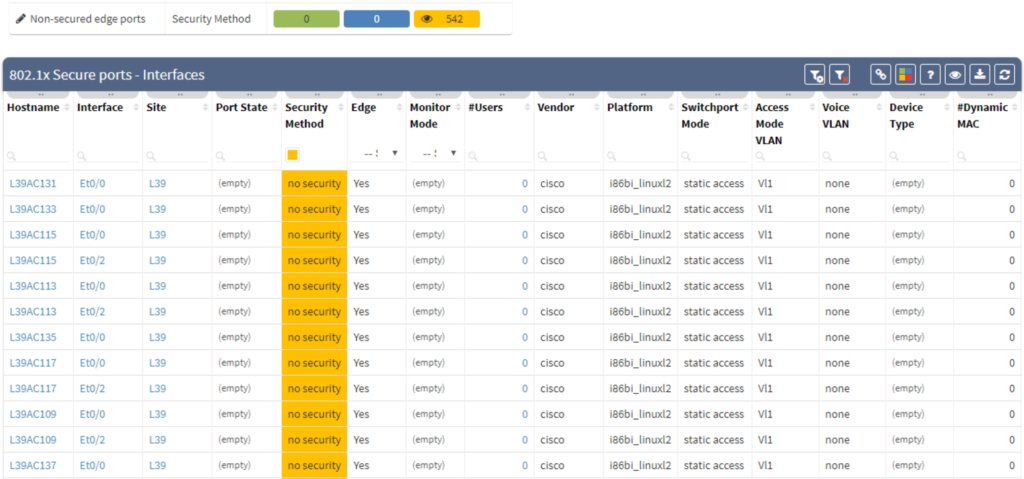
In a multivendor environment, enforcing an authentication means verifying that everything is what it claims to be. The purpose of an 802.1x verification is to help you accept or reject users requesting full-access to a network that uses 802.1X protocol.
Today, more and more companies shift towards tighter LAN security. They’re discovering that this process can cost them countless hours on implementation and verification if they try to do it on their own.
"In our company, we have more than 800 employees at 12 separate locations across the country. Using traditional methods, 802.1X protocol implementation is a long and arduous verification process. It can easily take more than three months to complete.
On the other hand, with the IP Fabric tool, we were able to tackle the verification process almost instantly. The tool simplifies and automates 802.1X verification, allowing us to run it as frequently as needed."
Access-lists (or firewall filters) are a key feature when enhancing security across networks. They deny or grant access to devices based on specific combinations of source, destination IP, destination port, or other kinds of data. ACLs are fast and easy to implement. However, they are difficult to troubleshoot, even when appropriately applied. The IP Fabric platform compiles all of your ACLs into one place, allowing you to compare and correlate rules across all network devices easily.
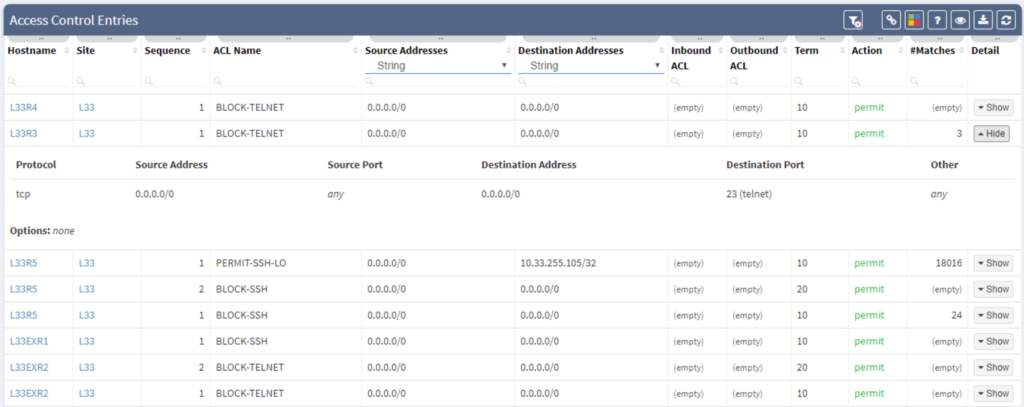
"Our MPLS network has thousands of network devices. To ensure compliance, we need to quickly verify that an up-to-date firewall filter is protecting management loopbacks. The IP Fabric platform can complete this task almost instantly and will give you a comprehensive device list that you can easily export and share."
The Authentication, Authorization, and Accounting system is used to track user activity on an IP-based network and control their access to network resources. It is time-consuming to verify that all network nodes are configured along with the same AAA framework when managing complex network infrastructure.
The IP Fabric platform reduces the amount of time and hassle involved in AAA by giving you a highly detailed overview of all AAA-related information.
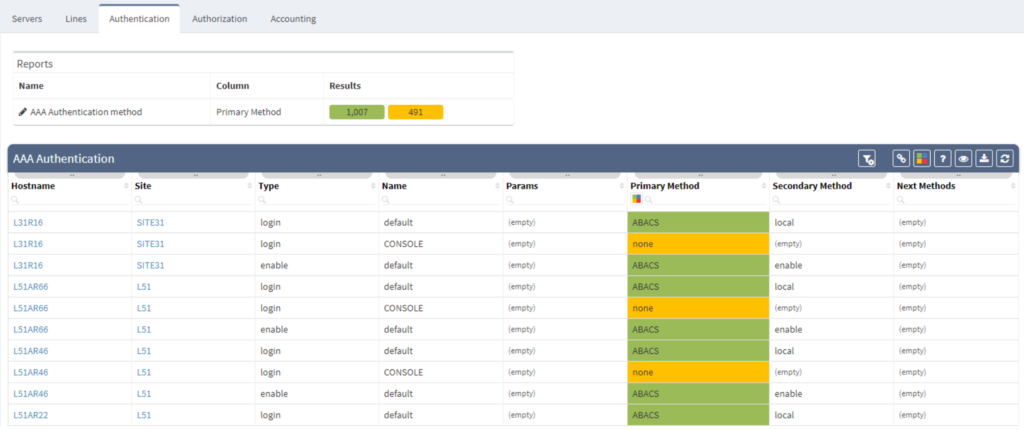
"A few months ago we decided to migrate all of our network devices to a new AAA server, which meant that we also agreed to a change of authorization rules.
The IP Fabric platform made tracking the progress of the migration effortless, meaning we had more time to focus on more critical tasks."
Simple Network Management Protocol (SNMP) and Syslog are the key protocols for maintaining and monitoring network. A network engineer needs to ensure that both protocols are reporting properly to dedicated SNMP and Syslog servers. Above all, one must apply security correctly to this type of communication.
Thanks to IP Fabric, you’ll have a detailed structure report related to these protocols.
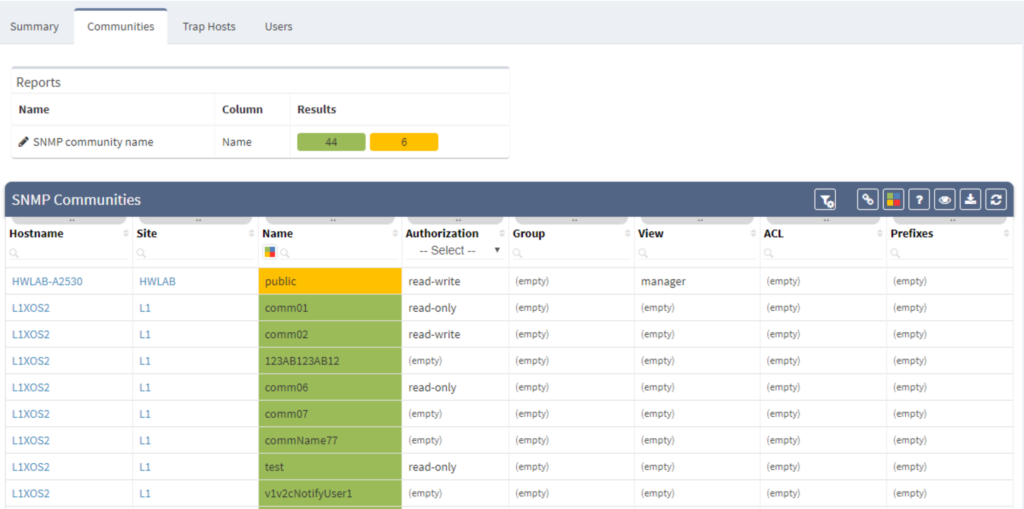
"Over the last 15 years, our network has evolved countless times, and we have lost track of correct SNMP configuration a few times along the way.
Since security is incredibly important to us, we designed the IP Fabric tool to help us verify that all SNMP traffic is sent to dedicated servers and that read-write rules are active at all times."
Interested in learning more about how IP Fabric’s platform can help you with analytics or intended network behavior reporting? Contact us through our website, request a demo, follow this blog, or try our self-guided demo.
With a growing number of customers and requests, the initial plans for minor bugfix release have been expanded into a major release which improves upon nearly all aspects of the product. Here we'll cover the biggest changes in the major release of IP Fabric 3.1.0. Customers can upgrade the installation via the administrative interface by following the procedure in the documentation.
Before we'll go into detail of the changes, let me point out a few of them in the beginning. For visualization, the new View Builder provides the option to create a fully custom diagram views, new manual site separation enables to refine automatic site detection, and improved object manipulation helps to deal with complex diagrams. For vendor and technology support, we've added basic support for Cisco Firepower Thread Defense, added vDOM and Zone Firewall support for Fortinet Fortigate family, and added OSPFv3 support for multiple families. Additionally, we've added customization options for Network Analysis Report, revamped snapshot management, re-engineered backup and restore system and much more, so let's dive straight in!

Based on numerous requests and thanks to our network automation architects, the Cisco Firepower Threat Defense devices are now being supported to complement our ever-expanding portfolio of supported network technologies and vendors. For now, only the basic support has been added as we're exploring use cases with this innovative platform.
The support for the Fortinet FortiGate family was expanded from basic discovery to support Virtual-Domains (VDOM), Zone Firewalls, and Port-Channels. This support has also made into network simulations expanding End-to-End path mapping capabilities with the security layer for this platform.
As more customers are working with IPv6, we've also added support for OSPFv3 for both IPv4 and IPv6 address families. Both technology tables and diagrams now have distinct OPSFv3 options, which include both IPv4 and IPv6 families.
With new released version 3.1.0, we introduce the View Builder. The ultimate feature that allows users to create any customized view of their own topologies and break the boundaries in diagrams. With its intuitive interface, the network devices can form logical groups regardless of any protocol relationship among them. If there is any protocol session between devices, the builder enables to crawl topology further expanding the view. If there is not any relation, the device still can be added manually by clicking the add device + button. The view builder is available through the tools menu in any of the diagrams (three dots).
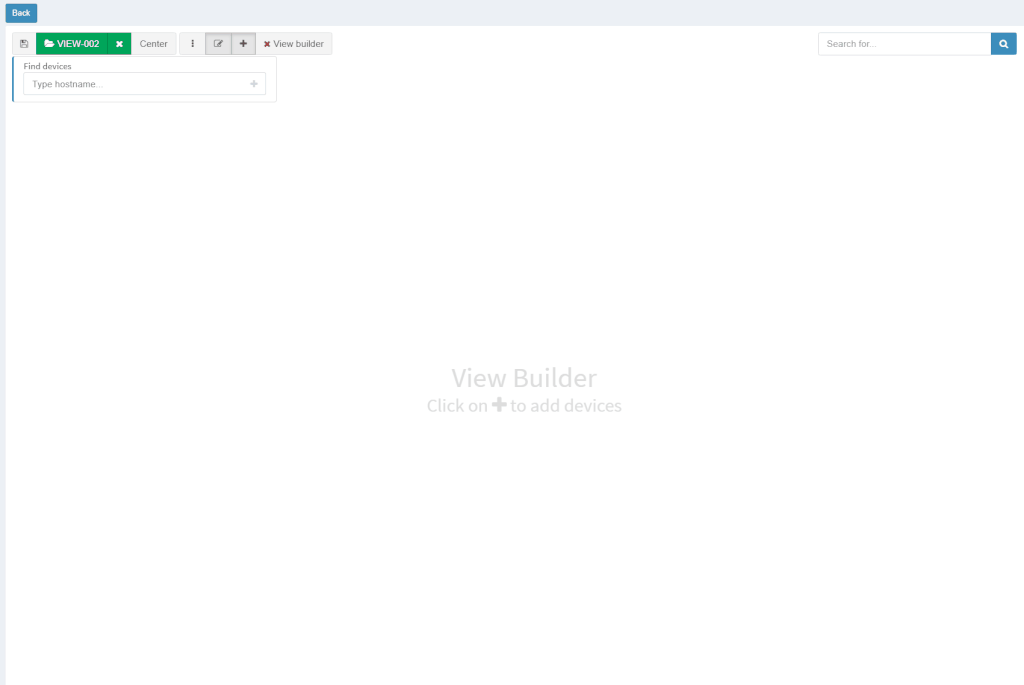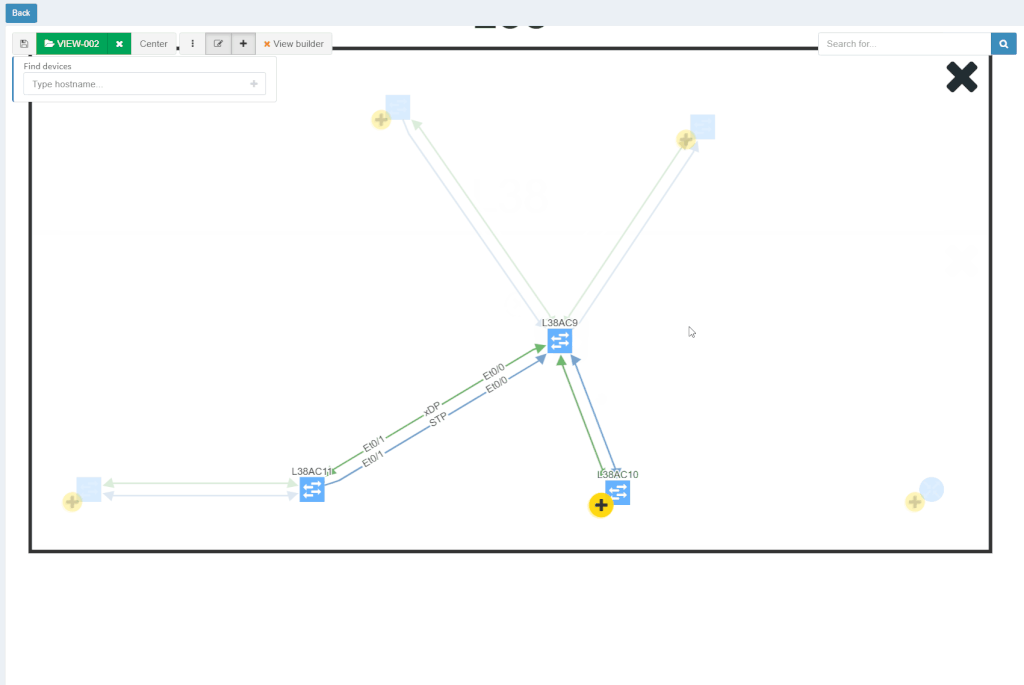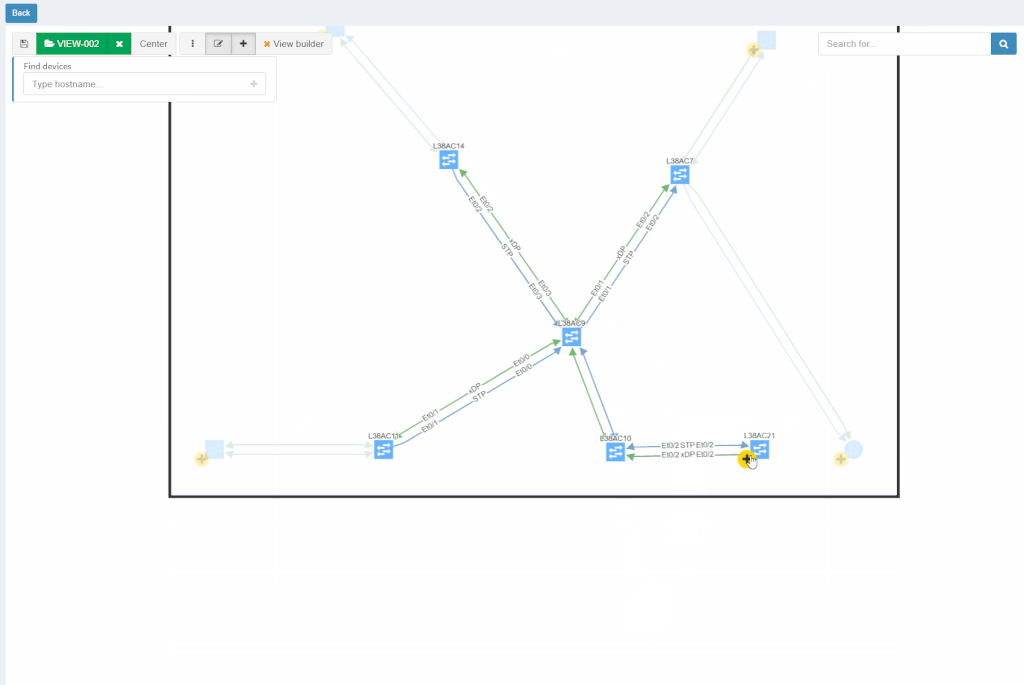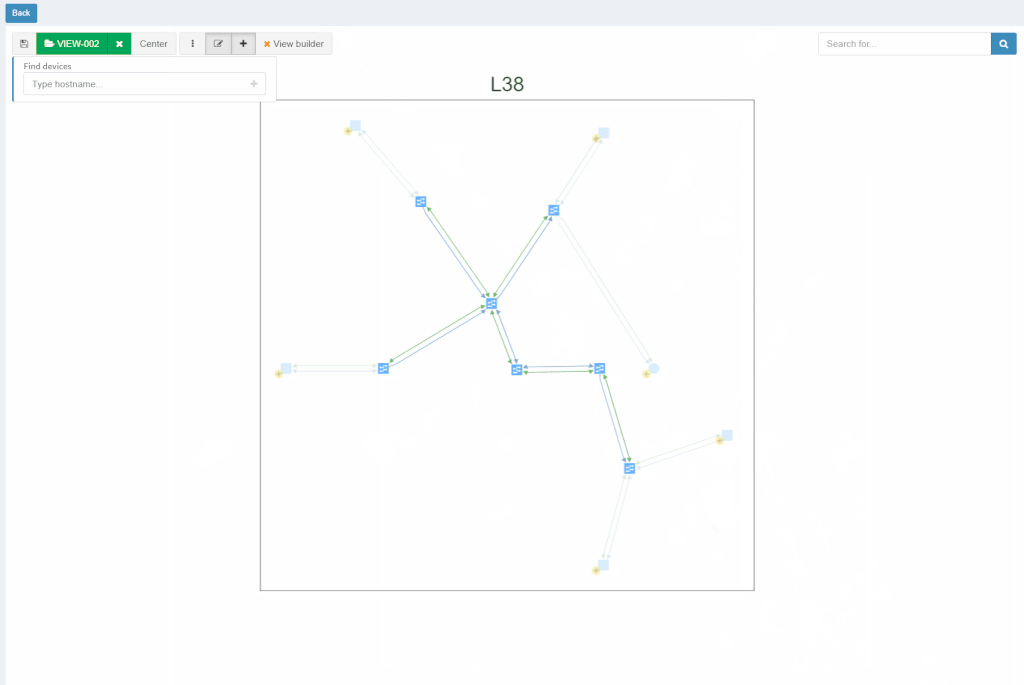
From now on, it is not possible to save the backup data on the same file system where the platform resides. New partition has to be created to save the backup locally. If there's no secondary partition detected, the platform will not let the user save the backup. More information related to new options is available in our online documentation.
Notably, the Discovery and Snapshot Management pages were merged together. This was a logical step for the platform. We had the Discovery and the Snapshot Management on separated pages, however, every new discovery creates a new snapshot. Now it is much easier to navigate and manipulate with snapshots.
Another great news is for API documentation! From now on it's not only available online in the official documentation, but it is also included in the platform itself. At every one of the technology tables, we can now view related API details. This should make it easier to integrate the IP Fabric platform with any other management system.
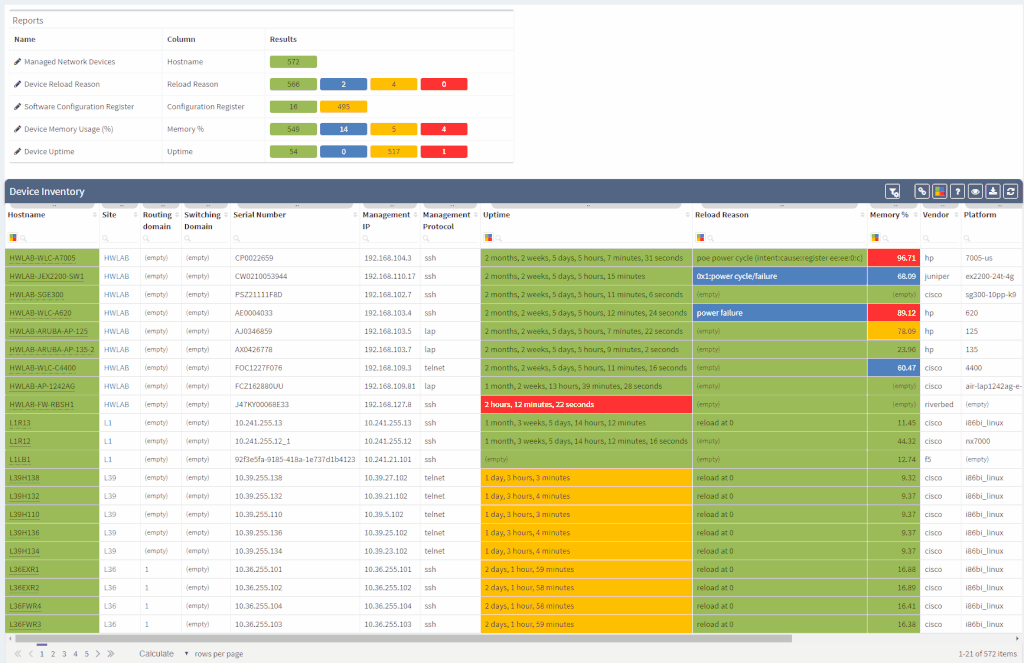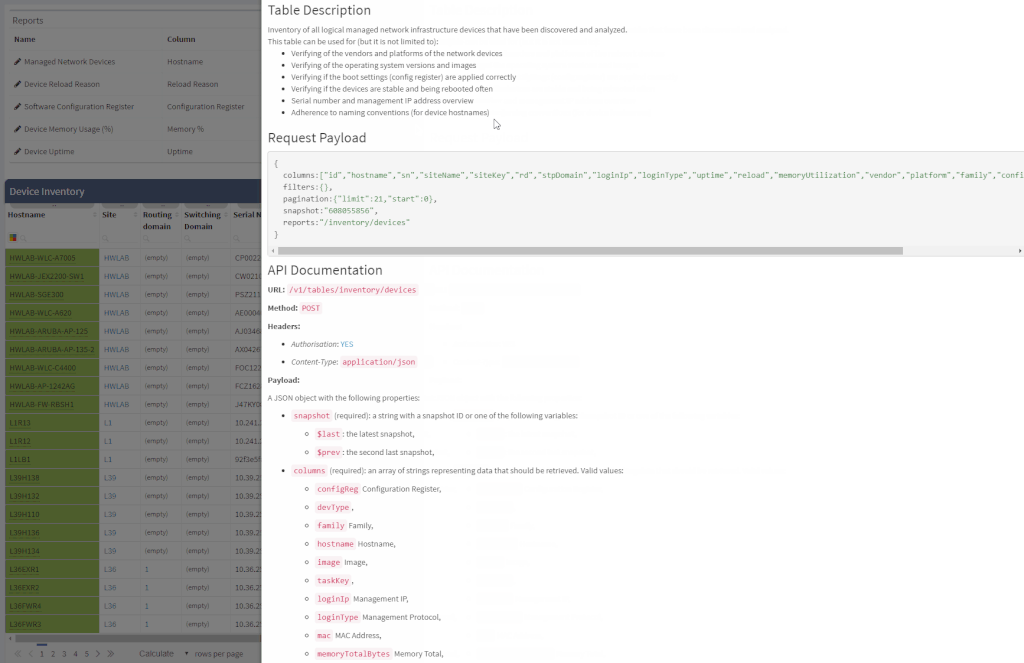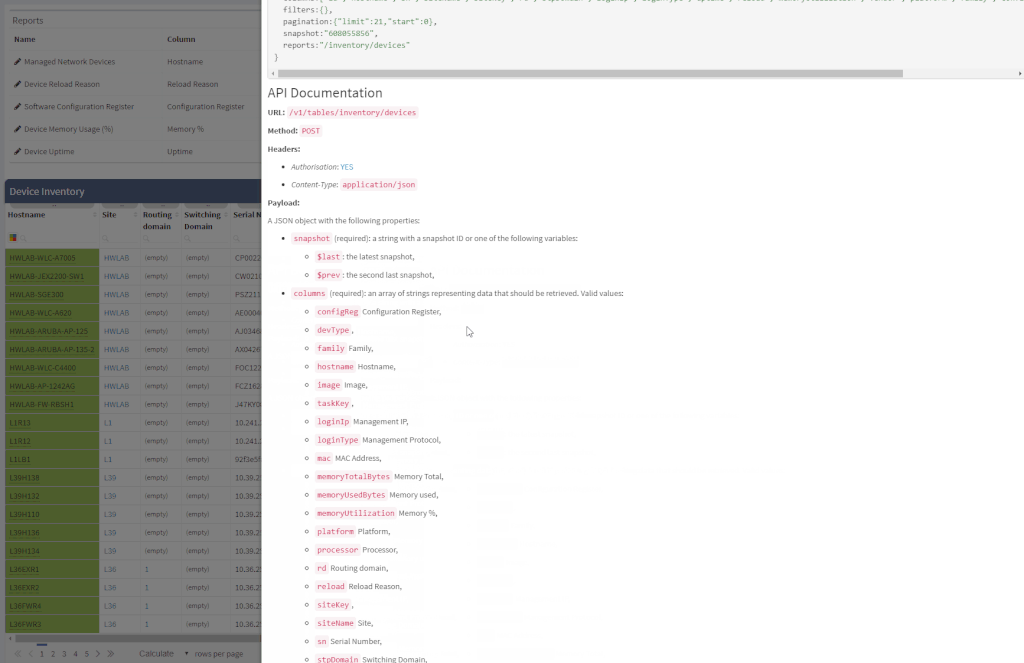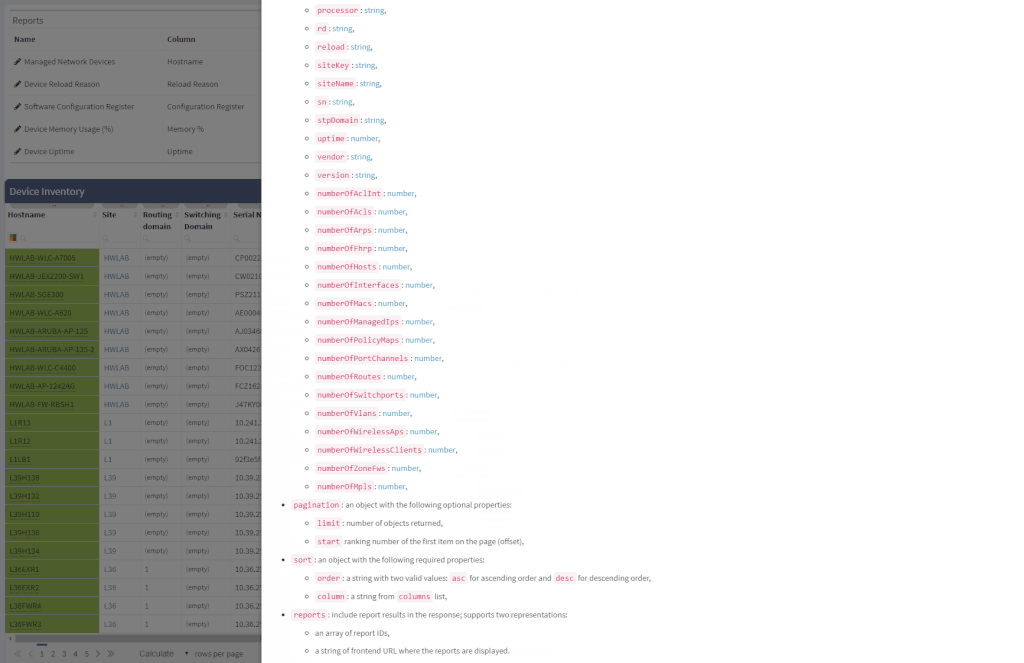
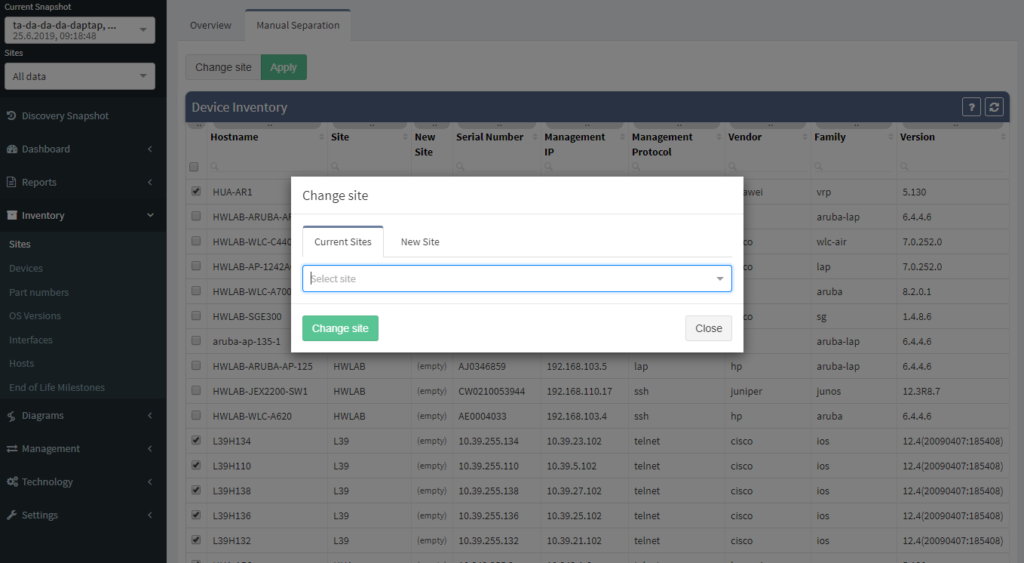
One of the most awaited features is undeniably the Site Separation update. It's only the first step, but the Manual Separation is available in the Inventory - Sites technological table. The logic is that the user would let the system separate the sites automatically and would then use the manual site separation option for fine-tuning and minor corrections through the inventory.
The network verifications are a pivotal part of the IP Fabric platform which enables a proactive approach to network management by uncovering hidden issues that might result in the outage or issue in the future. All network verifications within the IP Fabric platform have been refined to better serve their purpose and we've added descriptions to all of them.
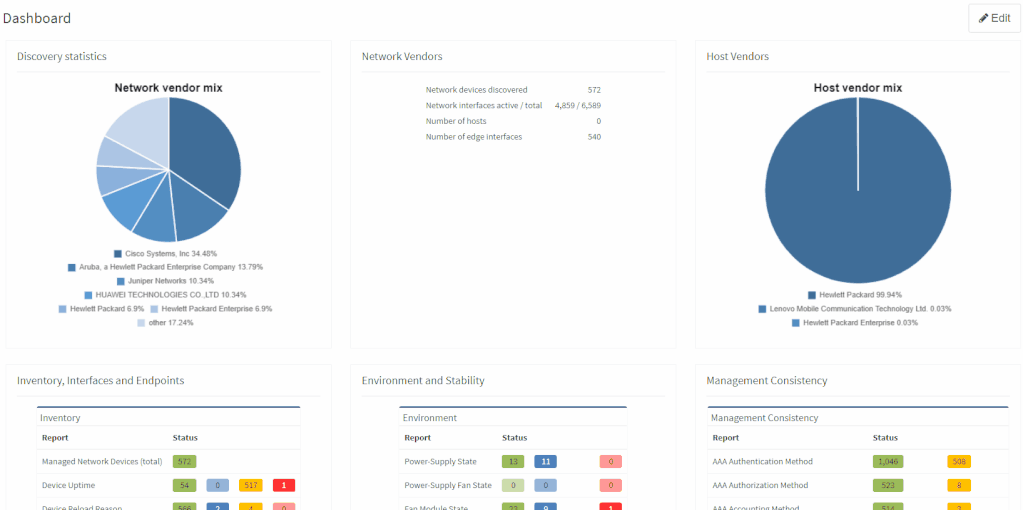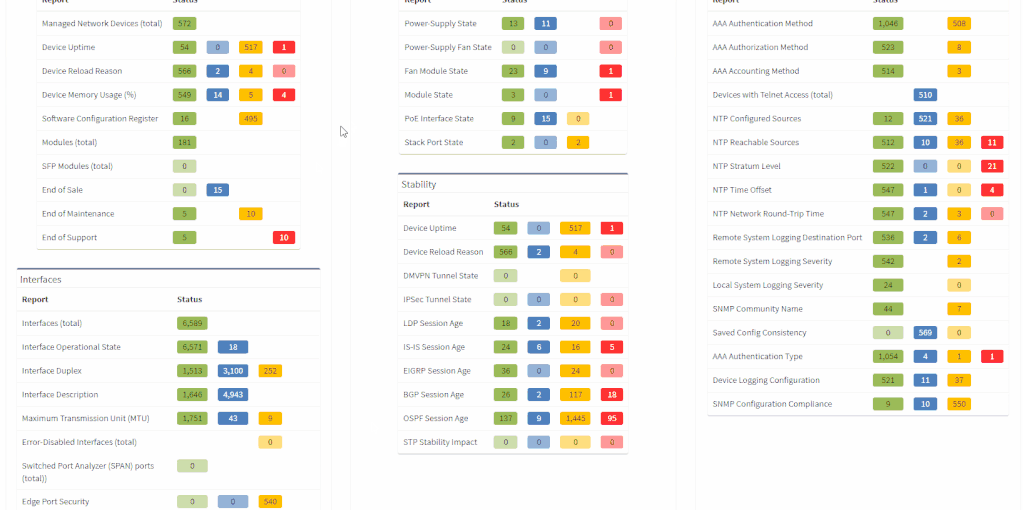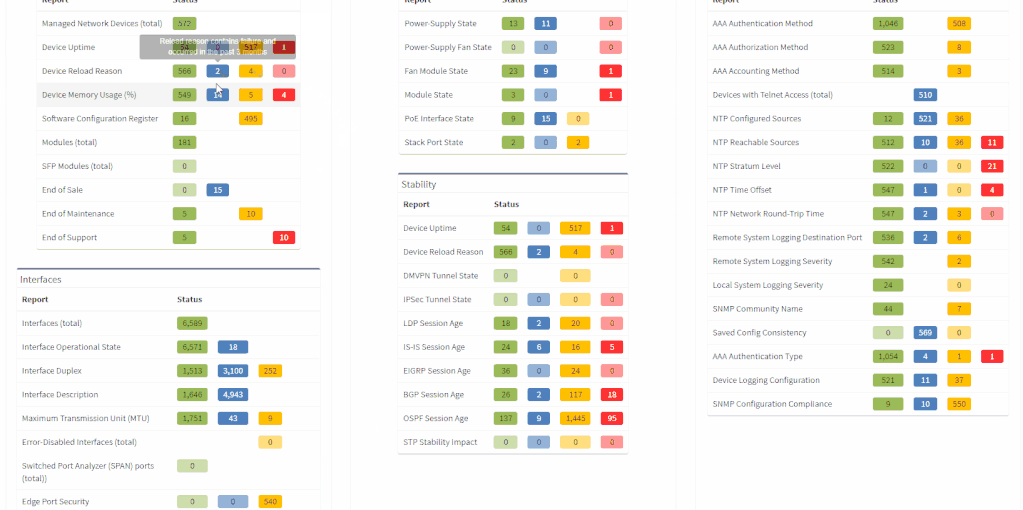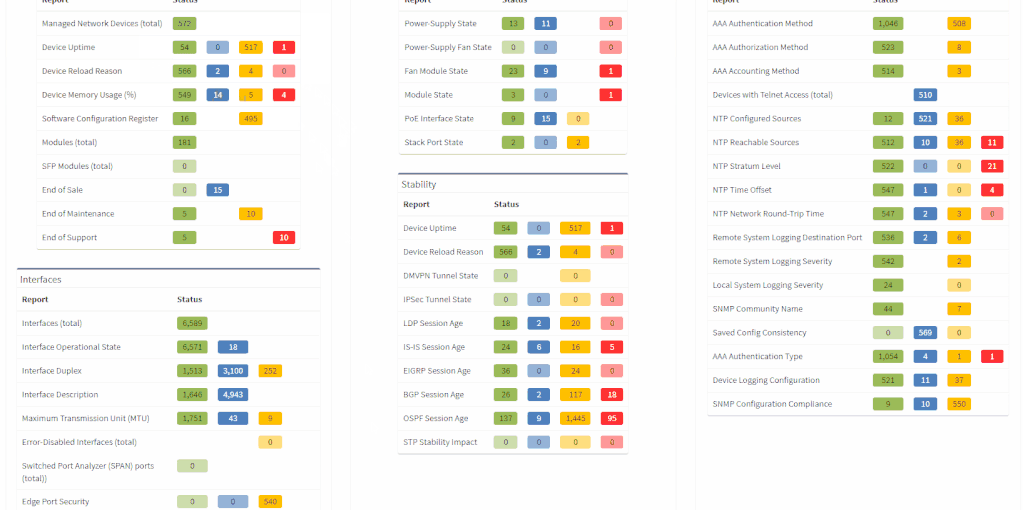
All network verifications that are in the platform by default are still fully customizable and users can create their own of any type and include them in the main Dashboard.
In addition to this update, we've enabled customization of the Network Analysis Report document to reflect the changes and any customizations in the Dashboard, so that the report now includes the result of all verifications, including detailed descriptions of the issues.
This big change also meant any previous dashboard customizations are removed due to the difficulty of migration of old checks without descriptions to new checks with descriptions. Underlying verification definitions have remained in place, so it should be a matter of a few clicks to re-add them, and we'll be happy to help you in case you've lost track of the dashboard customizations.
End to End path simulation continues to be one of the key components in Intent-Based Network Analytics and an important use case of our platform. End-to-End path simulations verify the forwarding and security of any communication pair for every snapshot through our network model in mere milliseconds.
Since we've added support for Fortinet security policies, from now it's possible to verify both forwarding and security policies of Fortinet Fortigate equipment through vDOMs within the End-to-End path forwarding check.
There were a number of refinements to forwarding decision calculations in the network model and updates to the visual representation of the path. For example, MPLS links are now displayed based on the presence of the label stack to help to differentiate where the label is popped through PHP and where it is added.
To read more about individual changes that did not make it into the announcement, you can take a look into release notes.
If you have found this useful, follow our company’s LinkedIn or Blog, sign up for one of the Webinars, or request demo or trial to see how the platform can help you to manage your network infrastructure more effectively. For more information or to contact us please visit www.ipfabric.io.
Would you appreciate much faster end-to-end path lookup simulation on big networks, prettier diagram layout or more extensive routing protocol support? We thought so and that’s why we decided to create even more seamless experience through recent updates. Let’s summarize all the effort.

Special thanks to our Network Automation Architects, the routing protocol support has improved for Border Gateway Protocol (BGP) support, that is now available for majority of the platforms. And the same for IS-IS protocol support, which is now available for more hardware manufacturers than before as well. Apart from that we have also completed Spanning-Tree support for Extreme XOS.
Our core development team pushed their best to create better end-user experience when working with end-to-end path in diagrams. The overall layout of network devices on the path is improved and the user has the option to see isolated path only or include surrounding devices in visualization. Not to mention that query algorithm has been revamped as well, which improved its already satisfying performance.
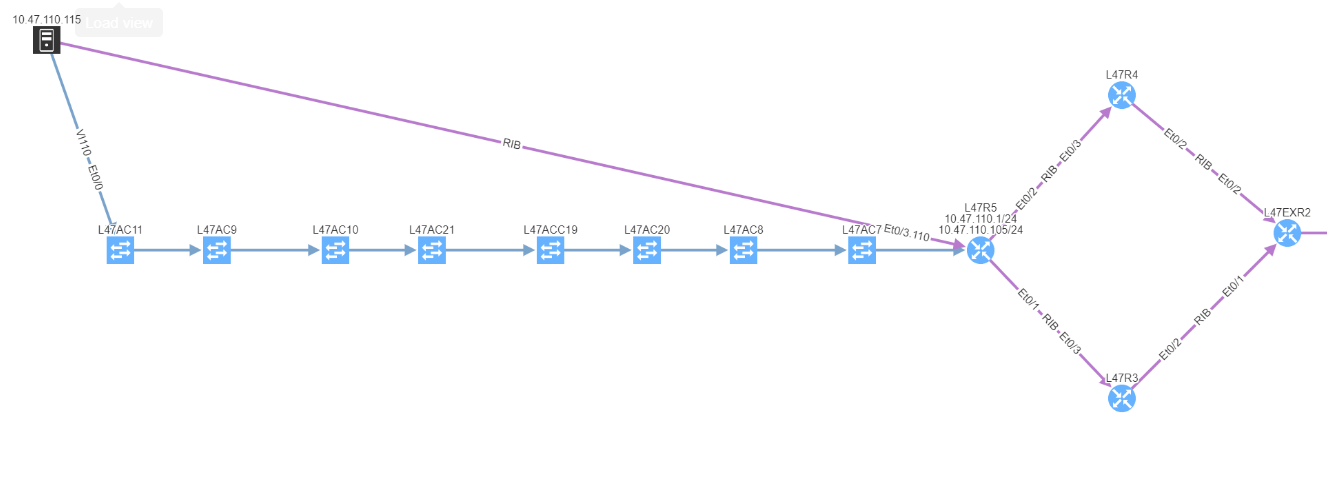
Discovered end points connected to Access-points are now included in end-to-end path simulation besides.
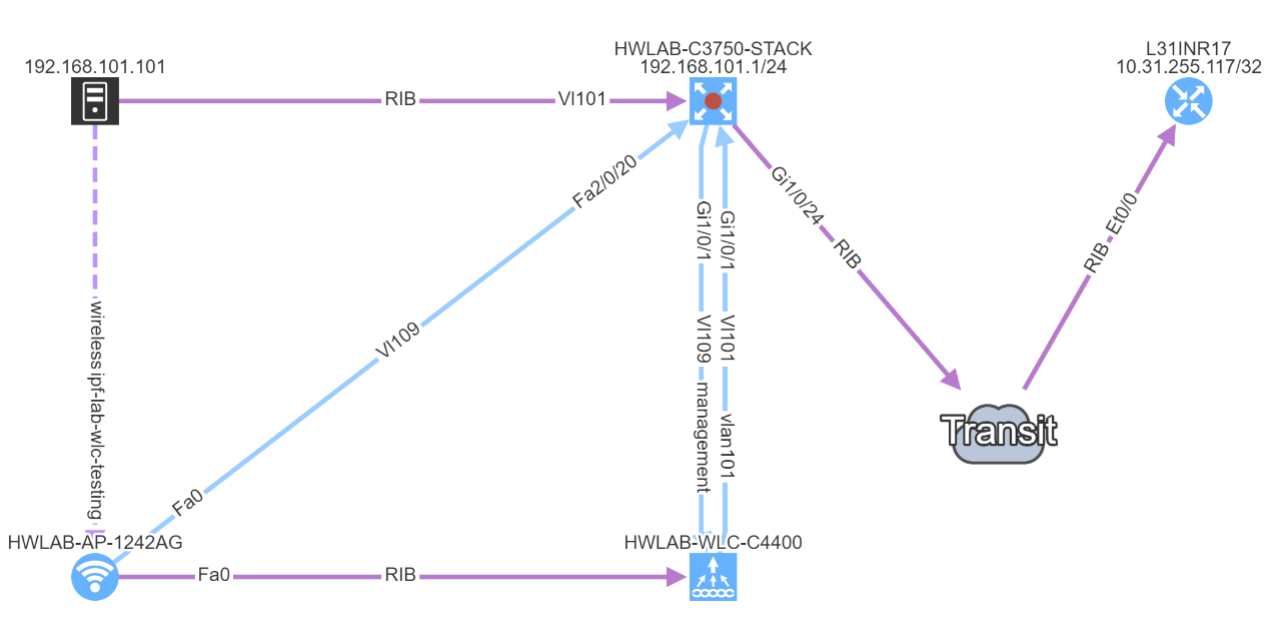
Notably the discovery for some of the HP Aruba switches has been corrected. Another major improvement is with Network history feature. The Network history is available via what we call the Snapshots or Digital footprint of your network. It has started from version 3.0.0. A Snapshot is created with each new discovery and they are often used to view the historical correlation between past and present state.
To be able to use any snapshot, it needs to be available in Random Access Memory (RAM) where the most recent snapshots are being kept. If there’s any historical one that has already moved from RAM to HDD of the virtual machine, it needs to be loaded first. We can currently load up to 5 snapshots at a time. With version 3.0.5, thanks to updated algorithm, the load time is up to four times faster than with previous version.
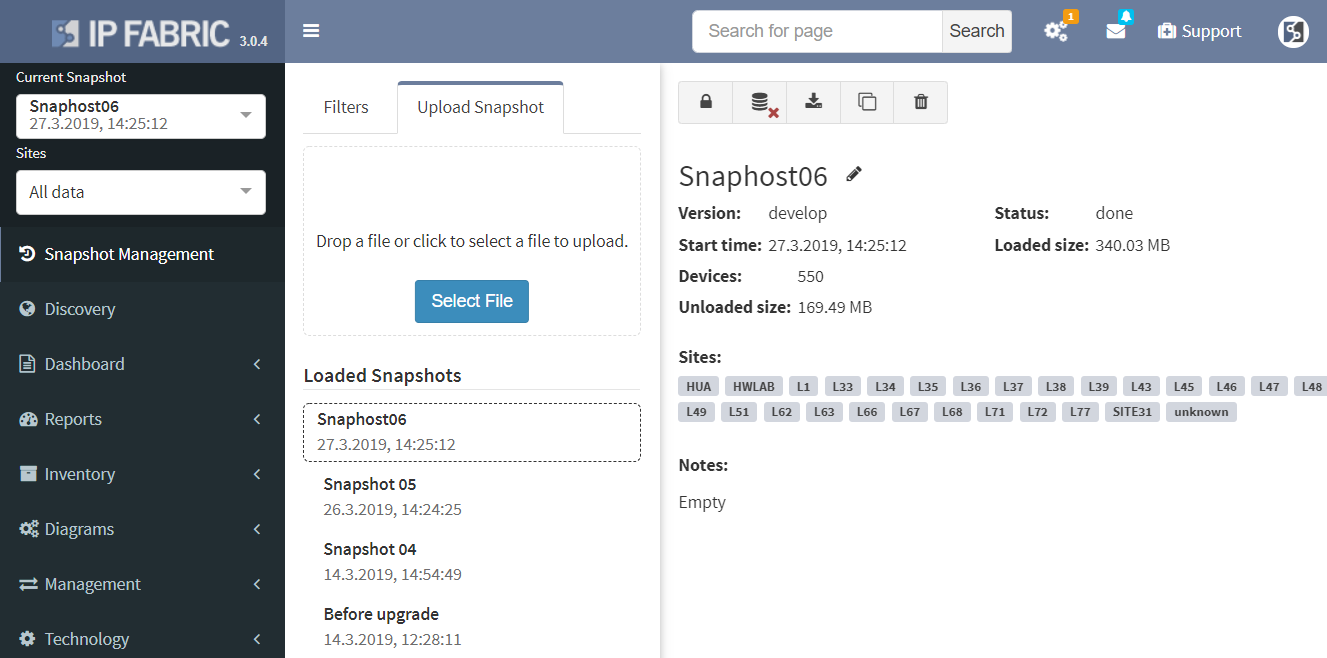
If you have found this article resourceful, please follow our company’s LinkedIn or Blog. There you can find more content emerging. You would like to test our platform and observe how it can assist you in more efficiently managing your network? feel free to contact us through our web page www.ipfabric.io.
As the old saying goes, “the secret to getting ahead is to get started.” To help you start saving time with IP Fabric’s platform, I wanted to walk you through the initial setup process, step-by-step.
But before we get to the setup guide, we’re going to tackle the questions we hear the most from users when they’re setting up the IP Fabric platform for the first time:
IP Fabric’s platform is a plug-and-play OVA image that runs on VMware. Since it runs in a virtual environment as a standalone server, you don’t need any additional support services or licenses.
The discovery process is very similar to how administrator and network devices interact; the platform uses SSH or Telnet to connect to an active device and collects data using a predefined set of commands (which may vary between different hardware vendors and families).
No. Since there isn’t enough information included in SNMP, IP Fabric’s platform doesn’t use SNMP protocol to collect information. Now that we’ve covered all of that let’s move on to the initial setup process.
1. After you’ve successfully installed the platform in a VMware environment with the appropriate IP and default gateway properties, follow these steps:
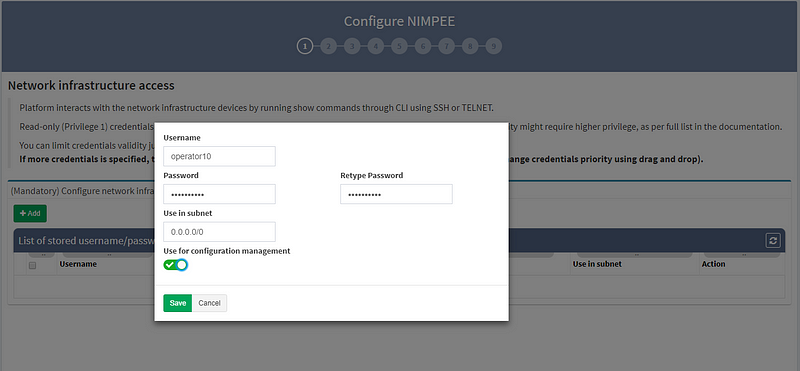
2. Next, enter the “enable password,” which allows you to move from User EXEC mode to Privileged EXEC mode on some devices.
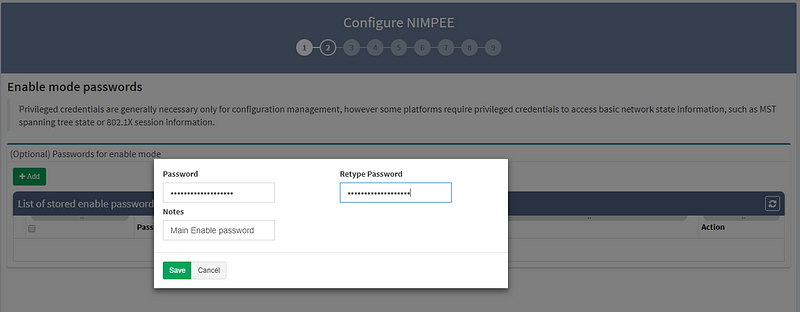
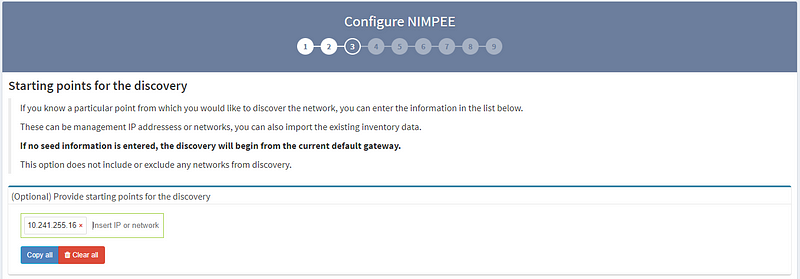
3. RECOMMENDED: Set the discovery starting point by entering the seed IP address (or addresses).
While this isn’t mandatory, we strongly recommend that you give the system at least one seed IP address to work with. Otherwise, the platform will try to discover IP networks by using traceroute over the gateway, which doesn’t necessarily produce the best results. In this example, I’ve used the management IP address of one of the routers in my virtual lab.
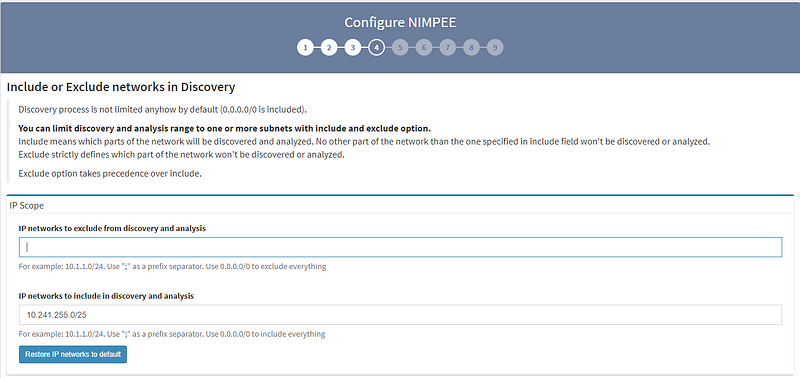
4. OPTIONAL: If you’d like, you can include/exclude networks from the discovery process. If you don’t create any predefined IP network boundaries in your discovery process, you can include any IP addresses (0.0.0.0/0).
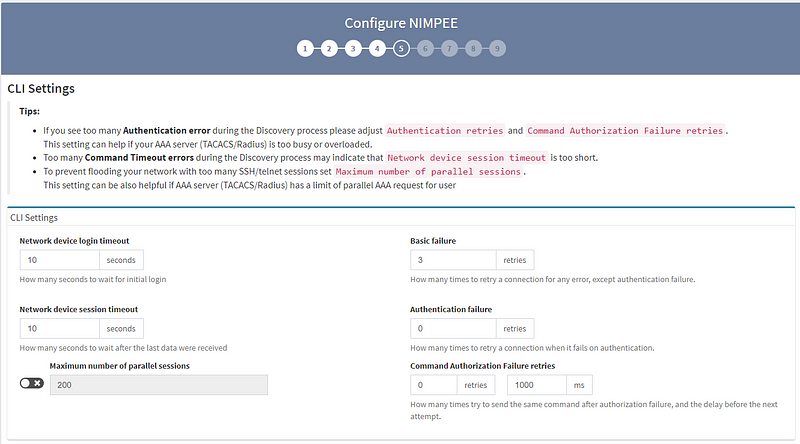
5. The Command Line Interface (CLI) settings section is mainly for fine-tuning SSH or Telnet interactions between the platform and devices. Unless you encounter a significant amount of authentication retries or other errors during the discovery process, I recommend you stick with the default settings we’ve provided. For security reasons, we also give you the option to limit the maximum number of parallel sessions.
6. The Configuration Management settings section allows you to tell the system when you’d like to collect data from network devices, either through scheduling or when triggered by an SYSLOG event.
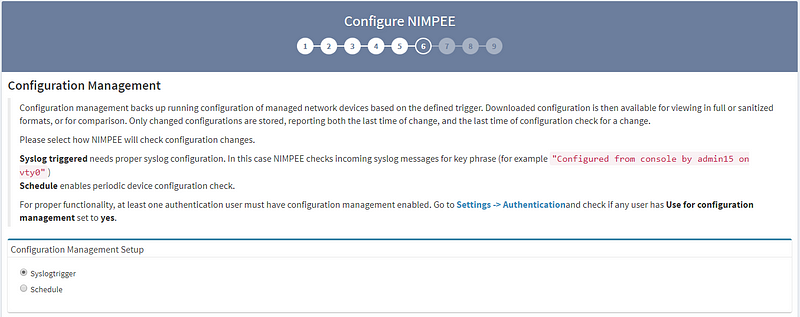
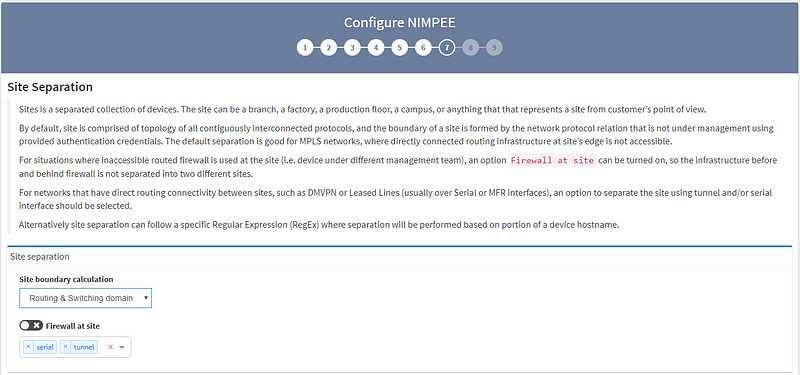
7. The Site Separation page has two boundary calculation options: the first is based on “Routing & Switching domain,” and the second is based on “Regular Expression.” (Note: the “Regular Expression” option is customizable.) I strongly recommend looking into both options to see which one best suits your needs. For this example, I’m using the “Routing & Switching domain” separation option.
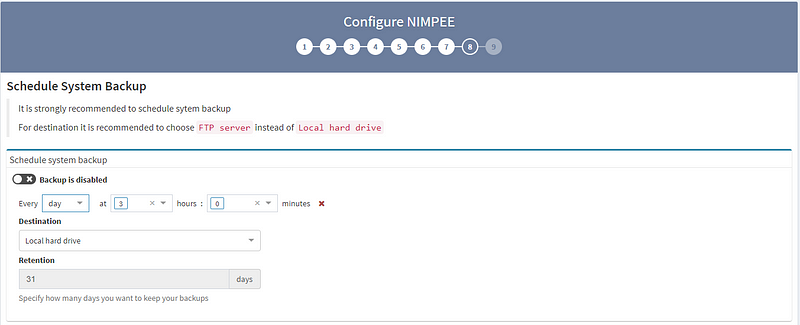
8. STRONGLY RECOMMENDED: While this step isn’t mandatory, we strongly recommend configuring automated environment backups.
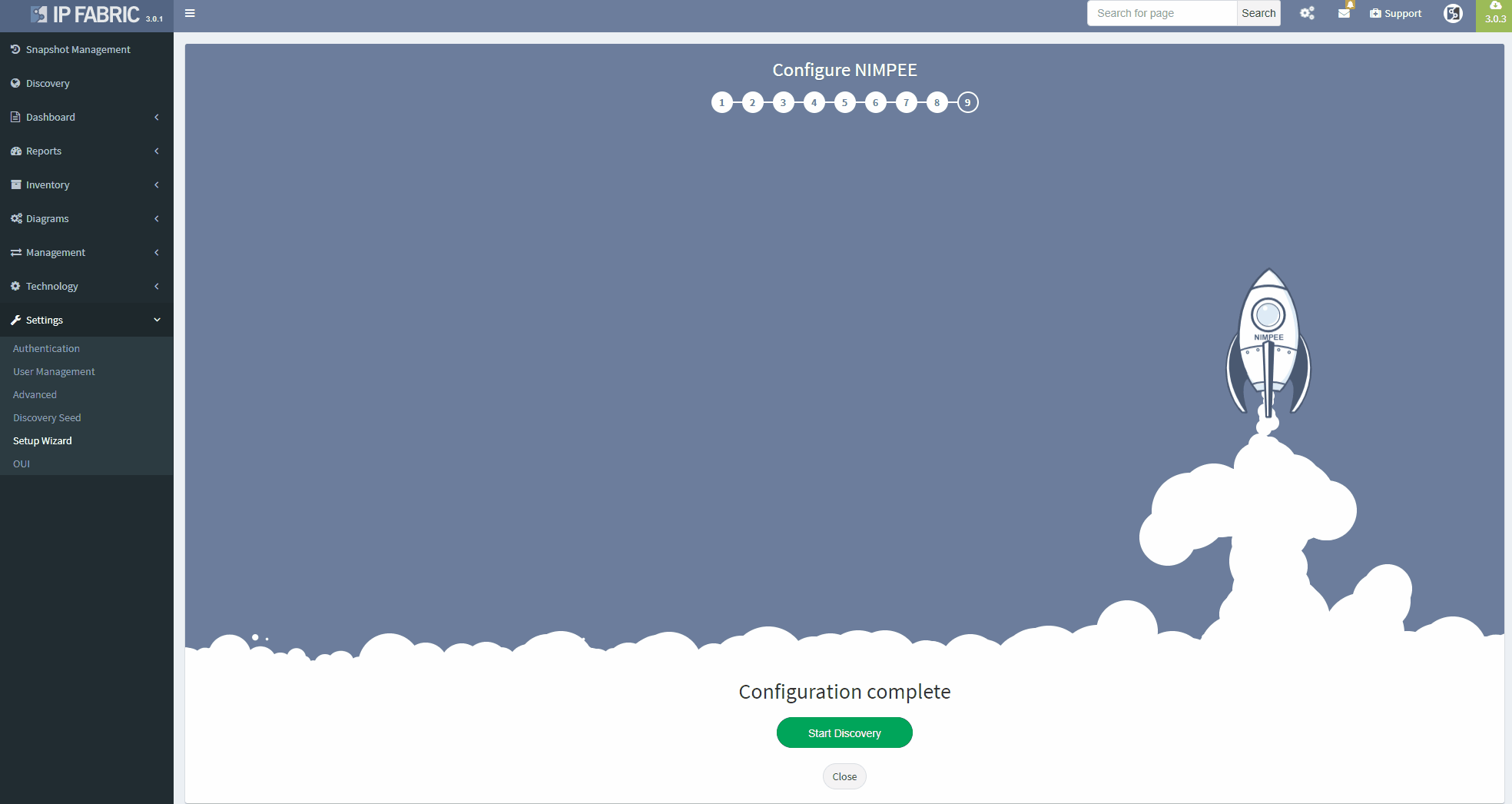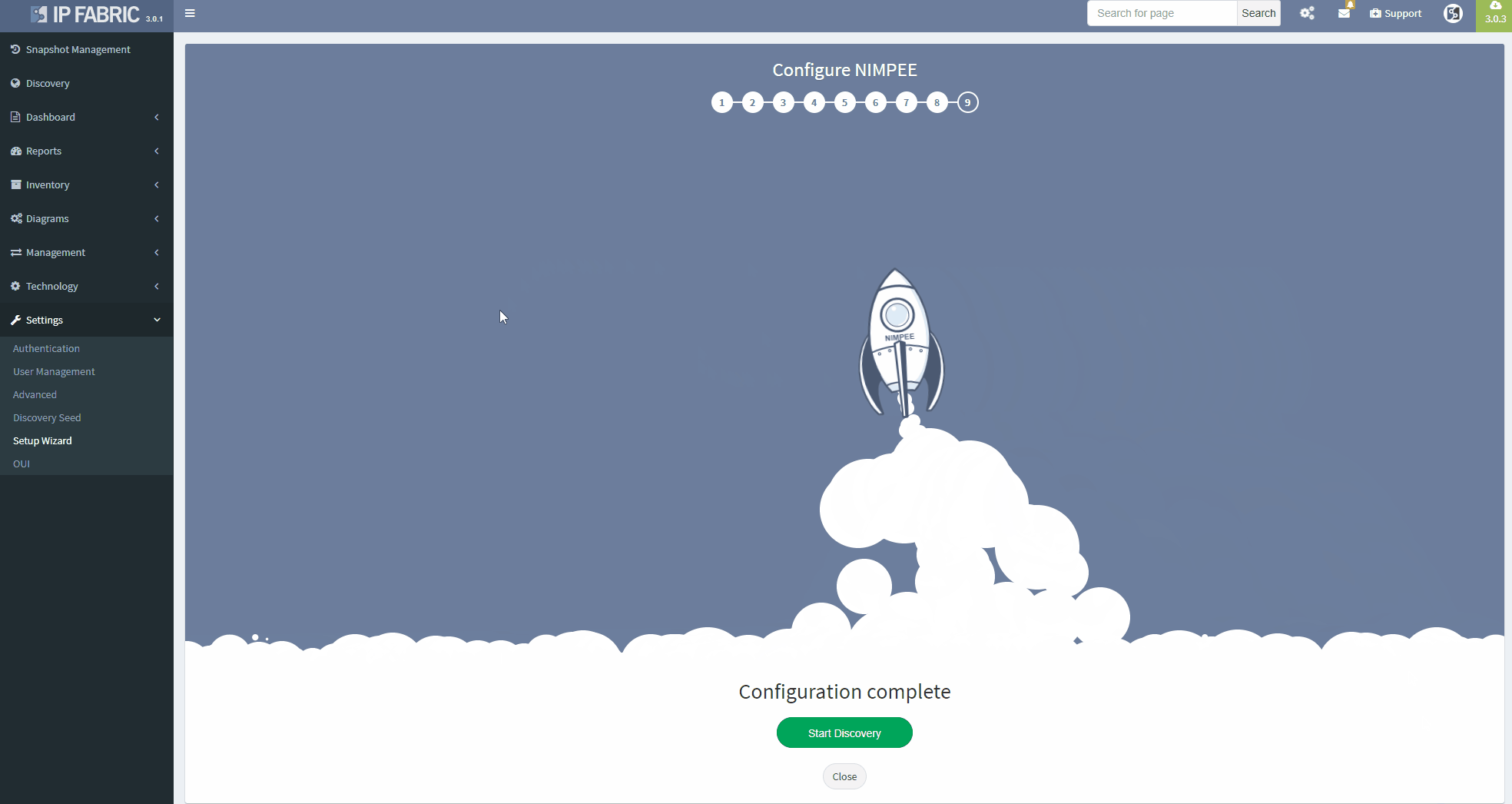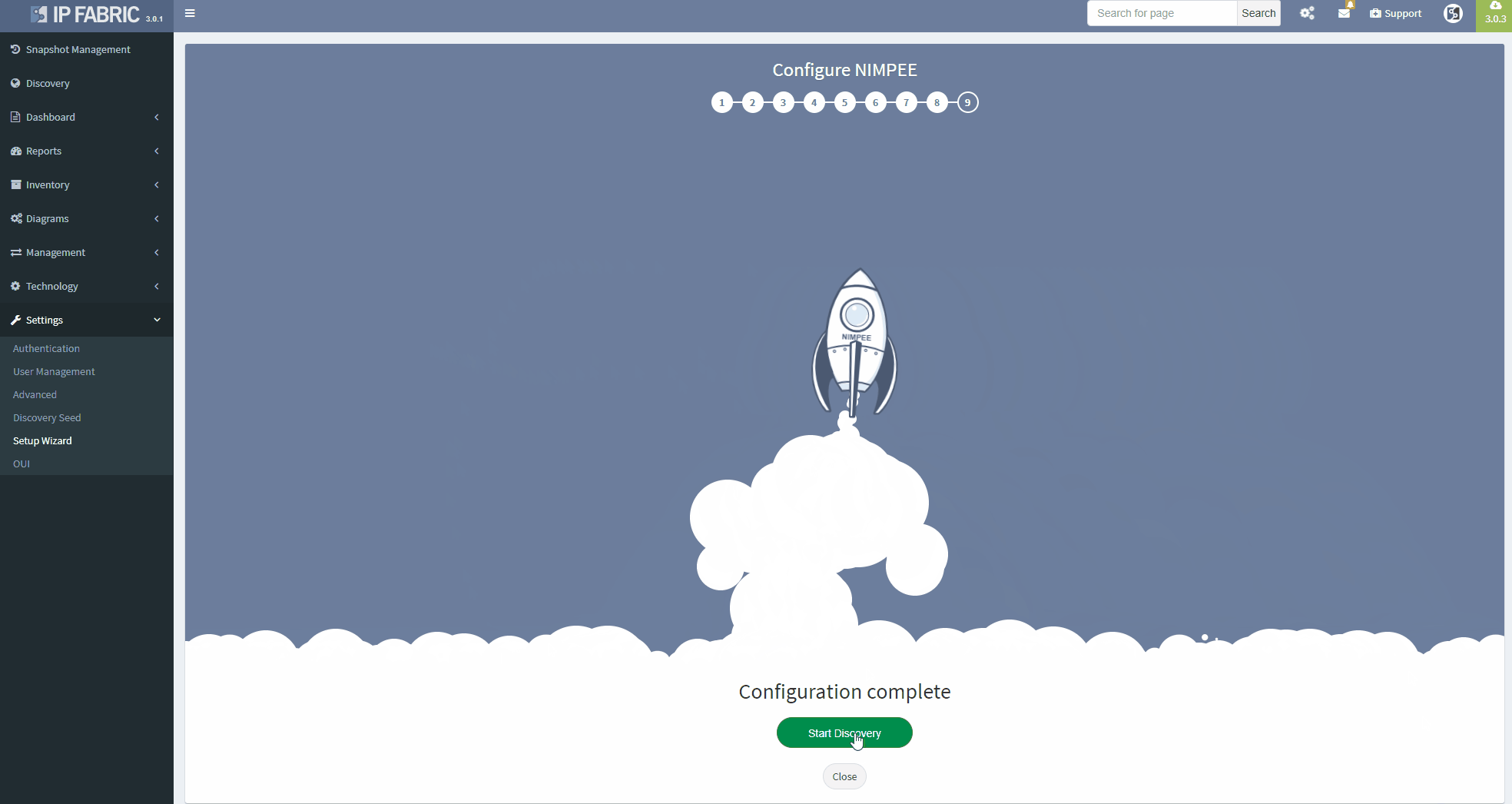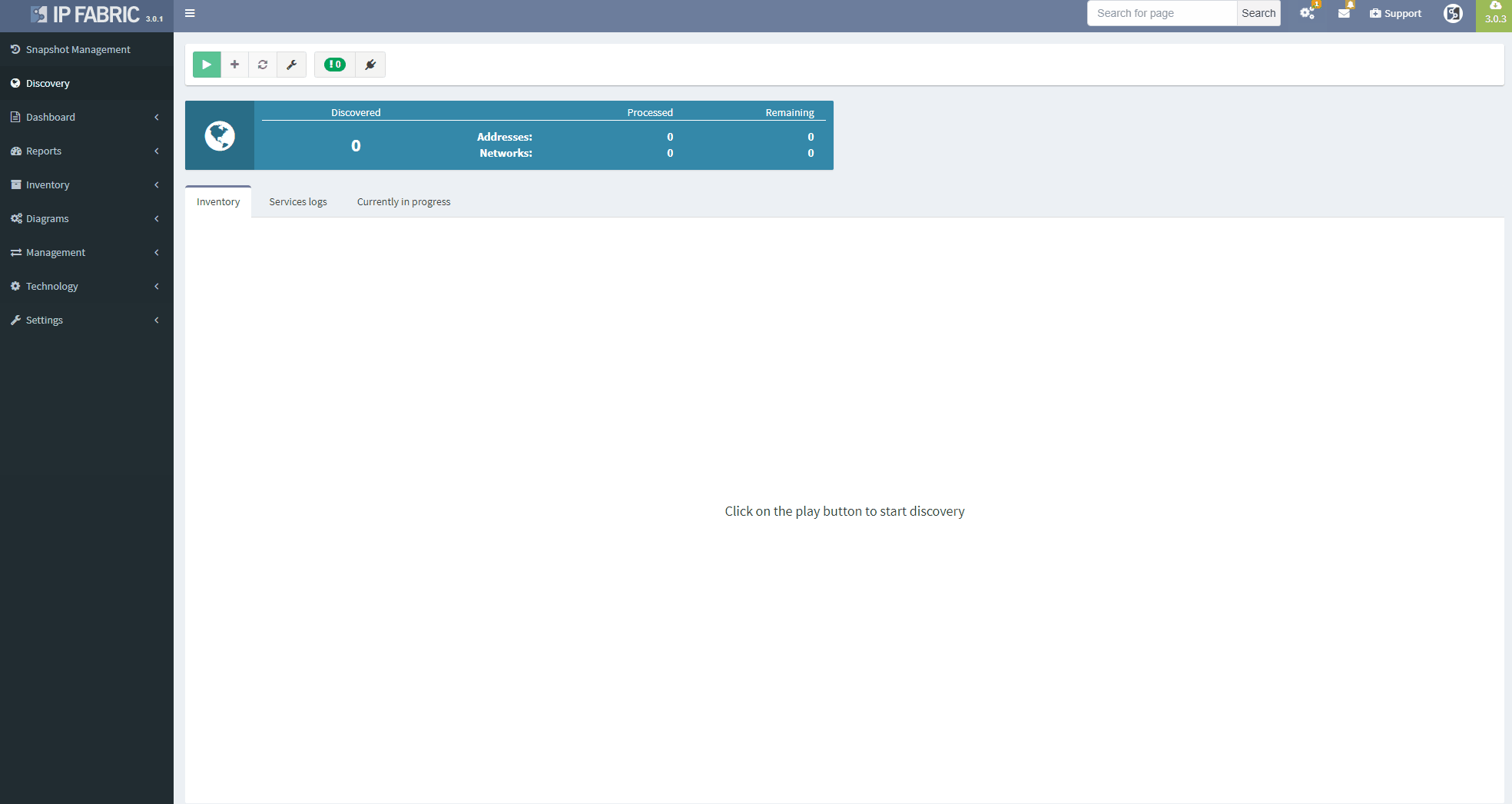
Congrats! Now that you’ve completed these steps, you’ve finished setting up your IP Fabric platform. Now, get out there and get discovering!
As the old saying goes, “the secret to getting ahead is to get started.” To help you start saving time with IP Fabric’s platform, I wanted to walk you through the initial setup process, step-by-step.
If you’re interested in learning more about how IP Fabric’s platform can help you with analytics or intended network behavior reporting, contact us through our website, request a demo, follow this blog or sign up for our webinars.
Authentication, Authorization, and Accounting, otherwise known as AAA, or Triple A.
Many individuals who have had to implement AAA on a router or a switch most likely have little knowledge regarding the commands that they copy to the router configuration. Most will simply utilize the AAA configurations from another functioning router or switch. Today, we are going to analyze the best AAA practices and how one can ensure its proper setting with our IP Fabric's platform.
For those who are working with a larger network environment, you are most likely using a form of TACACS+ or ACS server running that is specifically designed for the management of logins to your devices. AAA works in unison with TACACS+ to provide efficient management of your logins’ security. In other words, this monitors who is able to log in (Authentication), what that user can do (Authorization), as well as track the commands that are used (Accounting). In the instance of server failure or reachability issues, it is recommended to have a backup local login user name and password that will allow access to your devices.
We shall now analyze what is considered the best practices for configuration.
aaa new-modeltacacs server ACS1
address ipv4 1.1.1.1
key 0 SECRET-KEY
tacacs server ACS2
address ipv4 2.2.2.2
key 0 SECRET-KEY
aaa group server tacacs+ ACS
server name ACS1
server name ACS2aaa authentication login default group ACS local
aaa authentication enable default group ACS enable
aaa authorization config-commands
aaa authorization exec default group ACS local if-authenticated
aaa authorization commands 1 default group ACS if-authenticated
aaa authorization commands 15 default group ACS local if-authenticated
aaa accounting exec default start-stop group ACS
aaa accounting commands 1 default start-stop group ACS
aaa accounting commands 15 default start-stop group ACS
Upon dissecting this model by line, we have:
This new-model essentially turns on the AAA functionality on the network device.
This addresses the setup of the TACACS server details, such as the IP address, shared key, and all other optional details.
This is intended for the grouping of specific servers into logical groups.
Here, we define how the device is authenticating the users who attempt to log into the device. First, there is the default authentication method with group of TACACS+ servers named “ACS”. Then, if it is unreachable, we shall implement the locally configured user account list.
This component explains that, for enable mode, the default authentication method with group of TACACS+ servers named “ACS” should be utilized.
This is regarding our goal to authorize each command that is being issued to the device.
This sets up the device and places the user directly into enable mode, upon his authentication (the if-authenticated keyword).
In this command, we are authorizing the level 1 user commands, which is similar to the non-enable mode.
Here, we are providing authorization for level 15 users against TACACS+. If TACACS+ is unavailable, then the local user account is used, instead. Upon authentication, the user will immediately be placed into exec/enable mode.
AAA Accounting ensures the logging in and access into the device.
This provides the tracking of user activity on a given device for privilege 1 commands.
This provides the tracking of user activity on a given device for privilege 15 commands.
This provides tracking of user activity on a device, even if they have just logged in.
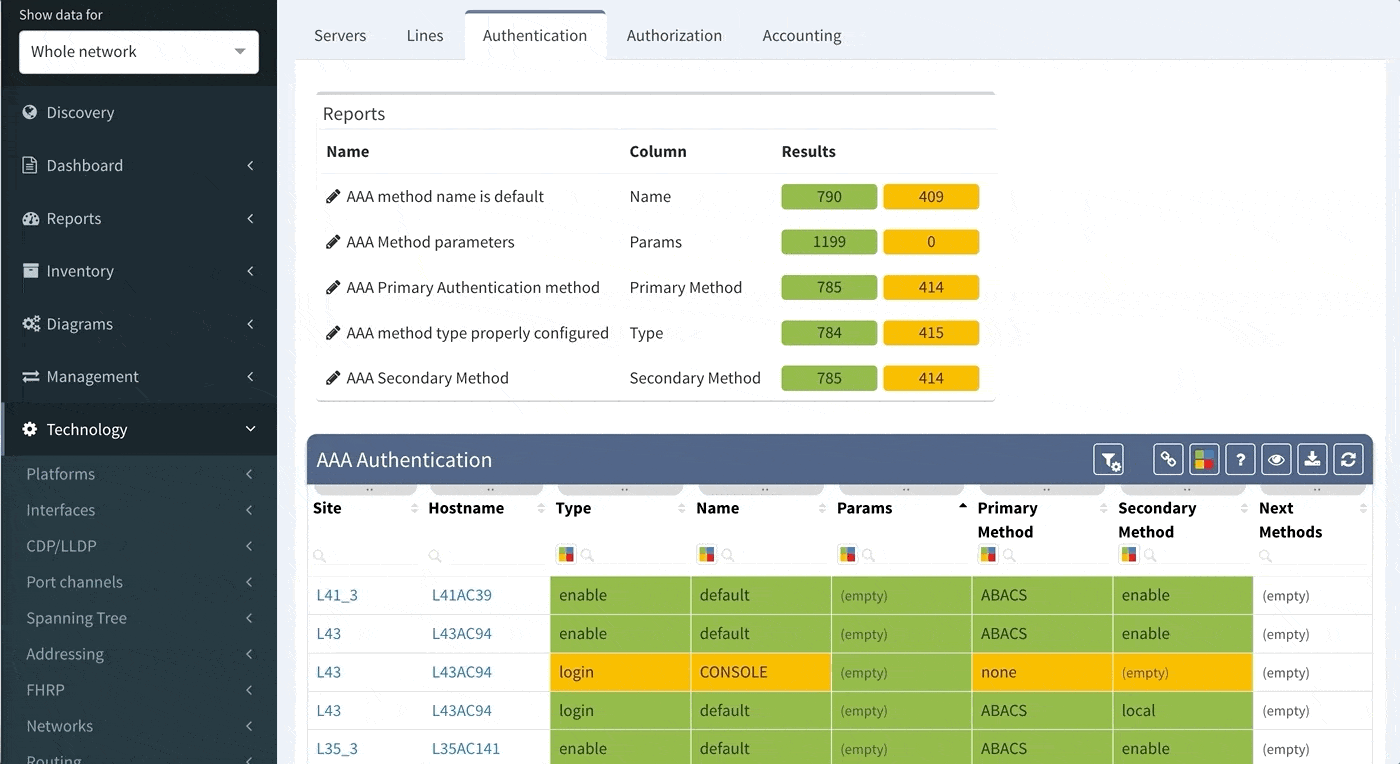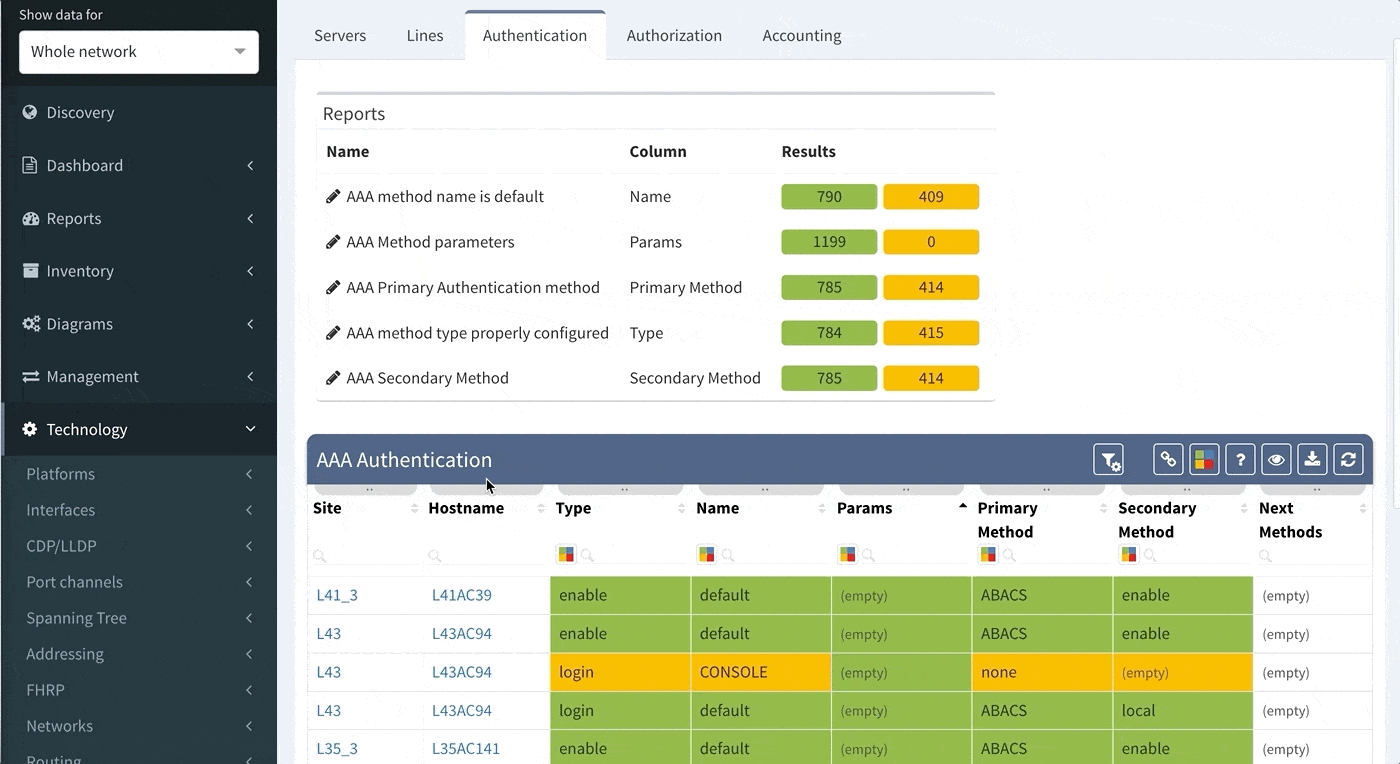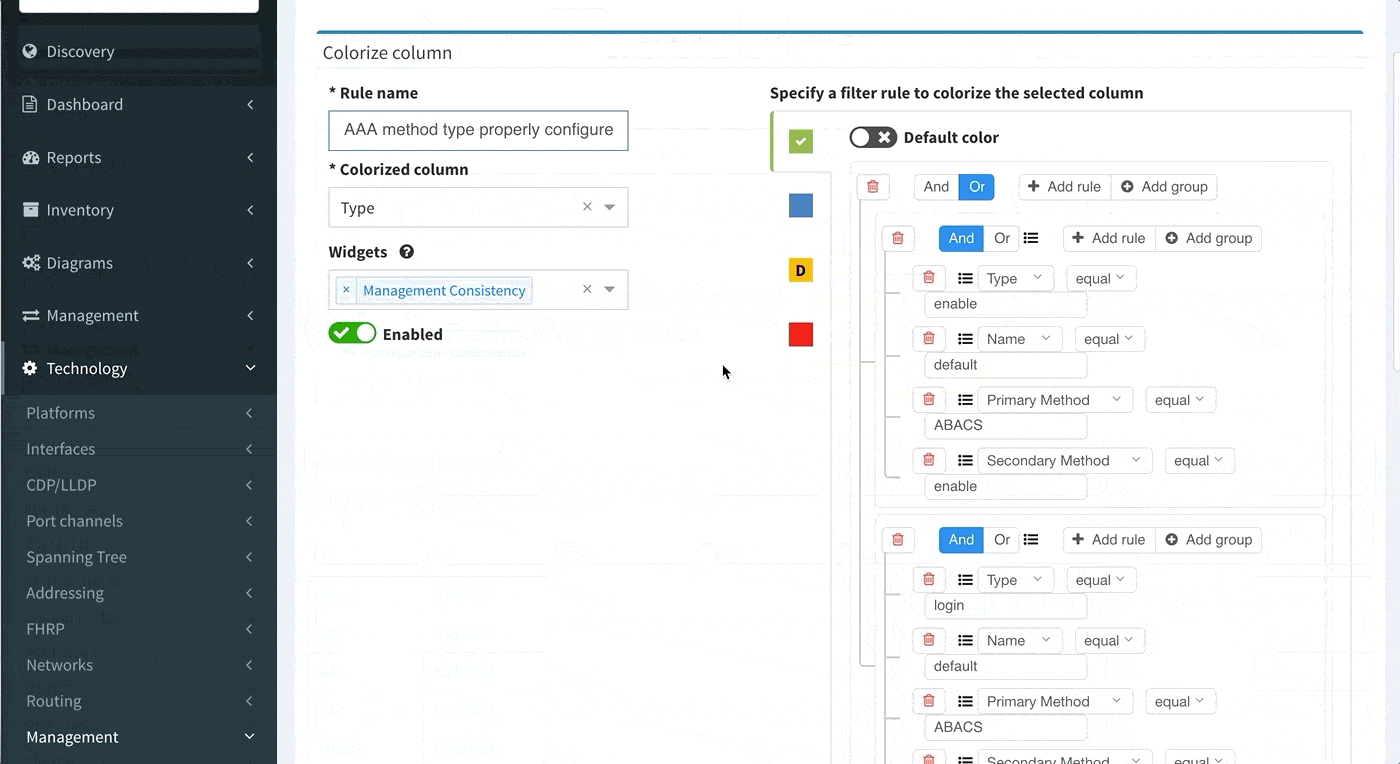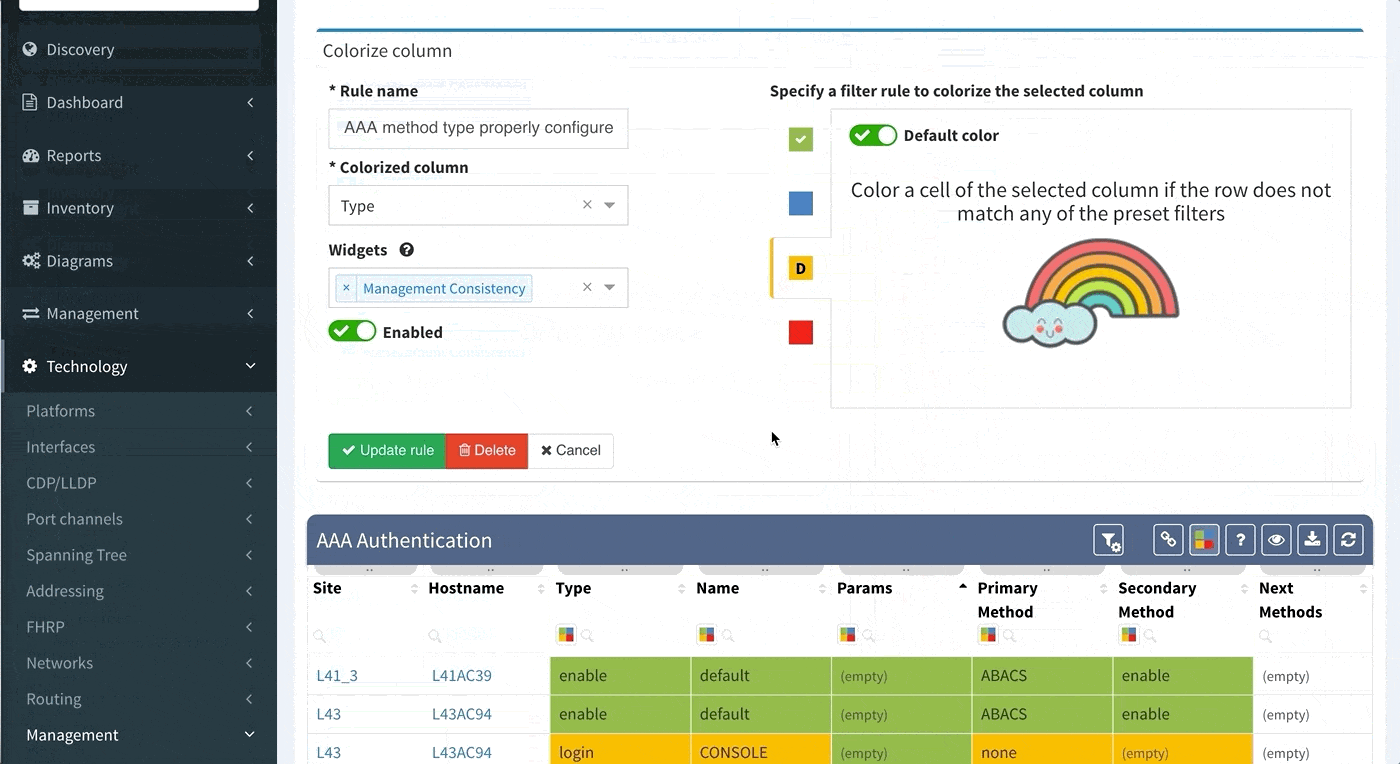
As you can see from this basic configuration, there is significant variability, resulting in complications of the verification of the proper function. This worsens with regular network operations, when the connectivity to the TACACS server fails, requiring a troubleshoot to determine the error. In such a situation, one would usually remove the TACACS configuration in attempt to resolve the issue. However, during the troubleshoot, it is common to forget about this change and leave the network open with local authentication or, perhaps, no authentication, whatsoever. Luckily, IP Fabric offers the newly released AAA verification, which can be used for the verification of the real live AAA settings.
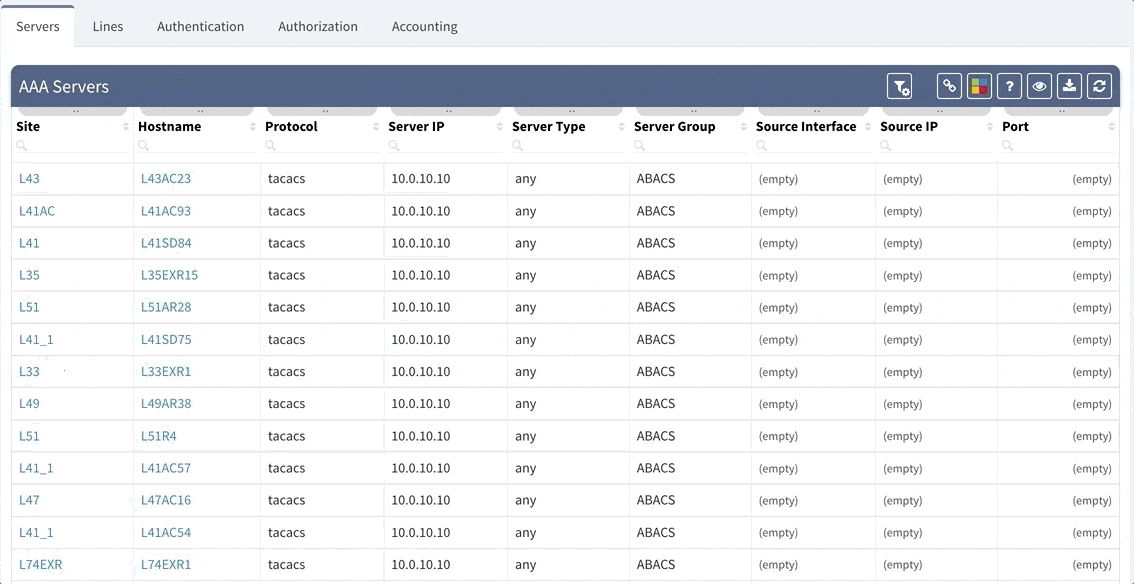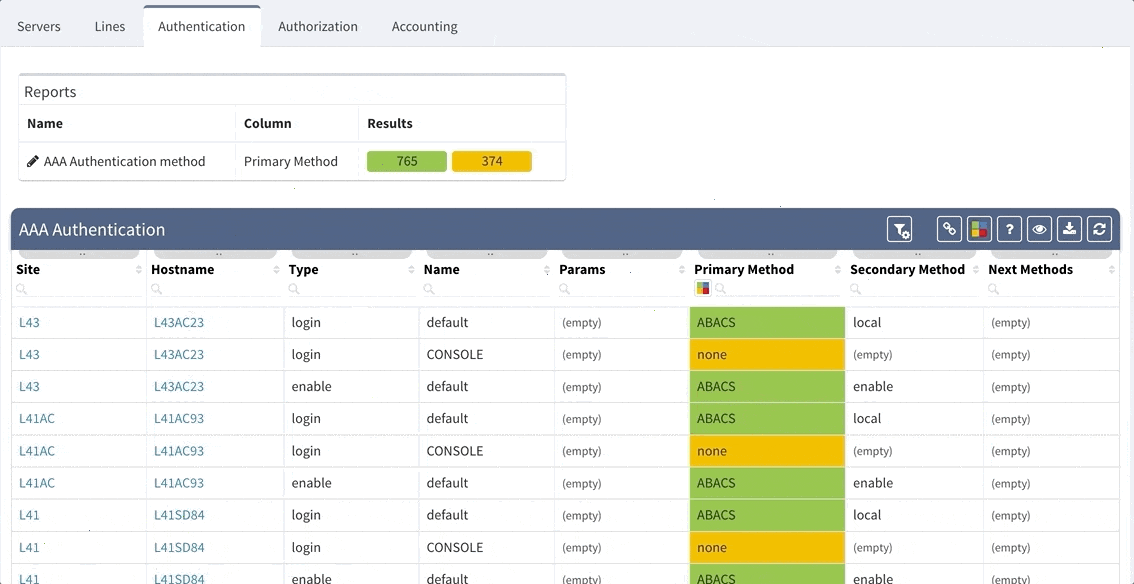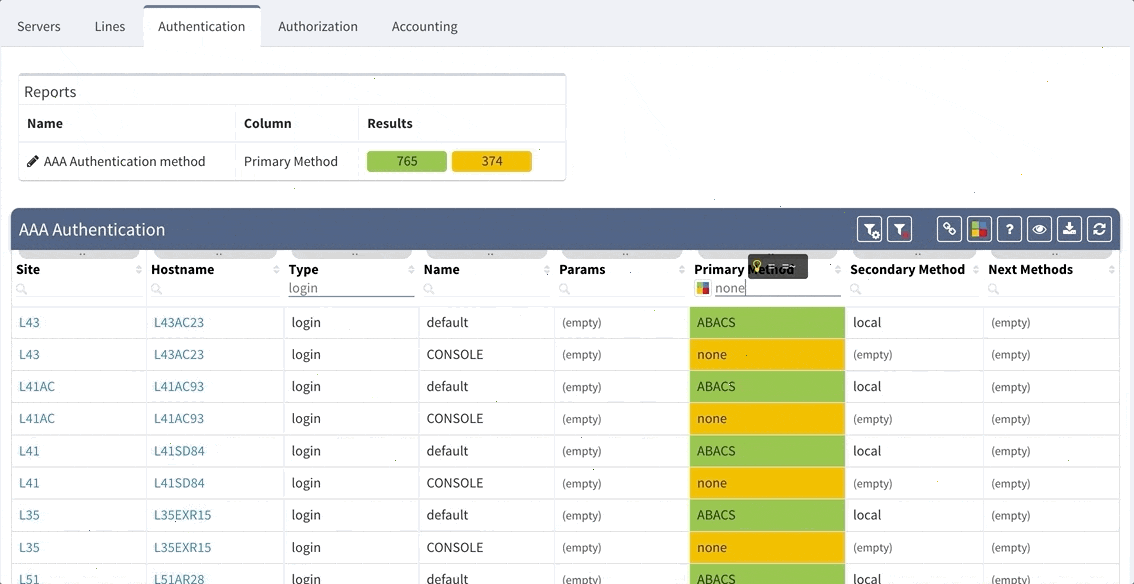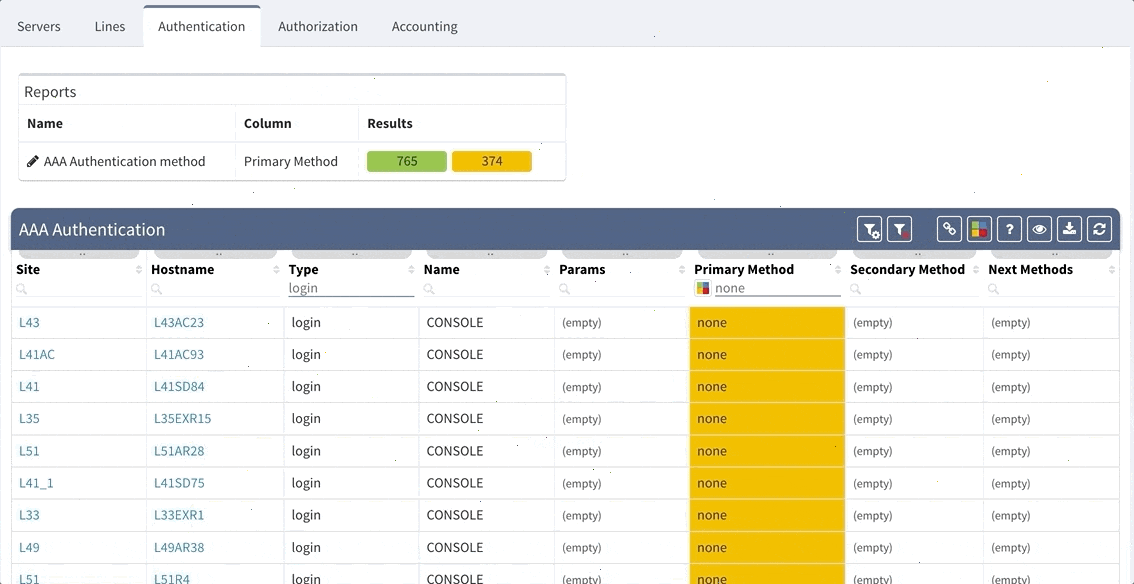
Although our platform includes a few “out of the box” reports, we highly recommend adjusting these default reports in color with your custom verification checks, since the AAA settings differ between various companies. We recommend that you observe and spend time on the following:
For example, let us assume that we want to set up the verification report for the Authentication methods to verify this:
which would be equivalent of the following piece of configuration
aaa authentication login default group ABACS localaaa authentication enable default group ABACS enableIt is generally recommended to have a single detection for all issues on the particular AAA method and to reveal the issue count on the dashboard.
This can be configured in the following manner:
For a more detailed overview of how to set this up, view the video below:
Proceed to colorize the columns with specific details to green or orange, so that you will immediately see what is wrong from the dashboard counter created previously. In our case, we would need to setup additional rules as follows:
AAA Authentication Secondary method would look like this:
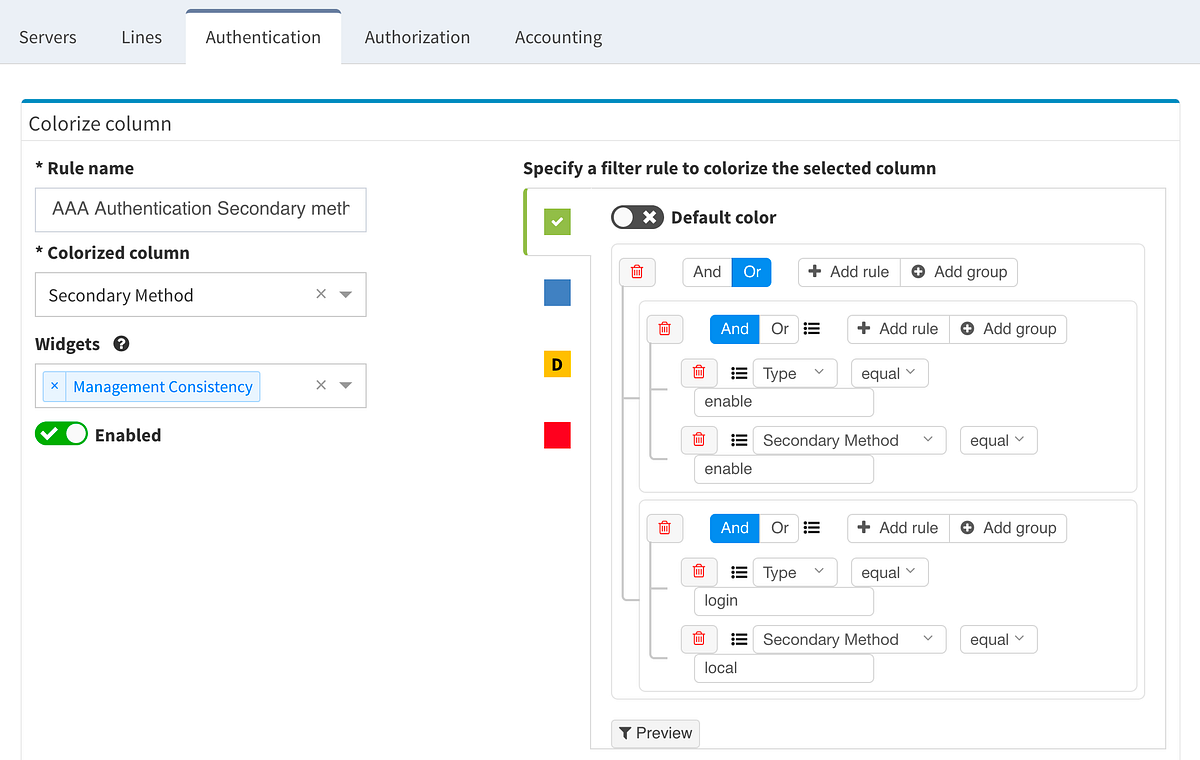
This will ensure the setup of the Authentication on all devices in the network. In regards to the remaining tabs (servers, lines, authorization, and accounting), you may follow the same logic to create similar specific rules that will configure IP Fabric to verify your specific AAA needs consistently in a matter of seconds.
If you’re interested in learning more about how IP Fabric’s platform can help you with analytics or intended network behavior reporting, contact us through our website, request a demo, follow this blog or sign up for our webinars.
Juniper SRX is a wonderful firewall device with a lot of rich features. However sometimes the complexity of security policies may grow greatly with multiple embedded addresses or application objects, more virtual routing and forwarding instances, route leaks and so on. It can come to a point when managing all security rules and providing service to multiple clients for datacenter or other infrastructure at the same time, can become very cumbersome. The fastest and most secure interaction with the firewall so far is still the command line interface. This exact area is one of the strongest and most versatile, when it comes to Juniper boxes. If you are an experienced tech, you may be able to interact with the SRX swiftly and easily. Moreover, narrow down any critical information related to troubleshooted issue, but It’s not so simple with security rules export.
but It’s not so simple with security rules export.
To be able to successfully export security policies from SRX, we have handful of options. The very easy one is to export configuration between certain security zones to a file. Furthermore, upload to a server or send to a customer. But it could be time-consuming for a non-Juniper technicians or managers to be able to comprehend all the information.
Another option would be buying Junos Space software with Security Director plugin. It's a specialized administration and orchestration tool made by Juniper, which can be easily installed in the cloud. It’s a great all in one tool for almost any Juniper device. In Security Director, security policy exports can be filtered appropriately. However, the only format options are PDF or the ZIP file and only Juniper firewalls are supported.
Or we could develop any customized script using Junos PyEZ library and export policies to multiple file formats. A little bit of coding never hurts anyone and it’s fun. Nonetheless, it needs to be maintained and updated in time. Further, you would be still interacting with command line interface, if there would not be any front end supporting the script itself.
Or there’s one more option that is available since IP Fabric version 2.2.4 was released (the most current one is 2.2.5). After successful discovery of any Juniper SRX with security policies by IP Fabric, you are just few clicks away from full-fledged policies export. It’s simple as that.
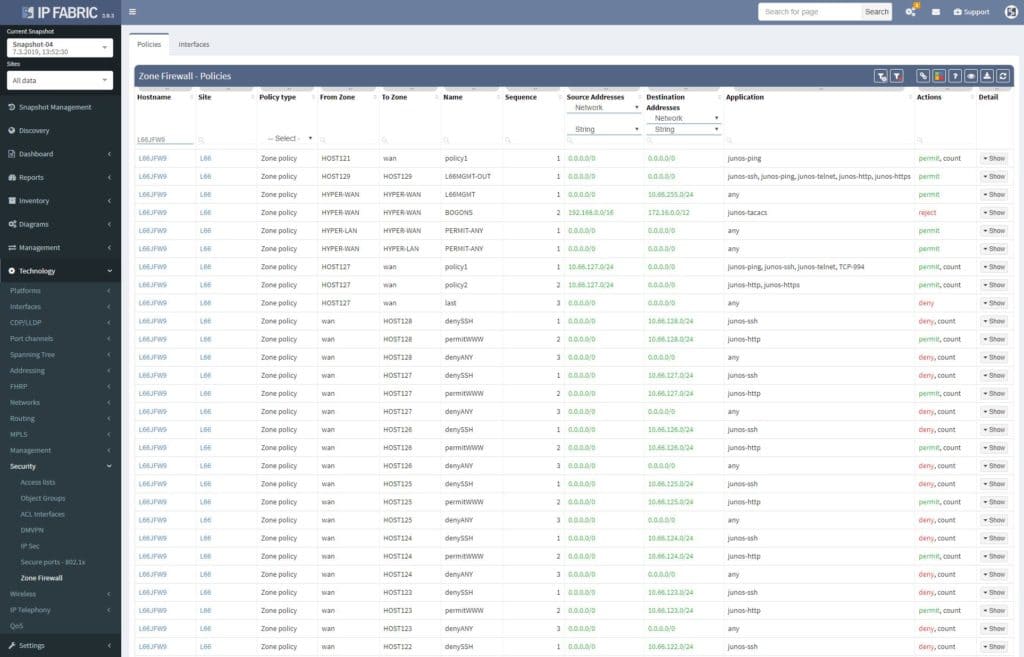
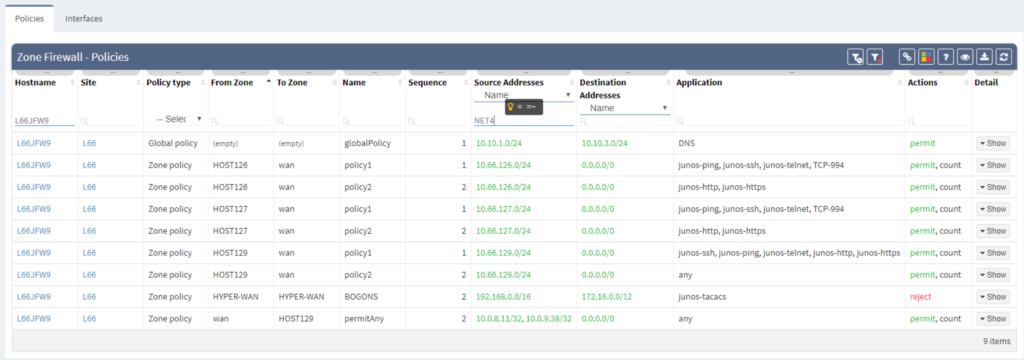
When opened in browser, the Zone Firewall related information can be navigated via Technology > Security. The default view is fully customizable, including colorizing columns, advanced filters and more. There’s a lot that has been done when it comes to custom tables and views recently.
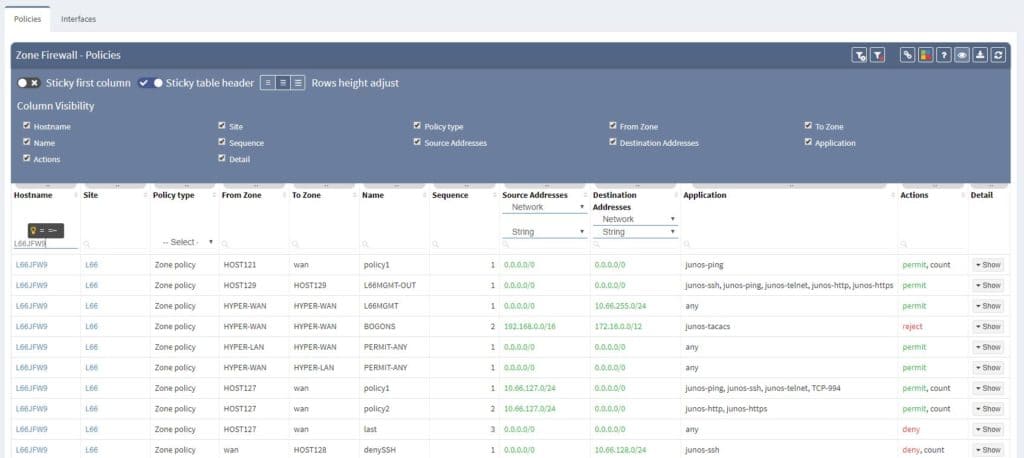
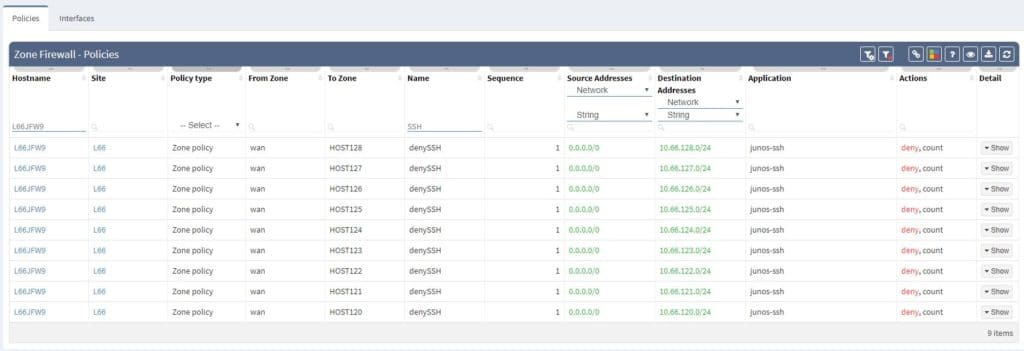
Single security policies can be furthermore unwrapped with address and application objects being resolved. IP Fabric understands even Junos default applications configured object and application sets, all well prepared for end-to-end path resolution via SRX, which is another stunning feature described in another article.
Filtering is supported with regex capabilities and its fast interface provides seamless experience to any security administrator or technical manager. Any filtered information can be exported to CSV format and downloaded.
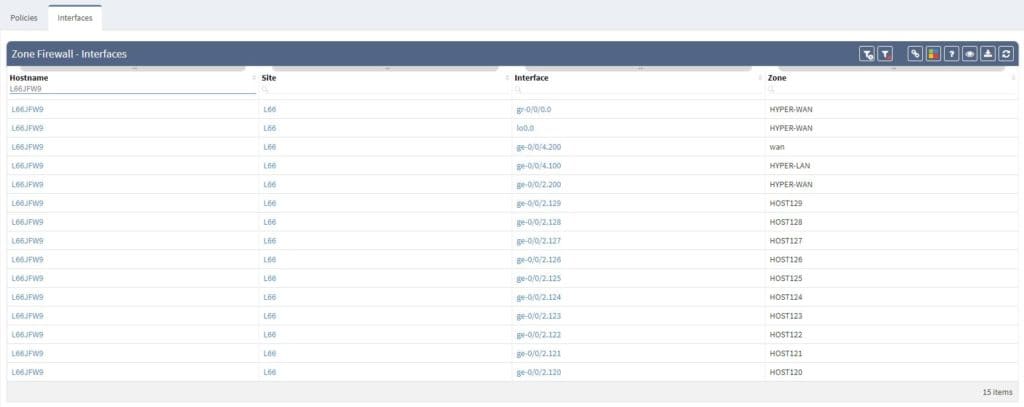
Another very handy feature is matching the security zones with its related interfaces. We need to simply navigate to Interfaces view when in Zone Firewall section and all information is available at hand, all can be exported as well. It’s all in one, easy to navigate and very fast to interact with.
If you’re interested in learning more about how IP Fabric’s platform can help you with analytics or intended network behavior reporting, contact us through our website, request a demo, follow this blog or sign up for our webinars.


