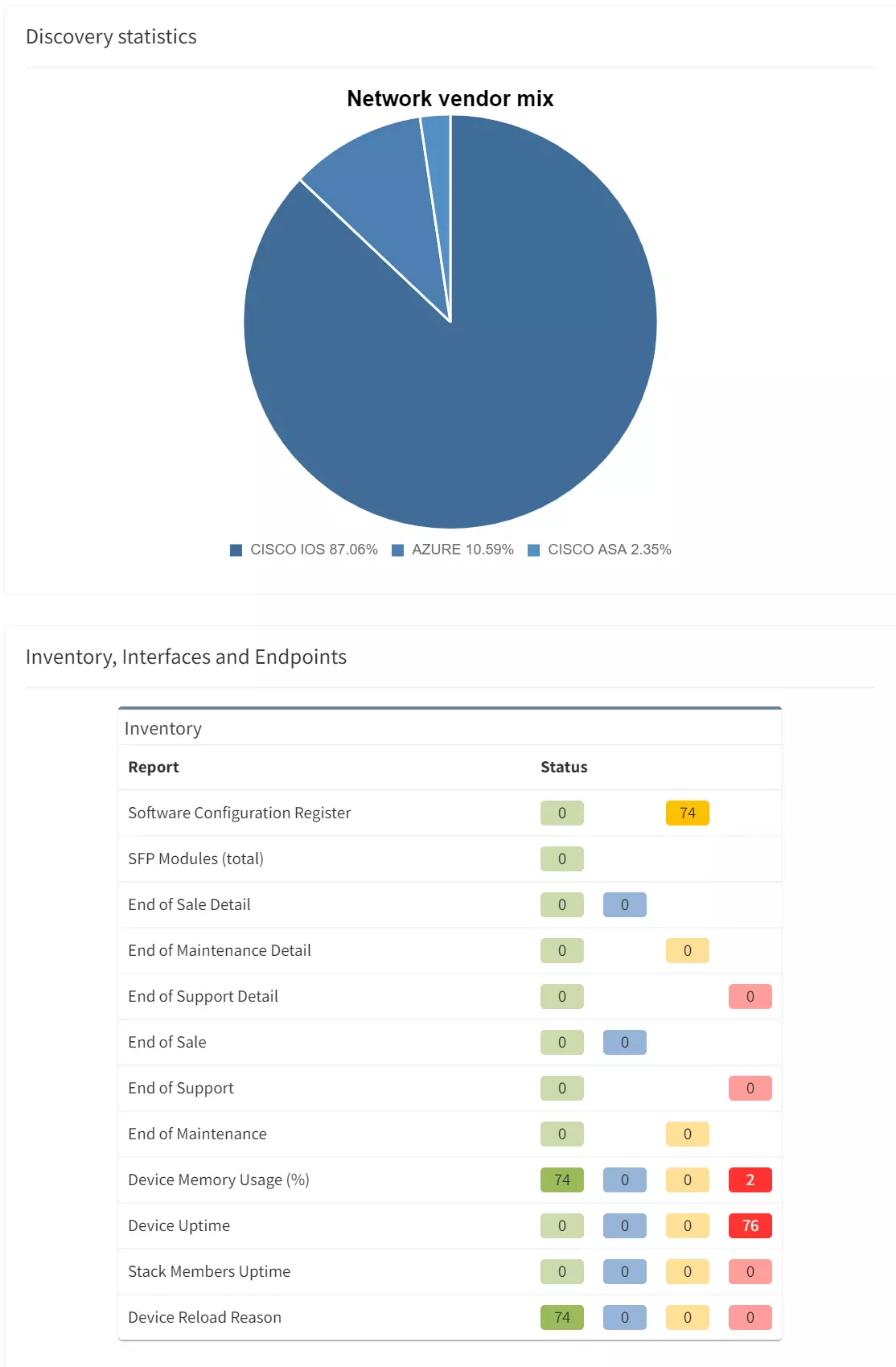
IP Fabric's Automated Network Assurance Platform is built to ensure your network remains up, stable, and secure, and that includes providing proactive notification of issues before they arise.
Our comprehensive model of your network gives you a holistic understanding of your cybersecurity attack surface, and the risks associated with it. This includes being able to identify known vulnerabilities in your network infrastructure, notified through NIST's multi-vendor CVE - Common Vulnerability and Exposures Program.
This command injection vulnerability, announced on 12th April 2024, specifically targets the GlobalProtect features of Palo Alto Networks firewalls. The vulnerability allows an unauthenticated attacker to execute arbitrary code on the appliance with root privilege. As such, it is classed as a Critical Vulnerability and needs to be resolved immediately. But how do you know if your security infrastructure is vulnerable to an exploit?
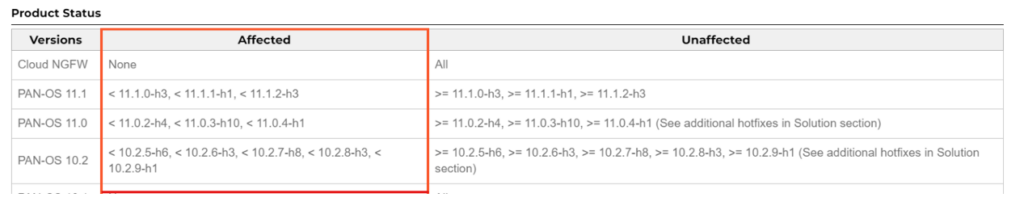
1. Your Palo Alto Networks firewalls will be running versions of PAN-OS 11.1, 11.0 or 10.2 shown below.
2. You will have GlobalProtect gateway or GlobalProtect portal configured on one or more interface.
Our Solution Architects have built a tool called PyNetCheck that allows our customers to quickly identify which Palo Alto appliances in their network are running the impacted versions of the PAN-OS and have Global Protect configured. It allows IP Fabric customers to programmatically define automated checks of inventory, configurations, interconnections within the network. The checks can also embed external data.
The publicly released PyNetCheck project contains sample tests and checks including those for specific critical CVEs, and because we have the data in the IP Fabric platform relating to configuration and code versions, we have updated PyNetCheck to specifically report on the presence of conditions for CVE-2024-3400 in your Palo Alto Networks security appliances.
We are reaching out to customers we know to have the affected versions in their networks.
If you are an IP Fabric customer and would like to know more, speak with your Customer Success Manager or Solution Architect for more details. And if you are not yet a customer and would like to find out more about how we can help, contact us at [email protected]!
Interested in finding out more about IP Fabric? Try our free, self-guided demo.
IP Fabric's Automated Network Assurance Platform is built to ensure your network remains up, stable, and secure, and that includes providing proactive notification of issues before they arise.
Our comprehensive model of your network gives you a holistic understanding of your cybersecurity attack surface, and the risks associated with it. This includes being able to identify known vulnerabilities in your network infrastructure, notified through NIST's multi-vendor CVE - Common Vulnerability and Exposures Program.
This command injection vulnerability, announced on 12th April 2024, specifically targets the GlobalProtect features of Palo Alto Networks firewalls. The vulnerability allows an unauthenticated attacker to execute arbitrary code on the appliance with root privilege. As such, it is classed as a Critical Vulnerability and needs to be resolved immediately. But how do you know if your security infrastructure is vulnerable to an exploit?
1. Your Palo Alto Networks firewalls will be running versions of PAN-OS 11.1, 11.0 or 10.2 shown below.

2. You will have GlobalProtect gateway or GlobalProtect portal configured on one or more interface.
Our Solution Architects have built a tool called PyNetCheck that allows our customers to quickly identify which Palo Alto appliances in their network are running the impacted versions of the PAN-OS and have Global Protect configured. It allows IP Fabric customers to programmatically define automated checks of inventory, configurations, interconnections within the network. The checks can also embed external data.
The publicly released PyNetCheck project contains sample tests and checks including those for specific critical CVEs, and because we have the data in the IP Fabric platform relating to configuration and code versions, we have updated PyNetCheck to specifically report on the presence of conditions for CVE-2024-3400 in your Palo Alto Networks security appliances.
We are reaching out to customers we know to have the affected versions in their networks.
If you are an IP Fabric customer and would like to know more, speak with your Customer Success Manager or Solution Architect for more details. And if you are not yet a customer and would like to find out more about how we can help, contact us at [email protected]!
Interested in finding out more about IP Fabric? Try our free, self-guided demo.