As methods of attack become more sophisticated, and as our networks grow ever larger, the number of reports in recent years regarding the staggering increase in cybercrimes has increased manifold. According to IBM, the average total cost of single data breach cost an organization approximately $3.86 million in 2020. In 2021, this increased to $4.24 million. 2022? Up to $4.35 million. A 12.7% increase in just two years.
As we've touched upon in previous posts, simply implementing sufficient firewall protection in network endpoints just doesn't cut it. You need to proactively and consistently ensure that your network security is up to snuff. With this in mind, let's take a look at some of the most common forms of cybercrimes, and see how IP Fabric can help you to proactively decrease the risk of becoming another cybercrime statistic.
Malware that blocks access to data/devices, and threatens to keep it locked unless a random is paid. Common methods of infiltration include social engineering attacks (e.g.) phishing emails, and through vulnerabilities in operating systems and software. Phishing attacks typically affect the 6th OSI layer.
DDoS disrupts traffic (from servers, services, or networks), by jamming the target with internet traffic to overwhelm it. Essentially, DDoS attacks attempt to paralyze a network and cause downtime, which can be particularly damaging for e-commerce sites. According to Kaspersky, 50% of DDoS attacks lead to service disruption, with 24% rendering services completely unavailable. These attacks typically affect the 4th OSI layer.
APTs are covert cyber-attacks where the attacker goes unnoticed whilst gaining and maintaining unauthorized access to a target network. The attacker typically remains undetected for a lengthy period of time while intercepting and relaying sensitive data. Intercepted information is used to cause outages, instigate DDoS attacks, or spread malware.
Trojans are a malware that disguise themselves as legitimate programs that, once run by unsuspecting users, use malicious code to gain access to target systems.
The final threat here is one that we pose to ourselves. When managing networks, there are often many things to manually maintain. Such a monumental task can lead to oversights and misconfigurations (e.g.) broken ACLs or outdated components and software, which make life easier for would-be hackers to manifest their nefarious intentions.

IP Fabric is not a dedicated security solution and doesn't fulfil the same functions as, say, an NSPM solution. From a security perspective, what IP Fabric can do is provide key visibility of the necessary components in your environments - giving you the necessary assurance that you have the relevant precautions in place to prevent your network falling victim to a cybercrime.
Useful for: Ransomware, DDoS, APT, Trojan Horses
Segmentation is used to prevent the spread of malware to certain parts of your network and ensure affected areas are sufficiently isolated. Even if an area of your network does become affected, the chances of it spreading and causing further issues to your network are limited.
IP Fabric itself doesn't provide segmentation. Instead, it can be used to visualize existing segmentation in your network, and whether this is sufficiently hardened. Based on this visualization, you can answer some essential questions: Does the segmentation prevent lateral movement? Is it properly configured?
All of these answers let you decide whether your endpoints are adequately protected against spreading malware in case an attack occurs.

Useful for: APT, Trojan Horses
Network Security Policy Management (NSPM) platforms help you ensure that your policies are properly defined and ideally placed to spread infection throughout your environments. Ensuring that the policies you are deploying are fit for purpose is critical to preventing attacks from having a lasting effect.
The problem with NSPMs? They have limited vendor support and only provide visibility from OSI layer 3. IP Fabric's network assurance provides full and up to date visibility of your entire network infrastructure to ensure that there are no blind spots left unnoticed. Check out our piece on the relationship between NSPM platforms and network assurance here for more information.
Useful for: Ransomware, DDoS, APT, Trojan Horses
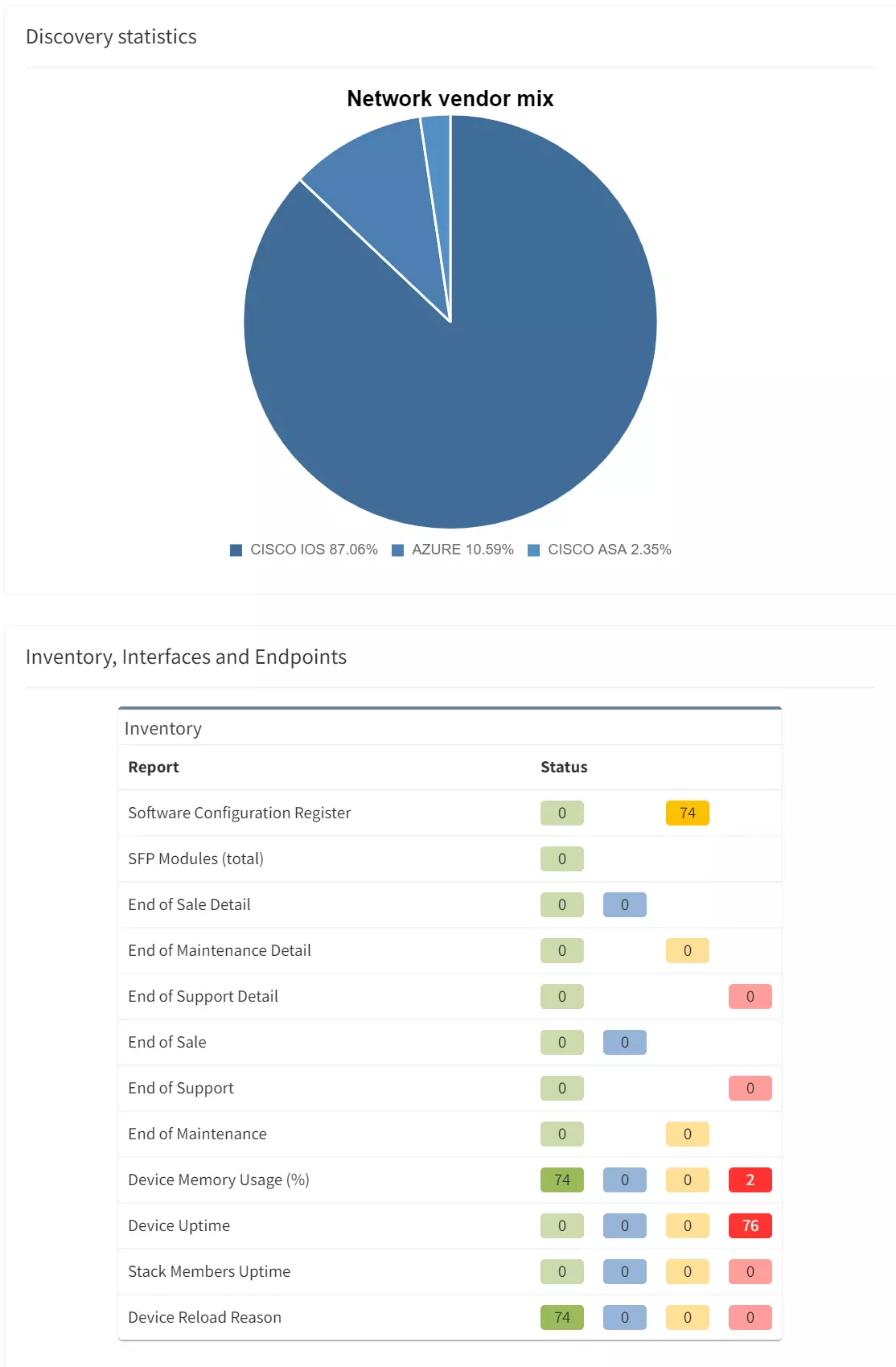
IP Fabric can be used to provide a complete inventory of hardware, software, and configurations within your network, including EoL information that can be used to ensure your protective software remains up-to-date. Doing so provides you with the confirmation that your components aren't leaving vulnerabilities for attackers to exploit.
Whenever components are nearing EoL, IP Fabric presents information on vendor-suggested replacement for said components, so that necessary steps can be taken to ensure no gaps are left for attackers.
Useful for: APT
APTs are typically detected due to unusual activity being discovered within the affected parts of the network.
By establishing complete visibility of your network through rapid CLI-based discovery via API, SSH or Telnet, which is kept up-to-date with regular snapshots (scheduled or ad-hoc), network teams can model forwarding and policy behavior within a network using captured configuration and device state data.
Using this data, teams can examine network behavior and forwarding policies to determine the presence of unusual activity that would typically be associated with APTs and act accordingly.
The best way to ensure network security is to make sure that everyone within an organization receives the necessary information on cyberthreats to mitigate risk. After all, a disciplined organization-wide security posture is a best practice.
But nasty things can still happen, and it only takes a second, or one error in judgment, for an attacker to gain access to a network.
With IP Fabric in place, however, networking teams can more proactively address misconfigurations that may threaten network security, ensure policies are uniformly applied, and make sure that any areas of the network housing critical data are appropriately segmented.
Arming your teams with the appropriate visibility and assurance will go a long way to preventing something happening to your organization.
Check out our glassboard video below, in which Christian Giebner highlights the key ways in which IP Fabric can help to bolster your network security efforts and ensure you aren't left with any nasty surprises lurking in the shadows (Note: This video is in the German language, with English subtitles available).
Want to test out IP Fabric for yourself? Try our free, self-guided demo here.
Make sure to follow us on LinkedIn, and on our blog, where we regularly publish new content!
As methods of attack become more sophisticated, and as our networks grow ever larger, the number of reports in recent years regarding the staggering increase in cybercrimes has increased manifold. According to IBM, the average total cost of single data breach cost an organization approximately $3.86 million in 2020. In 2021, this increased to $4.24 million. 2022? Up to $4.35 million. A 12.7% increase in just two years.
As we've touched upon in previous posts, simply implementing sufficient firewall protection in network endpoints just doesn't cut it. You need to proactively and consistently ensure that your network security is up to snuff. With this in mind, let's take a look at some of the most common forms of cybercrimes, and see how IP Fabric can help you to proactively decrease the risk of becoming another cybercrime statistic.
Malware that blocks access to data/devices, and threatens to keep it locked unless a random is paid. Common methods of infiltration include social engineering attacks (e.g.) phishing emails, and through vulnerabilities in operating systems and software. Phishing attacks typically affect the 6th OSI layer.
DDoS disrupts traffic (from servers, services, or networks), by jamming the target with internet traffic to overwhelm it. Essentially, DDoS attacks attempt to paralyze a network and cause downtime, which can be particularly damaging for e-commerce sites. According to Kaspersky, 50% of DDoS attacks lead to service disruption, with 24% rendering services completely unavailable. These attacks typically affect the 4th OSI layer.
APTs are covert cyber-attacks where the attacker goes unnoticed whilst gaining and maintaining unauthorized access to a target network. The attacker typically remains undetected for a lengthy period of time while intercepting and relaying sensitive data. Intercepted information is used to cause outages, instigate DDoS attacks, or spread malware.
Trojans are a malware that disguise themselves as legitimate programs that, once run by unsuspecting users, use malicious code to gain access to target systems.
The final threat here is one that we pose to ourselves. When managing networks, there are often many things to manually maintain. Such a monumental task can lead to oversights and misconfigurations (e.g.) broken ACLs or outdated components and software, which make life easier for would-be hackers to manifest their nefarious intentions.

IP Fabric is not a dedicated security solution and doesn't fulfil the same functions as, say, an NSPM solution. From a security perspective, what IP Fabric can do is provide key visibility of the necessary components in your environments - giving you the necessary assurance that you have the relevant precautions in place to prevent your network falling victim to a cybercrime.
Useful for: Ransomware, DDoS, APT, Trojan Horses
Segmentation is used to prevent the spread of malware to certain parts of your network and ensure affected areas are sufficiently isolated. Even if an area of your network does become affected, the chances of it spreading and causing further issues to your network are limited.
IP Fabric itself doesn't provide segmentation. Instead, it can be used to visualize existing segmentation in your network, and whether this is sufficiently hardened. Based on this visualization, you can answer some essential questions: Does the segmentation prevent lateral movement? Is it properly configured?
All of these answers let you decide whether your endpoints are adequately protected against spreading malware in case an attack occurs.

Useful for: APT, Trojan Horses
Network Security Policy Management (NSPM) platforms help you ensure that your policies are properly defined and ideally placed to spread infection throughout your environments. Ensuring that the policies you are deploying are fit for purpose is critical to preventing attacks from having a lasting effect.
The problem with NSPMs? They have limited vendor support and only provide visibility from OSI layer 3. IP Fabric's network assurance provides full and up to date visibility of your entire network infrastructure to ensure that there are no blind spots left unnoticed. Check out our piece on the relationship between NSPM platforms and network assurance here for more information.
Useful for: Ransomware, DDoS, APT, Trojan Horses
IP Fabric can be used to provide a complete inventory of hardware, software, and configurations within your network, including EoL information that can be used to ensure your protective software remains up-to-date. Doing so provides you with the confirmation that your components aren't leaving vulnerabilities for attackers to exploit.
Whenever components are nearing EoL, IP Fabric presents information on vendor-suggested replacement for said components, so that necessary steps can be taken to ensure no gaps are left for attackers.
Useful for: APT
APTs are typically detected due to unusual activity being discovered within the affected parts of the network.
By establishing complete visibility of your network through rapid CLI-based discovery via API, SSH or Telnet, which is kept up-to-date with regular snapshots (scheduled or ad-hoc), network teams can model forwarding and policy behavior within a network using captured configuration and device state data.
Using this data, teams can examine network behavior and forwarding policies to determine the presence of unusual activity that would typically be associated with APTs and act accordingly.
The best way to ensure network security is to make sure that everyone within an organization receives the necessary information on cyberthreats to mitigate risk. After all, a disciplined organization-wide security posture is a best practice.
But nasty things can still happen, and it only takes a second, or one error in judgment, for an attacker to gain access to a network.
With IP Fabric in place, however, networking teams can more proactively address misconfigurations that may threaten network security, ensure policies are uniformly applied, and make sure that any areas of the network housing critical data are appropriately segmented.
Arming your teams with the appropriate visibility and assurance will go a long way to preventing something happening to your organization.
Check out our glassboard video below, in which Christian Giebner highlights the key ways in which IP Fabric can help to bolster your network security efforts and ensure you aren't left with any nasty surprises lurking in the shadows (Note: This video is in the German language, with English subtitles available).
Want to test out IP Fabric for yourself? Try our free, self-guided demo here.
Make sure to follow us on LinkedIn, and on our blog, where we regularly publish new content!