Week commencing 1st June 2020, and another minor release - IP Fabric 3.5.2 - is ready for deployment! Let's sum up what the latest release has to offer.
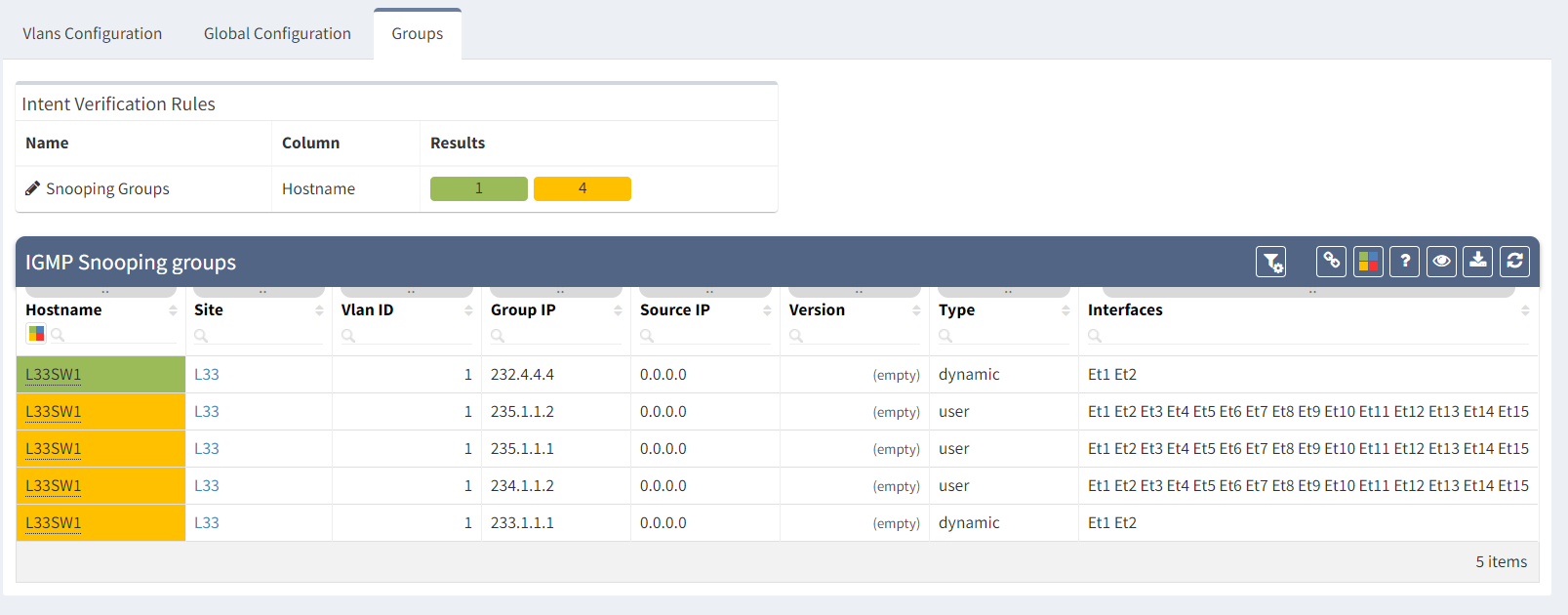
The 3.5 version started with multicast support with routing capabilities and the impressive distribution tree simulation in diagrams. The new 3.5.2 release adds information about PIM Rendezvous Points (RPs) and IGMP Snooping state. Now engineers can fully analyze multicast forwarding across LAN and WAN. IGMPv2 and IGMPv3 protocols are supported on multiple vendor platforms.
The Cisco Firepower support was introduced in mid-2019 with basic discovery features. IP Fabric version 3.5.2 is a significant milestone in the Cisco Firepower platform capability. We have now introduced full support for AAA, ACLs, NAT, and Object Groups, to mention but a few features.

Security is inevitably a critical part of any infrastructure and we continue to develop IP Fabric's capabilities in that area. On the roadmap for later in 2020 is a major release to address network security specifically. Expect to see significantly enhanced support for other vendors' firewall platforms, and for new network security features in general!
IP Fabric discovery is already fast, but we feel we can always make it faster! Up to now, every time IP Fabric created a snapshot it automatically attempted to discover any new nodes beyond those it already knew about.
In version 3.5.2, you can now limit a new snapshot to only update already-discovered network devices. This prevents IP Fabric from firing up the discovery algorithm that detects new devices on the network. This capability of locking the discovery scope is a huge improvement for large scale networks. Let's see how it works.
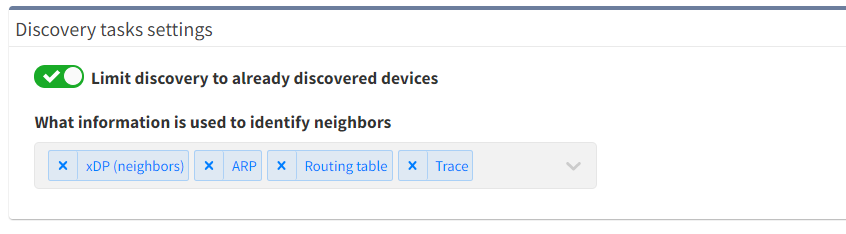
Previously the standard discovery process started with already-discovered devices. IP Fabric would then attempt to connect to unknown endpoints using the discovery algorithm.
As of version 3.5.2, if we know that our inventory is complete, we can simply tell IP Fabric not to search for new nodes. This prevents the system from spending additional time on testing more and more IP addresses as possible new devices. We then enable the discovery of new devices when we know that changes have been made. Alternatively, we use it when we're explicitly wanting to check our online inventory is up to date.
Note that we can now also modify the methods that the discovery algorithm uses to find and identify neighbors in the topology. This is helpful for optimizing the discovery, for example, if we are certain, that one of the methods is not supported in our network devices or is not configured.
In 3.5.2, you can also see our commitment to continue to improve support for multiple network vendors. Changes to feature support and improvements are evident for:
More details at IP Fabric Release Notes.
There are some BIG updates coming over the next couple of major versions in the platform, due over the coming months. Keep coming back to wordpress-625423-2416527.cloudwaysapps.com and follow IP Fabric on LinkedIn for more information as it drops!
A network security audit is a systematic evaluation of the security of a company’s information systems or network intermediary devices. We evaluate the secureness of the network using a few different sets of criteria, including measuring how well the devices conform to a set of established rules.
A thorough security audit typically assesses the system’s physical configuration, environment, software, information handling processes, and user practices. Traditionally, this process uses up a lot of valuable work hours, and can easily give inaccurate results if a tiny mistake is made anywhere along the way. But today, thanks to IP Fabric, teams can perform this security audit in just under an hour.
Let’s take a look at some of the ways that IP Fabric can help you conduct a network security audit quickly.
When it comes to successfully exporting security policies from SRX, IP Fabric gives you plenty of options.
The very easy one is to export the configuration between security zones to a text file and upload and send them to a customer. But it could be time-consuming for non-Juniper technicians or managers. Also, for some people, it may be difficult to comprehend all the information in the configuration file.
Another option may be buying Junos Space software with the Security Director plugin. Or we could develop any customized script using Junos PyEZ library and export policies to multiple file formats. Both have their downsides.
"As a DC service provider, we have implemented a robust firewall cluster that currently supports more than 2000 clients. These clients request the security reports on a daily basis. The reports have to include the most current security policies configuration as well.
As a result of using the IP Fabric platform, we can create and export a comprehensive report anytime. Typically, fulfilling this request would take all day, but with IP Fabric, this entire process takes mere seconds to finish."
In a multivendor environment, enforcing an authentication means verifying that everything is what it claims to be. The purpose of an 802.1x verification is to help you accept or reject users requesting full-access to a network that uses 802.1X protocol.
Today, more and more companies shift towards tighter LAN security. They’re discovering that this process can cost them countless hours on implementation and verification if they try to do it on their own.
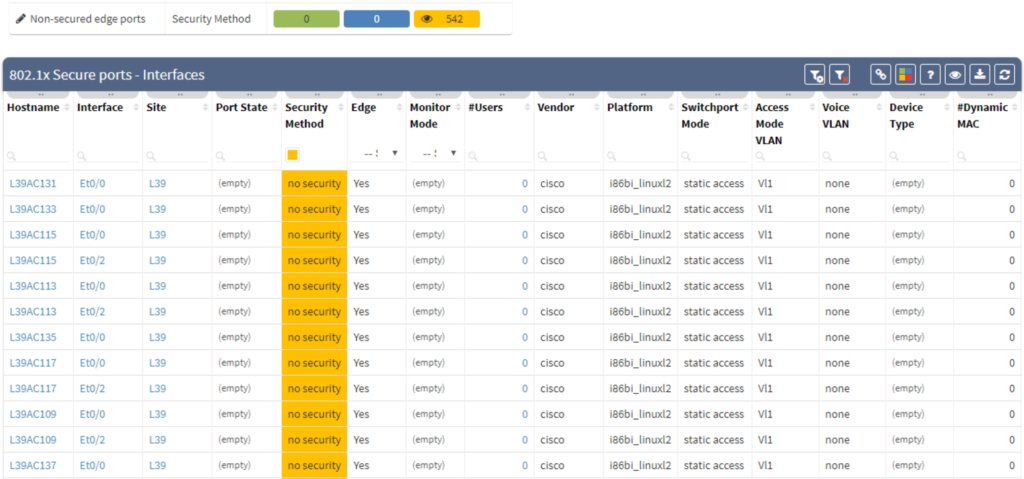
"In our company, we have more than 800 employees at 12 separate locations across the country. Using traditional methods, 802.1X protocol implementation is a long and arduous verification process. It can easily take more than three months to complete.
On the other hand, with the IP Fabric tool, we were able to tackle the verification process almost instantly. The tool simplifies and automates 802.1X verification, allowing us to run it as frequently as needed."
Access-lists (or firewall filters) are a key feature when enhancing security across networks. They deny or grant access to devices based on specific combinations of source, destination IP, destination port, or other kinds of data. ACLs are fast and easy to implement. However, they are difficult to troubleshoot, even when appropriately applied. The IP Fabric platform compiles all of your ACLs into one place, allowing you to compare and correlate rules across all network devices easily.
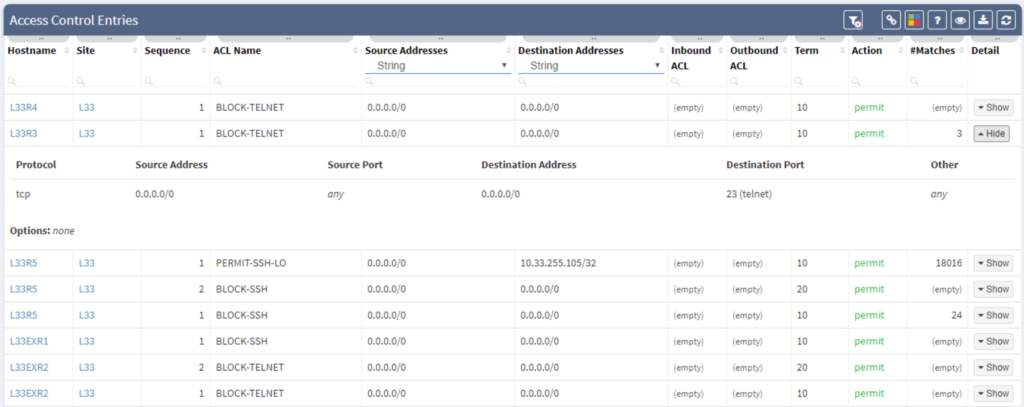
"Our MPLS network has thousands of network devices. To ensure compliance, we need to quickly verify that an up-to-date firewall filter is protecting management loopbacks. The IP Fabric platform can complete this task almost instantly and will give you a comprehensive device list that you can easily export and share."
The Authentication, Authorization, and Accounting system is used to track user activity on an IP-based network and control their access to network resources. It is time-consuming to verify that all network nodes are configured along with the same AAA framework when managing complex network infrastructure.
The IP Fabric platform reduces the amount of time and hassle involved in AAA by giving you a highly detailed overview of all AAA-related information.
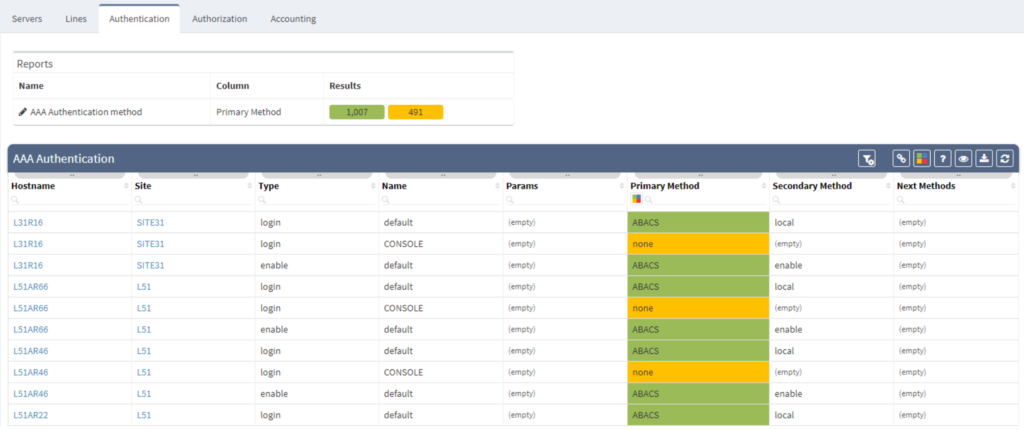
"A few months ago we decided to migrate all of our network devices to a new AAA server, which meant that we also agreed to a change of authorization rules.
The IP Fabric platform made tracking the progress of the migration effortless, meaning we had more time to focus on more critical tasks."
Simple Network Management Protocol (SNMP) and Syslog are the key protocols for maintaining and monitoring network. A network engineer needs to ensure that both protocols are reporting properly to dedicated SNMP and Syslog servers. Above all, one must apply security correctly to this type of communication.
Thanks to IP Fabric, you’ll have a detailed structure report related to these protocols.
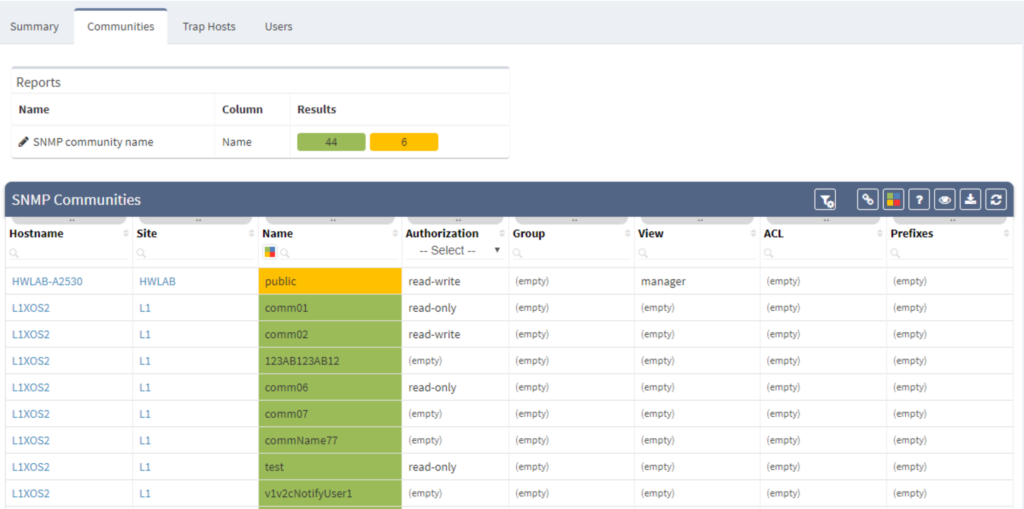
"Over the last 15 years, our network has evolved countless times, and we have lost track of correct SNMP configuration a few times along the way.
Since security is incredibly important to us, we designed the IP Fabric tool to help us verify that all SNMP traffic is sent to dedicated servers and that read-write rules are active at all times."
Interested in learning more about how IP Fabric’s platform can help you with analytics or intended network behavior reporting? Contact us through our website, request a demo, follow this blog, or try our self-guided demo.
Juniper SRX is a wonderful firewall device with a lot of rich features. However sometimes the complexity of security policies may grow greatly with multiple embedded addresses or application objects, more virtual routing and forwarding instances, route leaks and so on. It can come to a point when managing all security rules and providing service to multiple clients for datacenter or other infrastructure at the same time, can become very cumbersome. The fastest and most secure interaction with the firewall so far is still the command line interface. This exact area is one of the strongest and most versatile, when it comes to Juniper boxes. If you are an experienced tech, you may be able to interact with the SRX swiftly and easily. Moreover, narrow down any critical information related to troubleshooted issue, but It’s not so simple with security rules export.
but It’s not so simple with security rules export.
To be able to successfully export security policies from SRX, we have handful of options. The very easy one is to export configuration between certain security zones to a file. Furthermore, upload to a server or send to a customer. But it could be time-consuming for a non-Juniper technicians or managers to be able to comprehend all the information.
Another option would be buying Junos Space software with Security Director plugin. It's a specialized administration and orchestration tool made by Juniper, which can be easily installed in the cloud. It’s a great all in one tool for almost any Juniper device. In Security Director, security policy exports can be filtered appropriately. However, the only format options are PDF or the ZIP file and only Juniper firewalls are supported.
Or we could develop any customized script using Junos PyEZ library and export policies to multiple file formats. A little bit of coding never hurts anyone and it’s fun. Nonetheless, it needs to be maintained and updated in time. Further, you would be still interacting with command line interface, if there would not be any front end supporting the script itself.
Or there’s one more option that is available since IP Fabric version 2.2.4 was released (the most current one is 2.2.5). After successful discovery of any Juniper SRX with security policies by IP Fabric, you are just few clicks away from full-fledged policies export. It’s simple as that.
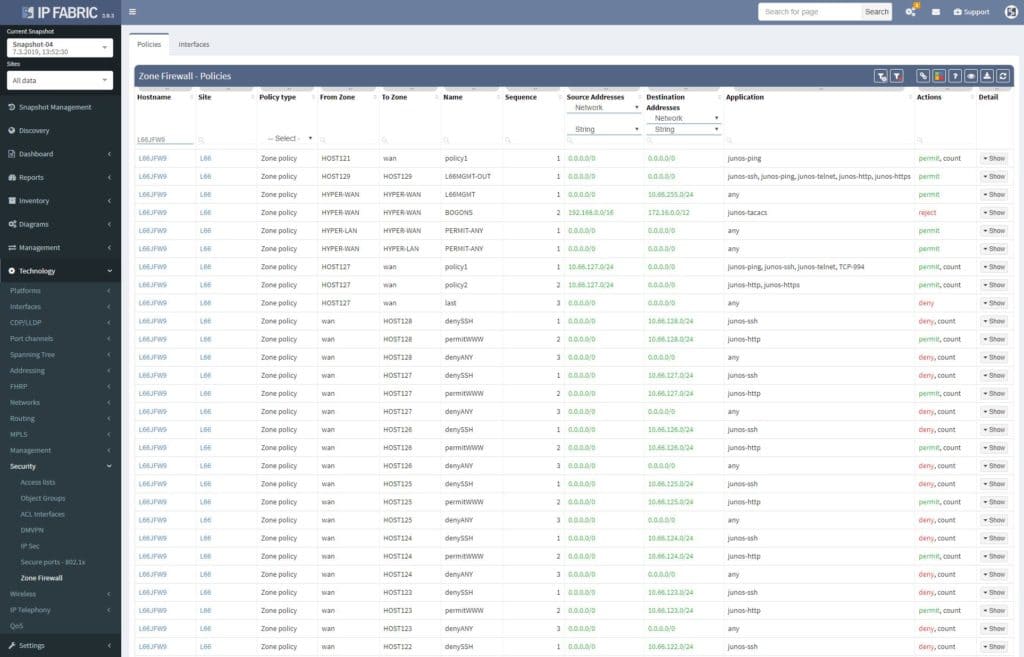
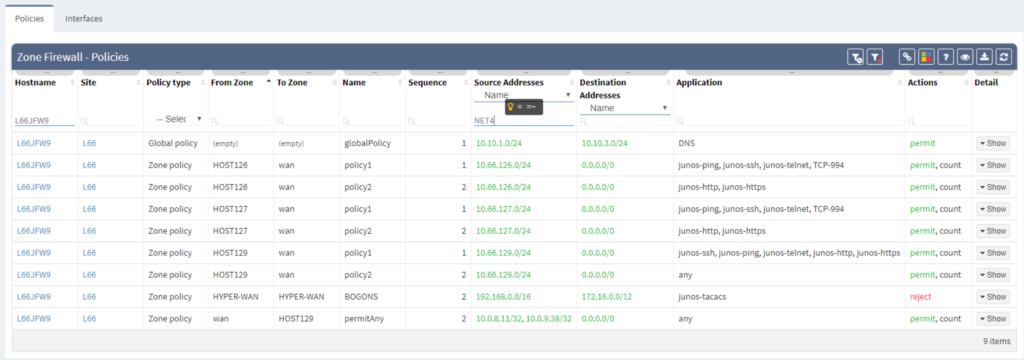
When opened in browser, the Zone Firewall related information can be navigated via Technology > Security. The default view is fully customizable, including colorizing columns, advanced filters and more. There’s a lot that has been done when it comes to custom tables and views recently.
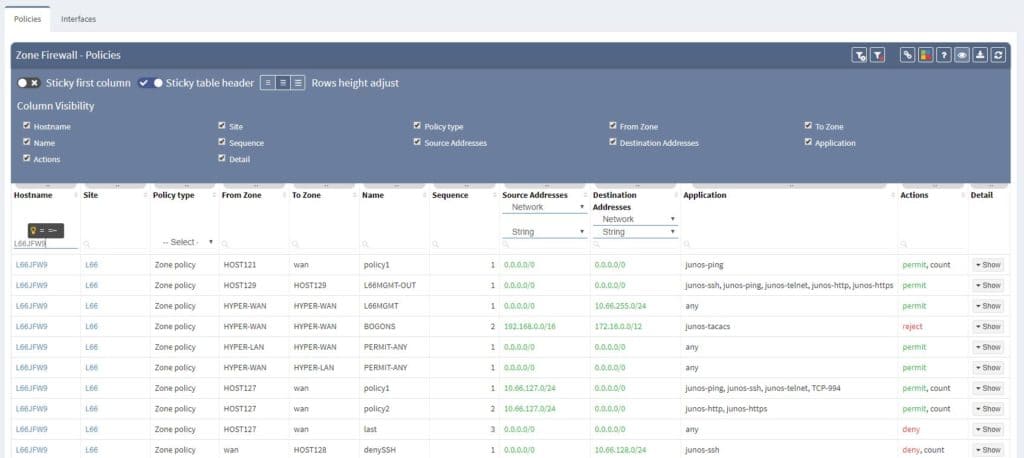
Single security policies can be furthermore unwrapped with address and application objects being resolved. IP Fabric understands even Junos default applications configured object and application sets, all well prepared for end-to-end path resolution via SRX, which is another stunning feature described in another article.
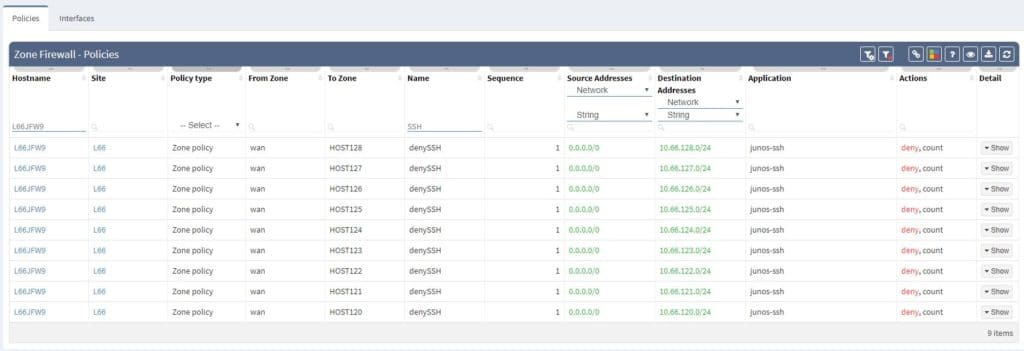
Filtering is supported with regex capabilities and its fast interface provides seamless experience to any security administrator or technical manager. Any filtered information can be exported to CSV format and downloaded.
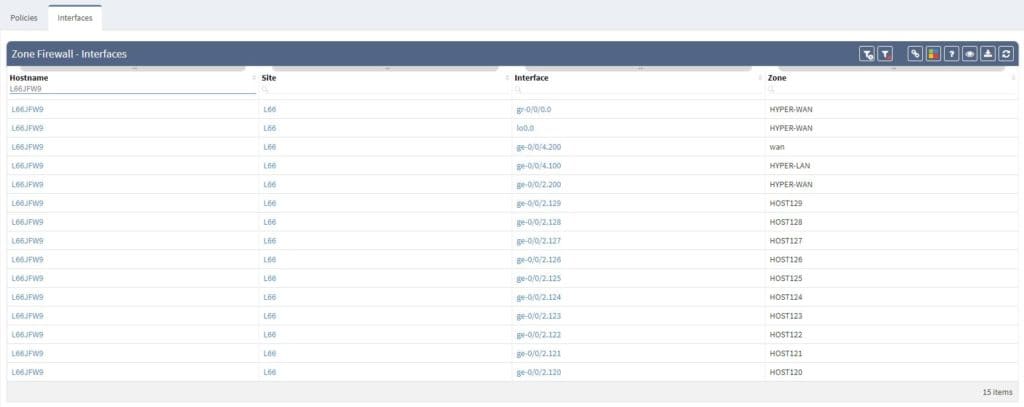
Another very handy feature is matching the security zones with its related interfaces. We need to simply navigate to Interfaces view when in Zone Firewall section and all information is available at hand, all can be exported as well. It’s all in one, easy to navigate and very fast to interact with.
If you’re interested in learning more about how IP Fabric’s platform can help you with analytics or intended network behavior reporting, contact us through our website, request a demo, follow this blog or sign up for our webinars.


