The latest 2.2.8 version released very recently again brought new powerful features and updates to our customers. IP Fabric is continuously gathering feedback and request from customers and one of them was to be able to work with more network devices and vendors, specifically devices from Arista Networks.
I have been in the networking field for almost 10 years now. I started with Cisco (as majority of network techs), then shifted to Juniper and played with other switches and routers along the way (not mentioning firewalls or other equipment) like HPs, Netgear, VyOS, MRV and more, but I have honestly never ever tested equipment made by Arista before. So I am feeling a bit excited by stepping into unknown.

I am not about to let you dive through our process in detail, there are technical parts in the IP Fabric process that should be kept under the hood for special reasons. However it logically involves studying provided materials related to new technologies in detail, testing classic routing and switching topologies from start and devices’ interaction capabilities with our systems. We also work with subject matter experts and domain experts to guide us through the process.
Luckily for me I may say there may be undeniable resemblance when it comes to command line interface to other vendor that we already support. I am not gonna mention which one it is, but you can test on your own. And that is saving us some time, so we don’t have to reinvent the whole wheel in regards to device discovery. Arista Networks was founded in 2004 by former Cisco engineers, their boxes run on linux based Extensible Operating System (EOS). And I praise it a lot, it has python library included, you can jump to bash and play along as you like as in any linux environment. I haven’t tested their Json-RPC yet, but I am probably about to. I’d say the whole EOS concept is very clean and open and of course you can run your own scripts. There’s also vEOS on the market for cloud environment.
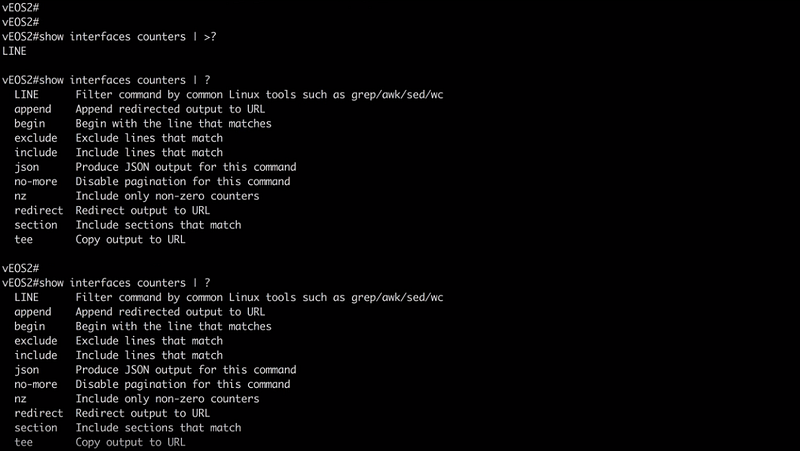
All good for now, I am very happy to announce this little teaser for next release and stay with us!
If you’re interested in learning more about how IP Fabric’s platform can help you with analytics or intended network behavior reporting, contact us through our website, request a demo, follow this blog or sign up for our webinars.
At IP Fabric we’re committed to helping network engineers with mapping and verification of their critical networks, undeniable part of which is helping to understand each issue and its implications. That is why we’re happy to welcome Orhan Ergun, a well-known industry expert, consultant, CCDE trainer, and a published author, to our Technical Advisory Board. Orhan will work with us on making the product a better engineering experience and making it more useful for engineers throughout network lifecycle.
Today, we are delighted to announce a new feature loaded release 2.2.8 of our IP Fabric Network Infrastructure Management Platform — Engineering Edition. This release is full of new exciting features and improvements, ranging from a new routing protocol support — EIGRP and RIP, through additional technology verification for Authentication, Authorization, and Accounting (AAA) to improvements for the existing tables and verification checks. We have listened to your feedback closely and implemented major improvements for the diagrams, so that you can display more information both visually and in the related popup windows.
Many of you have asked for ability to display additional information directly in the diagrams and we are delivering it today. Now you can display or hide additional network detail without going to the Technology Tables.
There is a number of options to display detailed information for various layers and technologies:
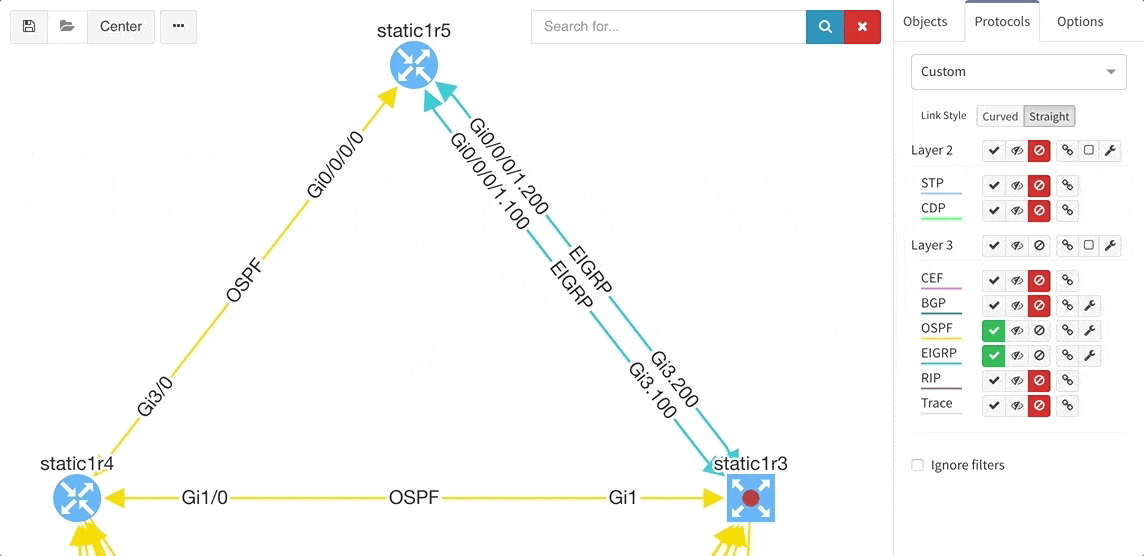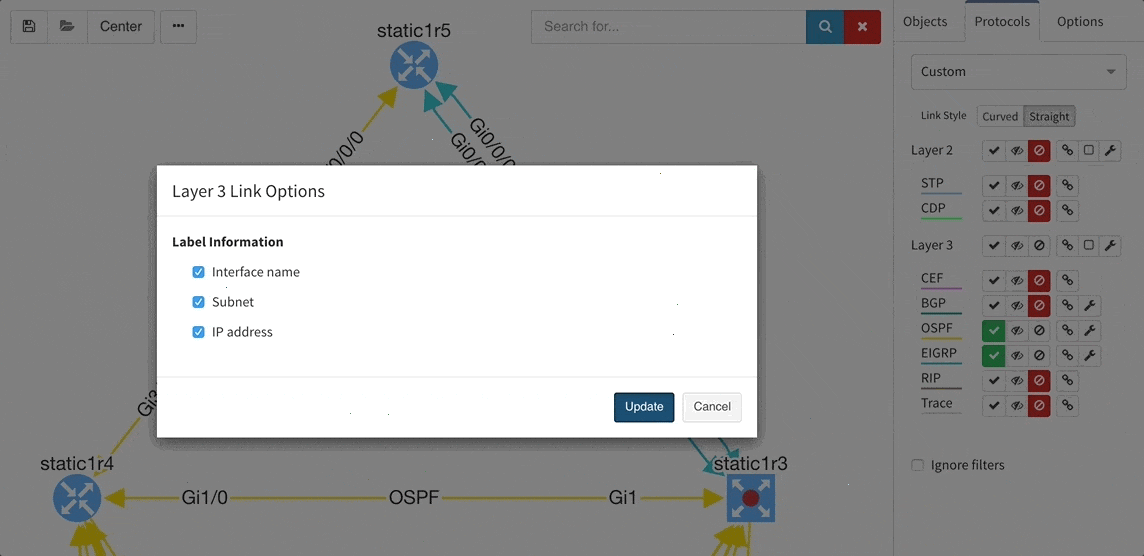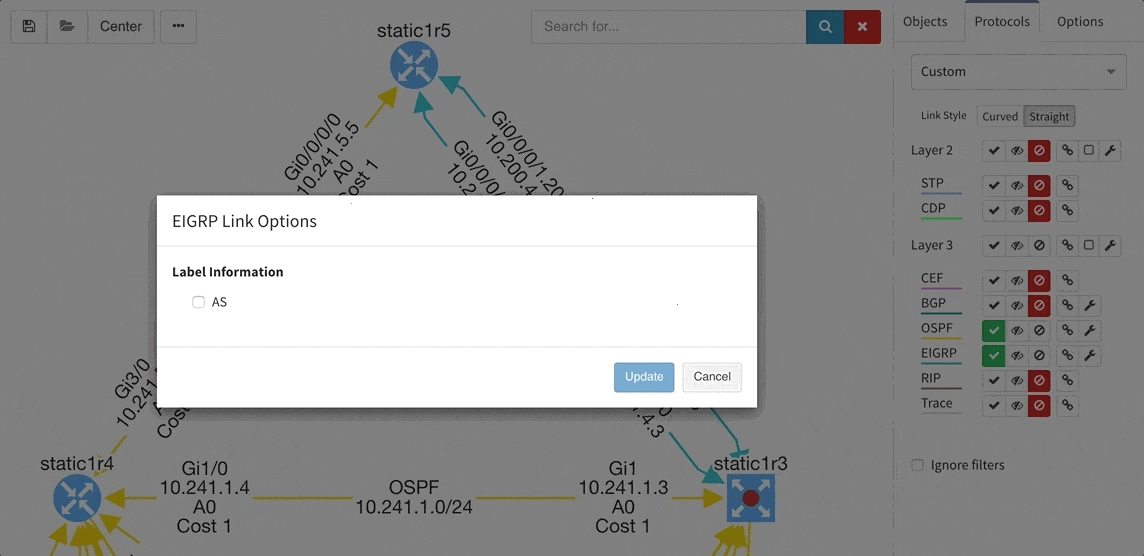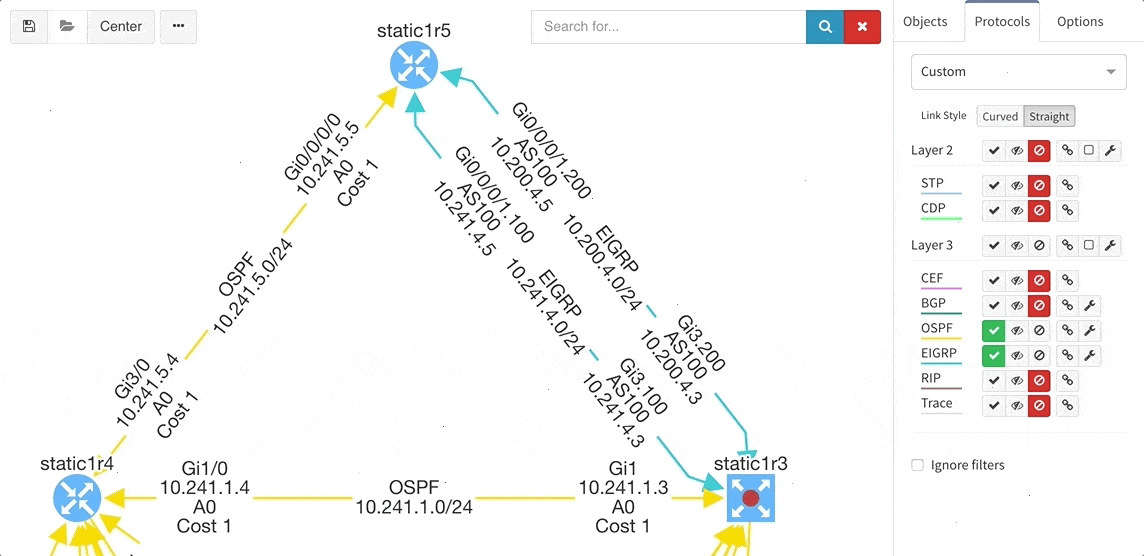
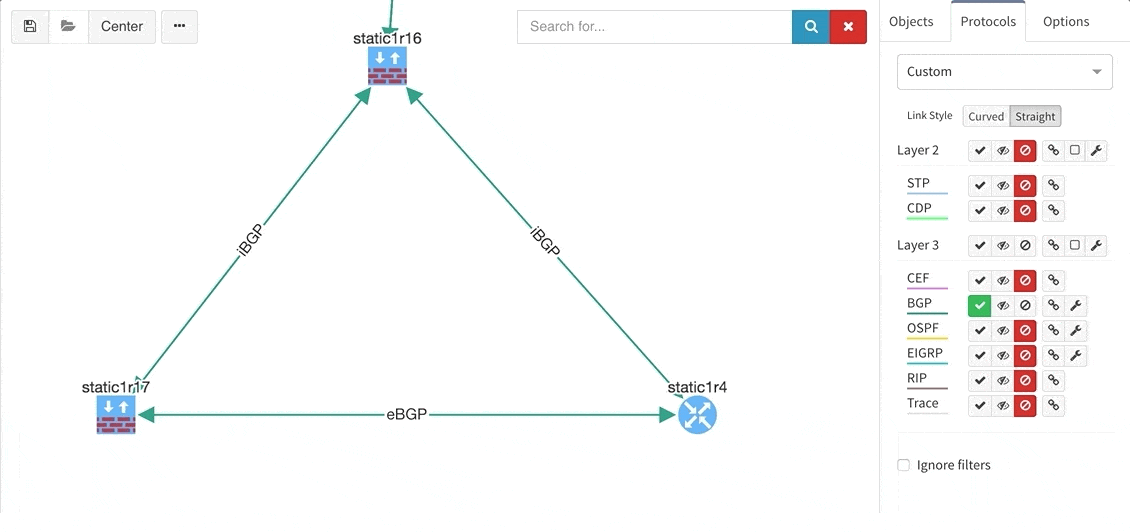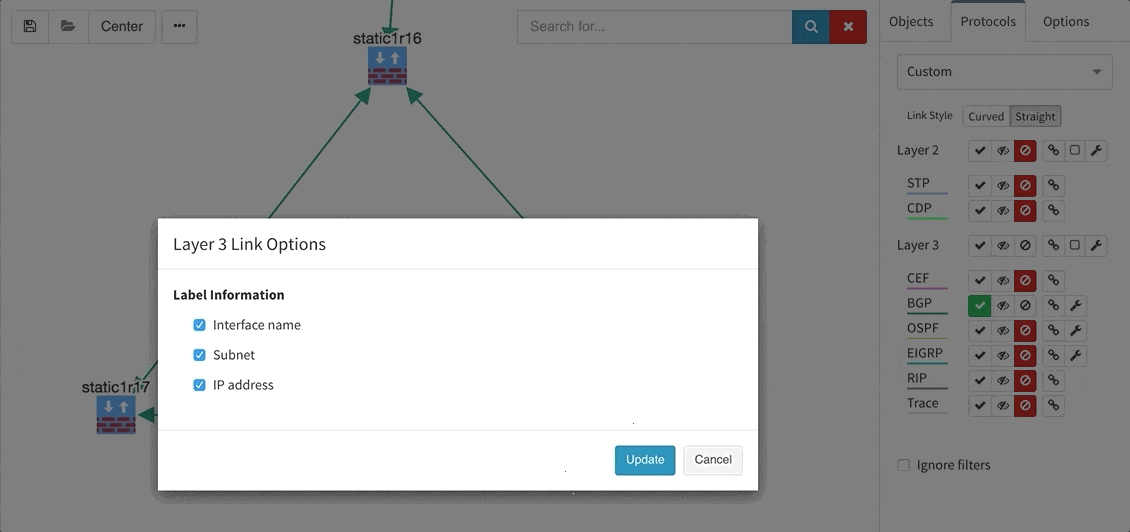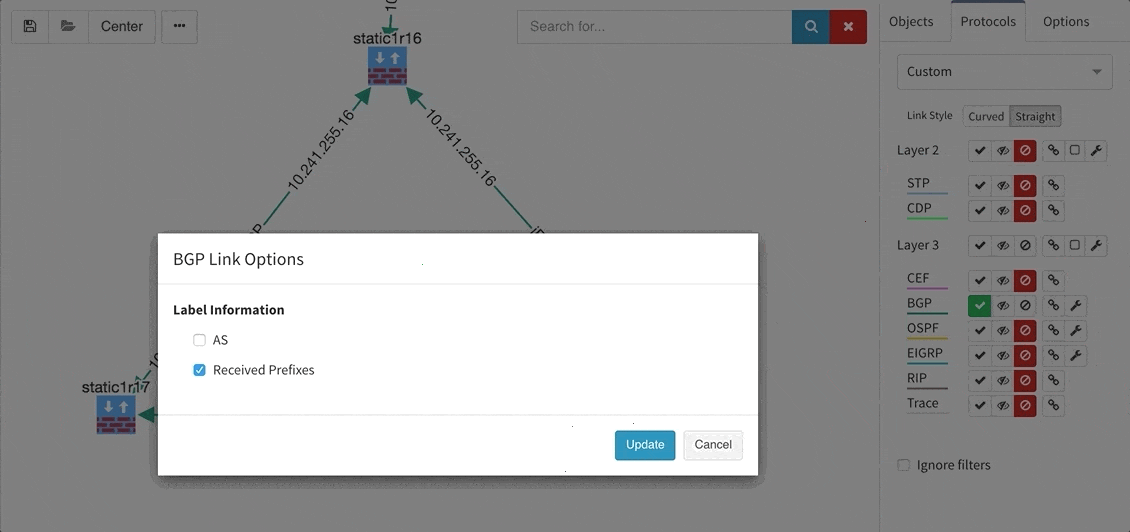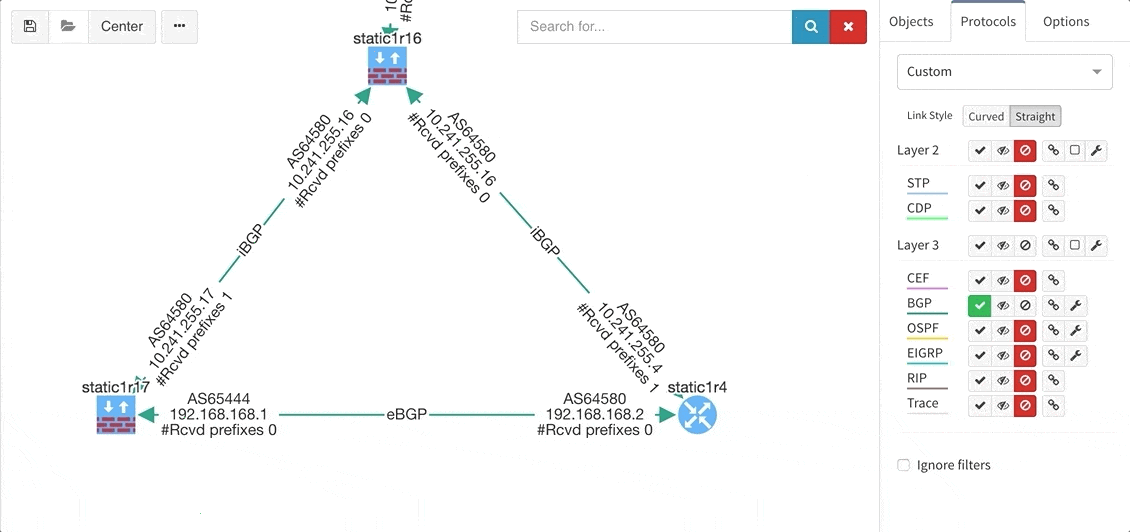
These new options, however, created an issue — the diagrams became overloaded with information. Therefore, we created a new straight link style that works better than the default Bezier curves, especially if you need to display more details on multiple parallel links.
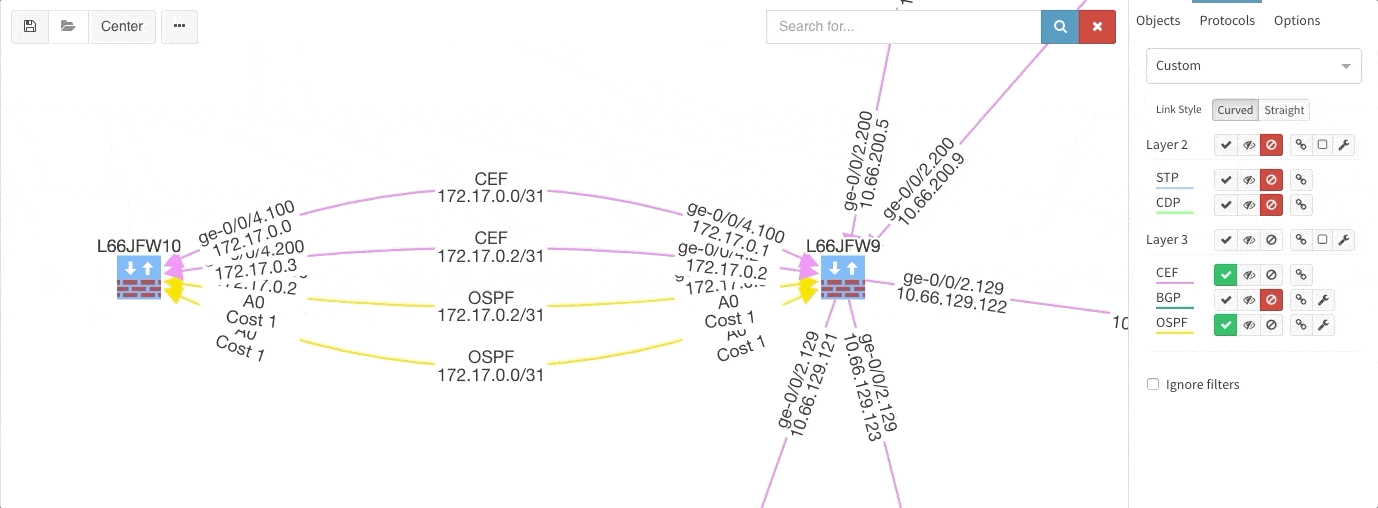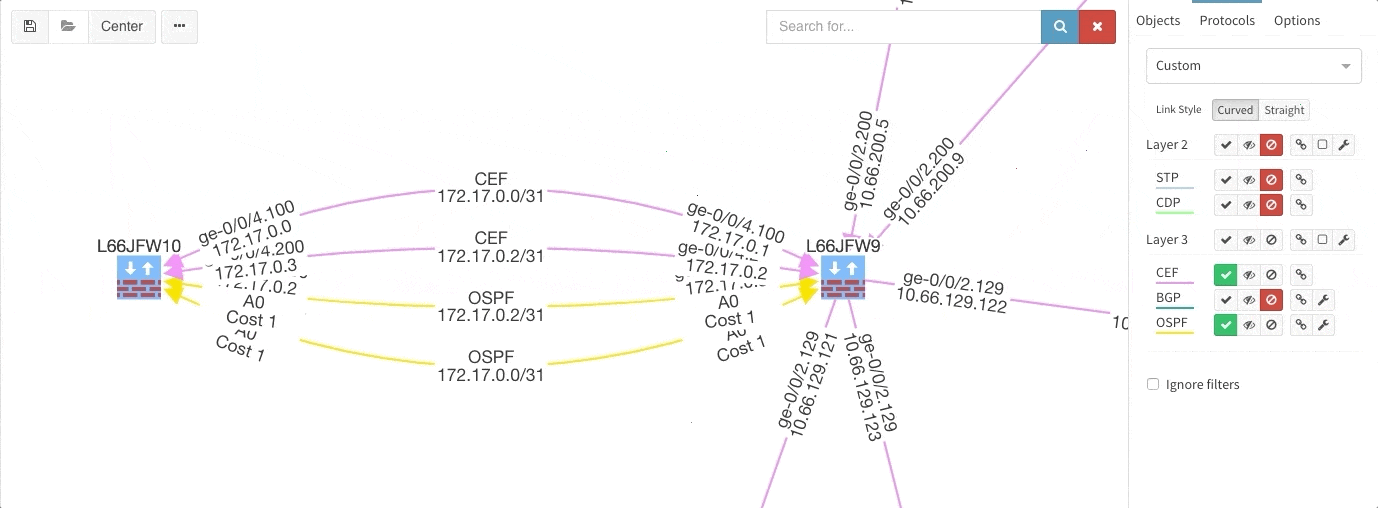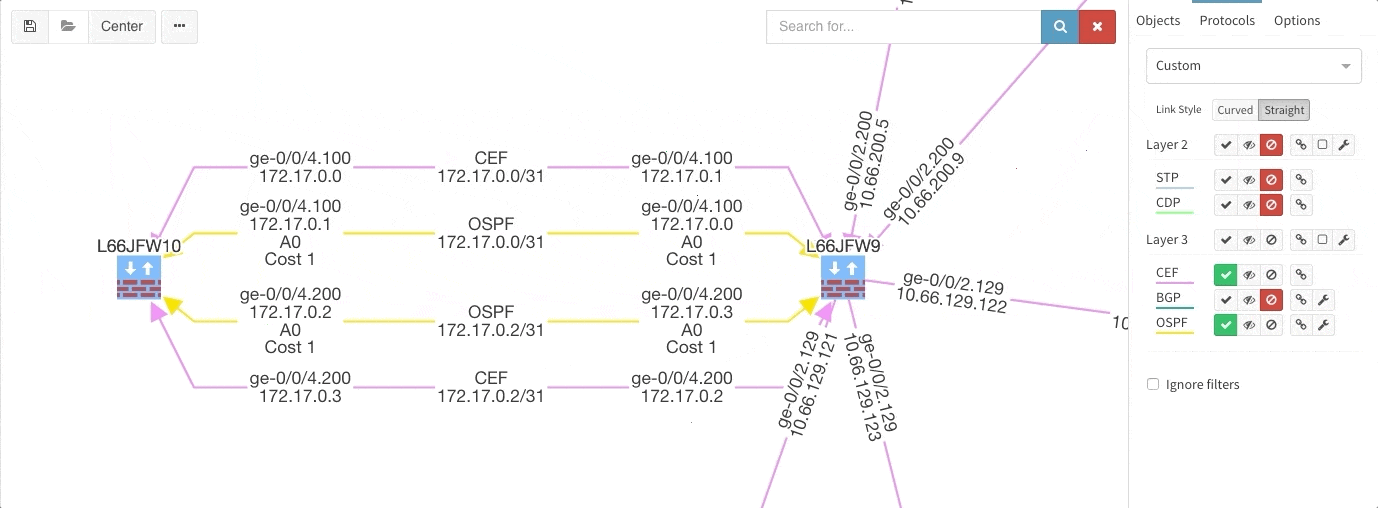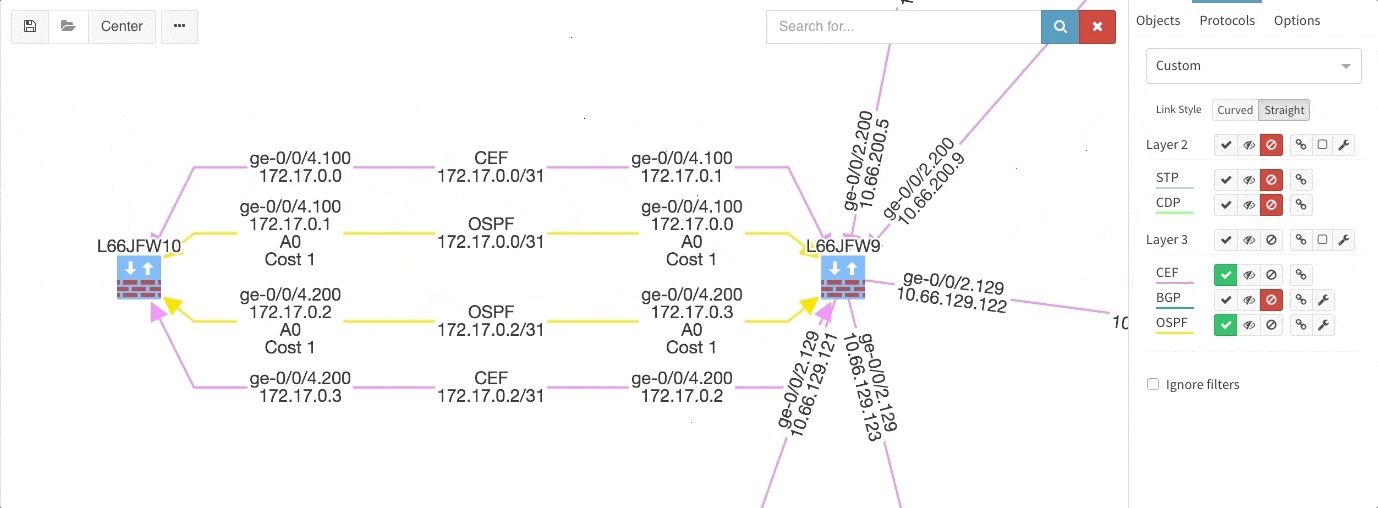
Rethinking link style calculation proved very popular, because straight links can represent more information more clearly, especially when displaying multiple paths or protocols.
One of the awesome features of IP Fabric is its End to End path lookup. It allows you to test whether the traffic will be allowed through the whole infrastructure or not and why. However, in complex networks it was not very easy to find what is wrong with the path as there were only arrows to signify the resulting decision, and no clear indication of the problematic devices. To improve visual interpretation of the path lookup result we implemented highlighting of the devices which are causing a problem or are prohibiting traffic to pass, be it either because of ACL, Zone Based Firewall, Routing or Switching. Forwarding verification result has also been added to the device popup windows to provide detail from routing and switching perspective.
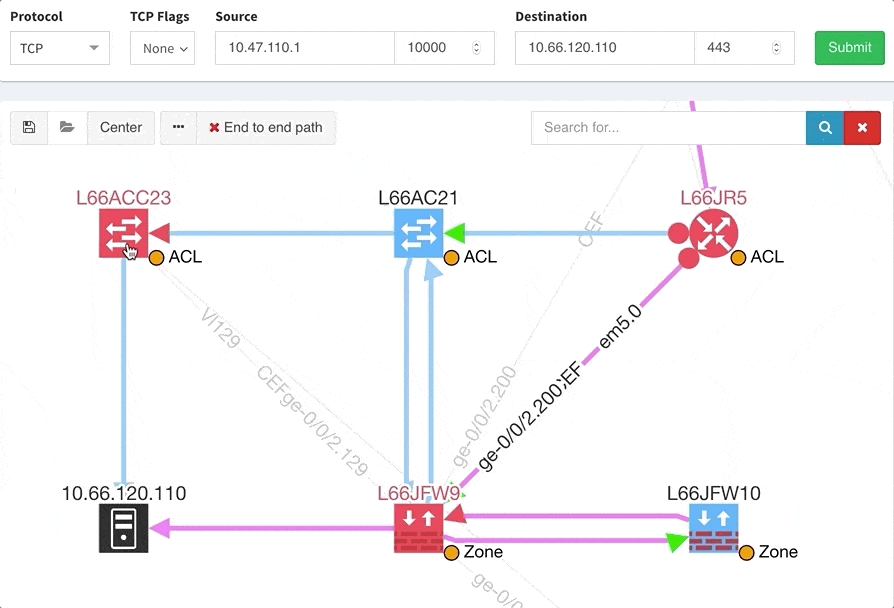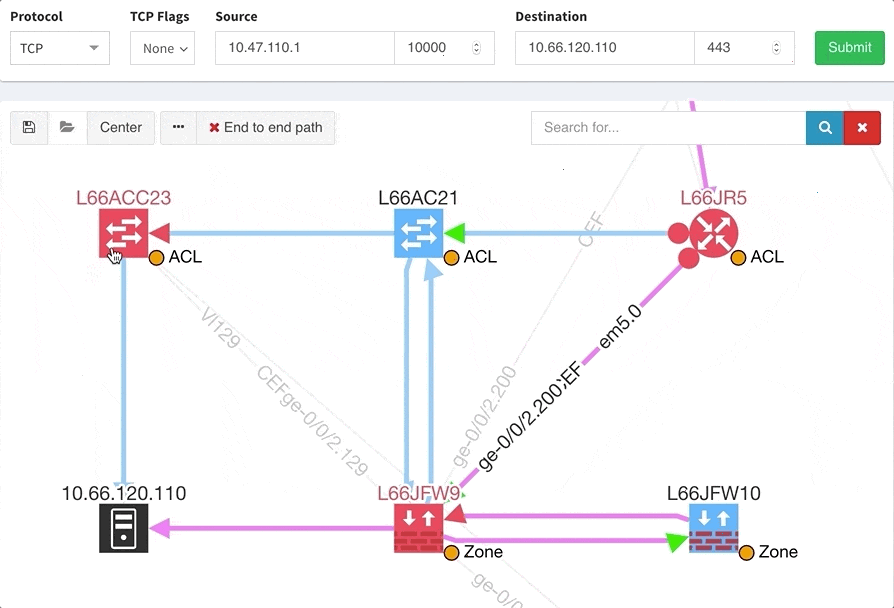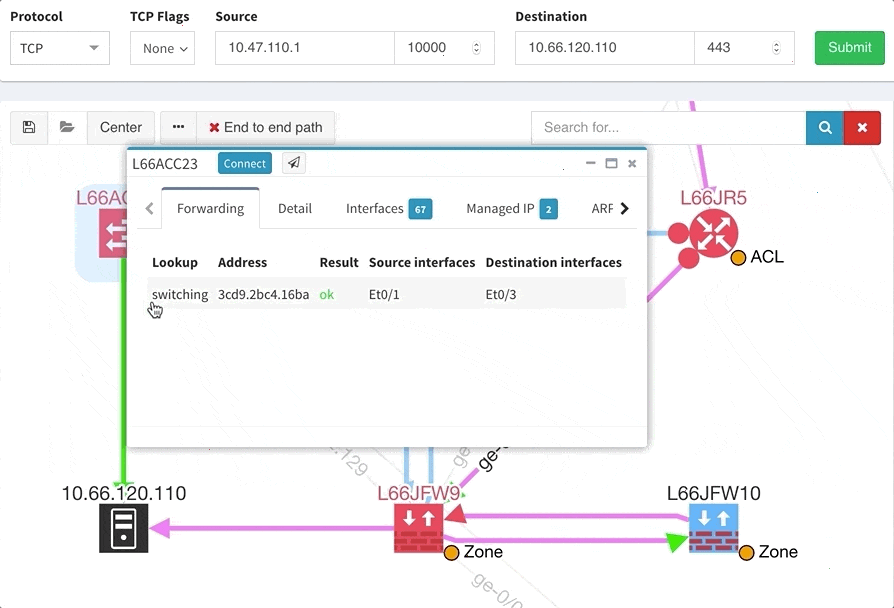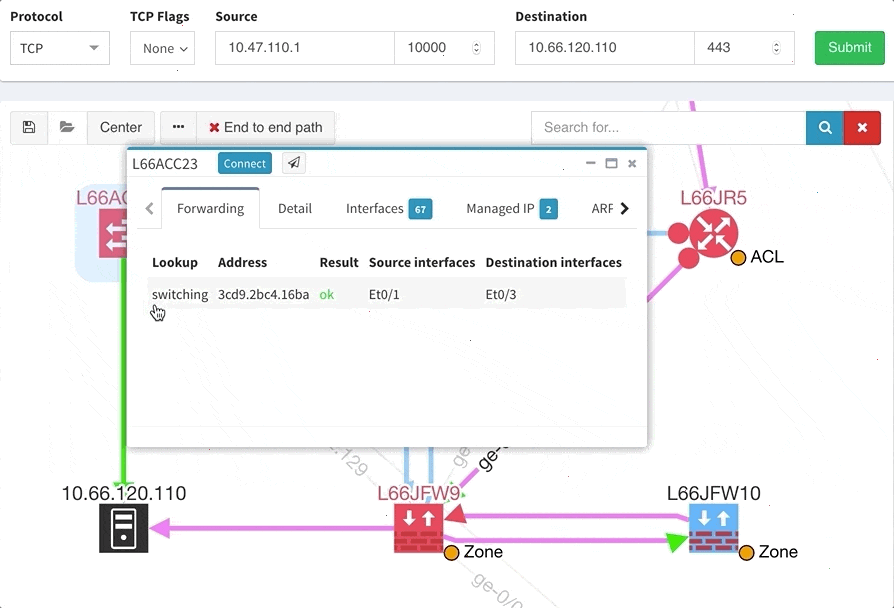
The path lookup is truly end to end, meaning we do not stop at the first device denying the traffic but finish the path simulation, so that we can highlight all the issues on that particular path.
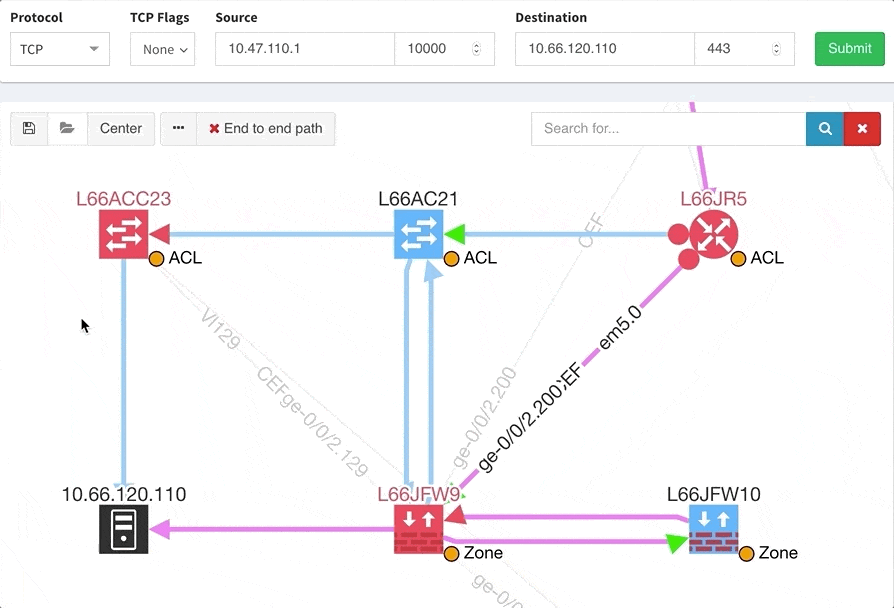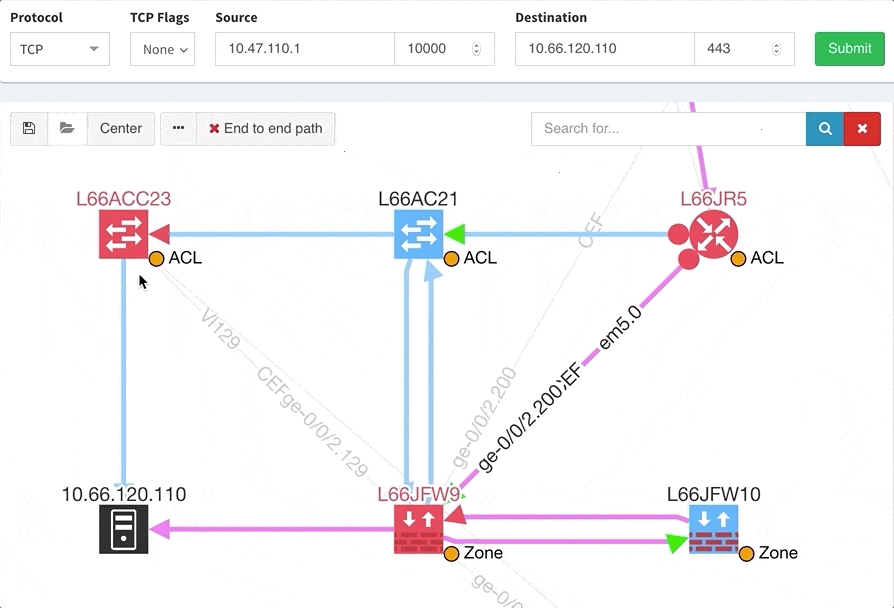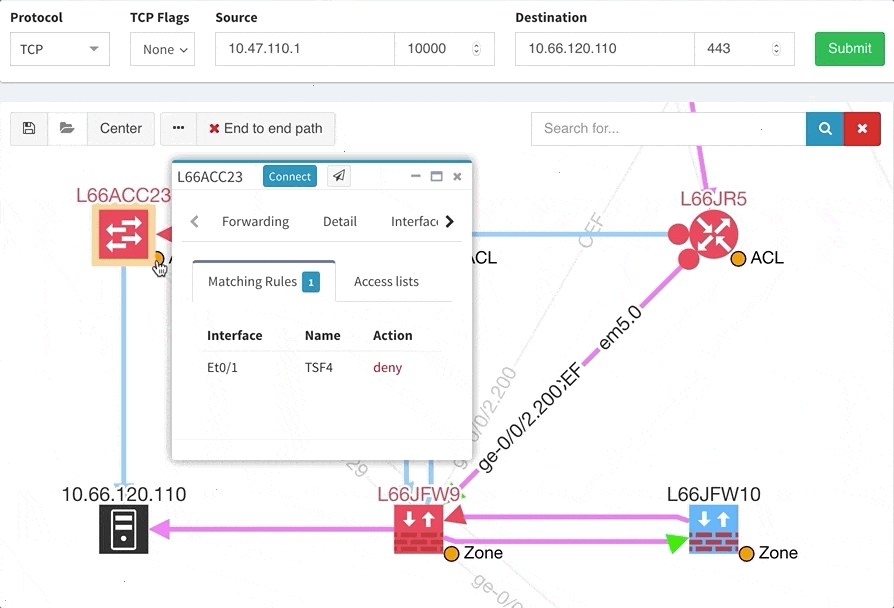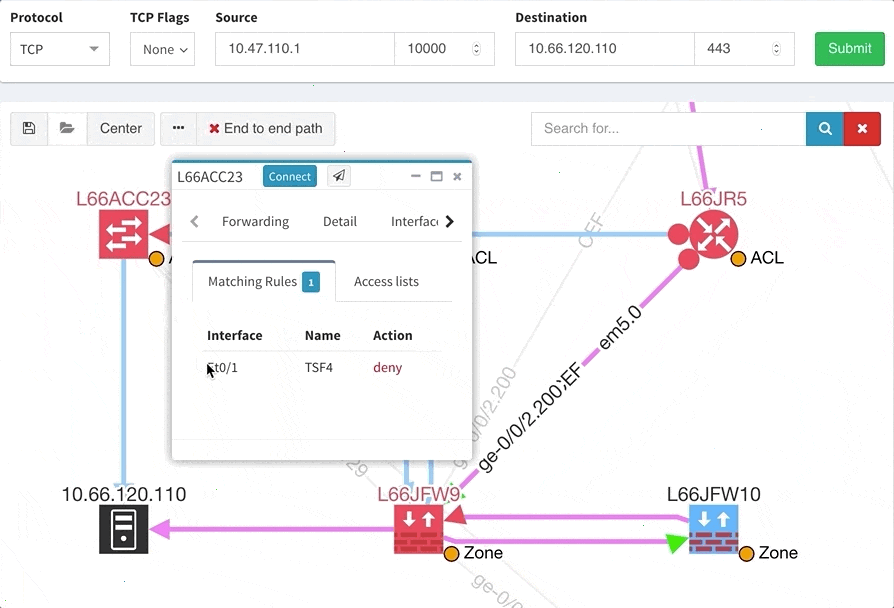
This enables you to prepare all the necessary changes at once, instead of moving hop by hop.
IP Fabric now provides detailed information about configured Authentication, Authorization and Accounting (AAA) servers, policies and how they are applied through your network infrastructure. This can be used for validation that all devices are hardened properly, that the users logging in are being properly authenticated and authorized, and that all their activities on the device are logged and accounted for.
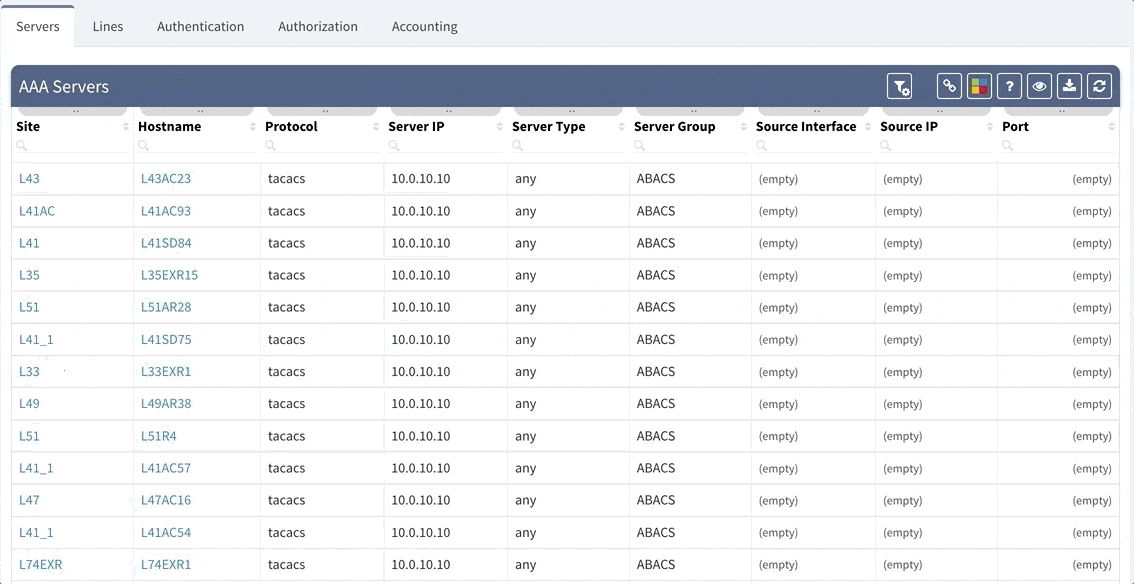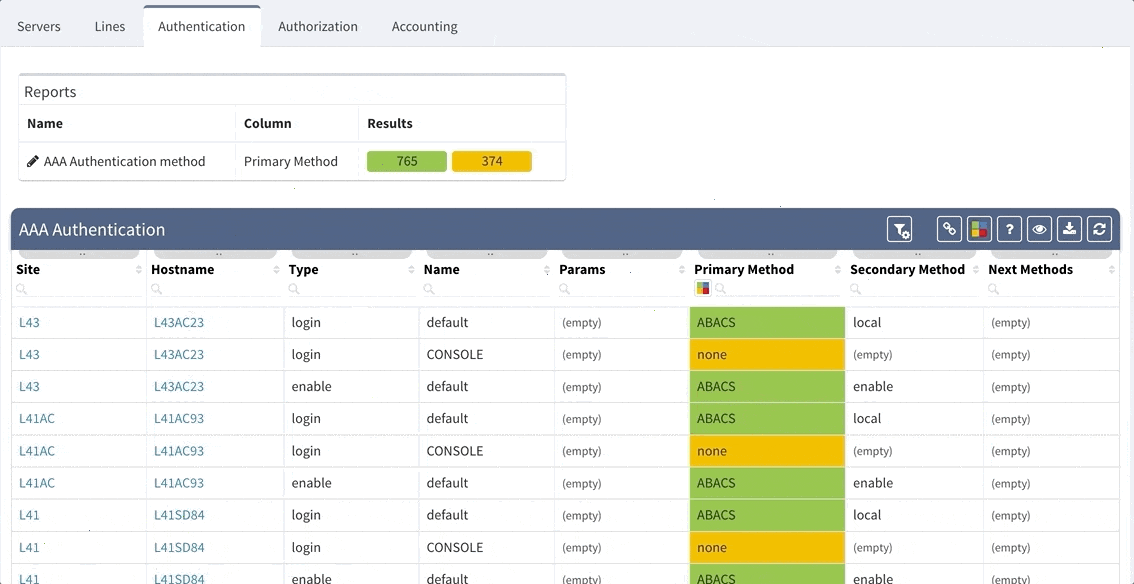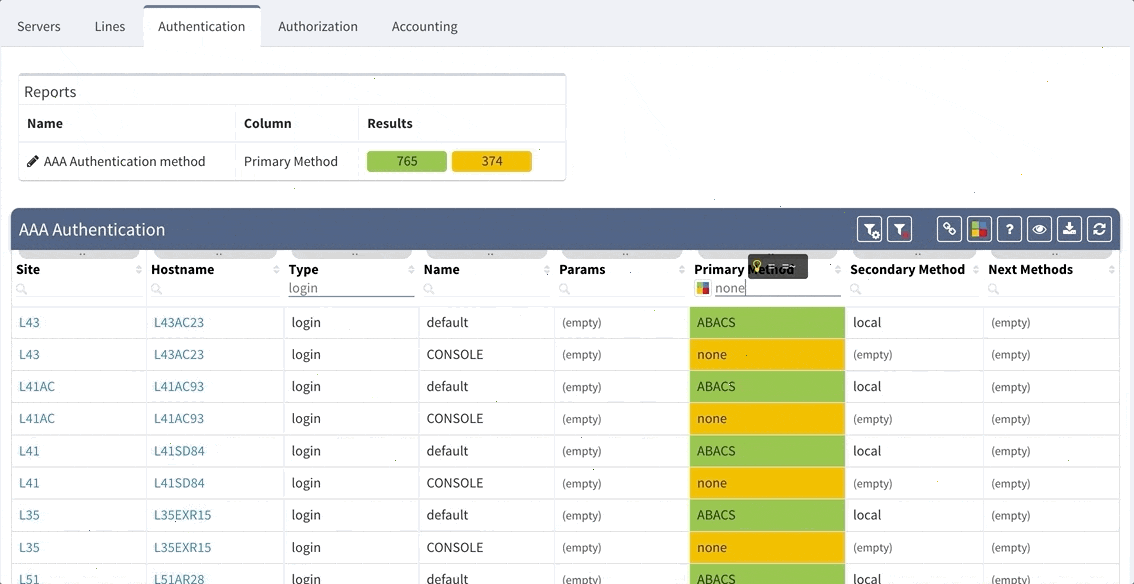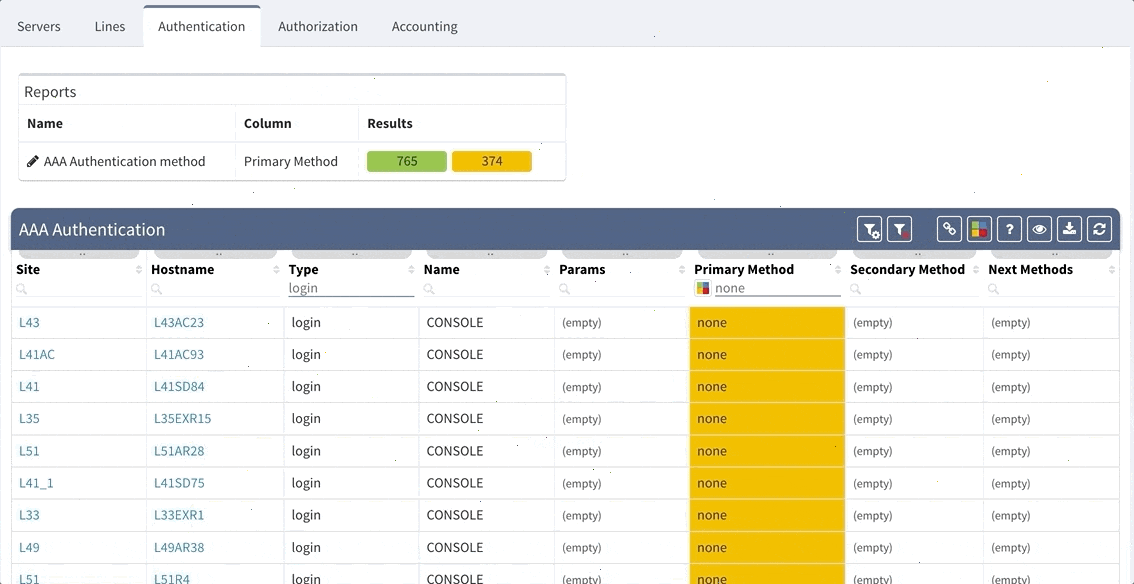
This is an example of how intent-based verification is much more robust than text-based golden config checks. With IP Fabric's platform you can ensure that general AAA rules are followed throughout your network, and that operational state complies with your intent of how the network is supposed to operate, regardless what OS device is running or if the device is HP, Juniper or Cisco.
While we support general routing verifications regardless of the protocol or the route source, with 2.2.8 we’re expanding detailed routing protocol support from BGP and OSPF to EIGRP and RIP. As always, the data is presented in the structured technology tables, the knowledge base, as well as in Diagrams.
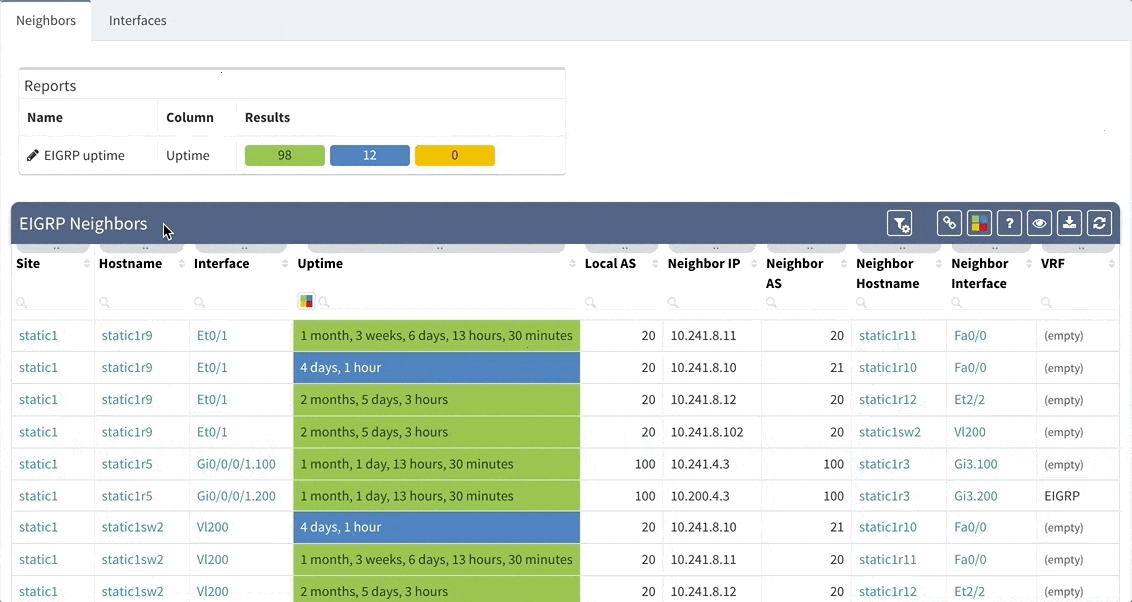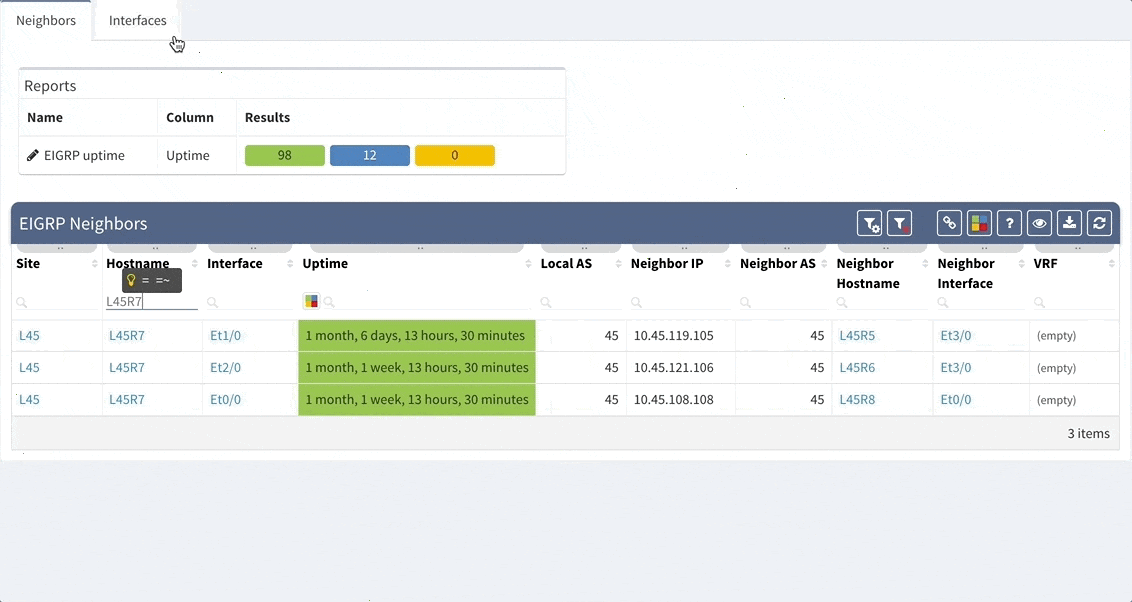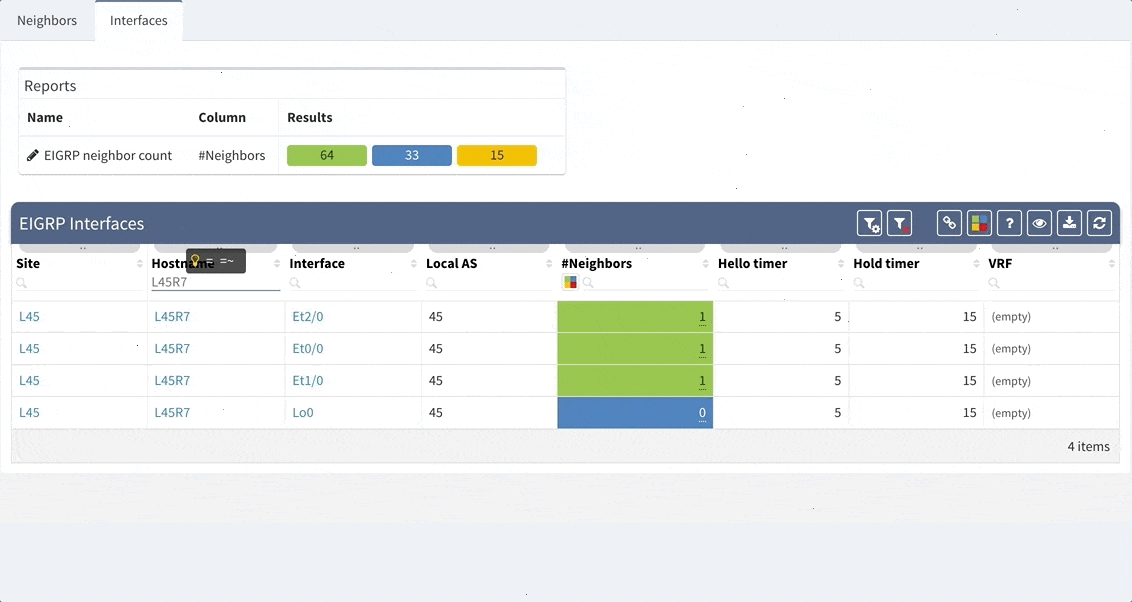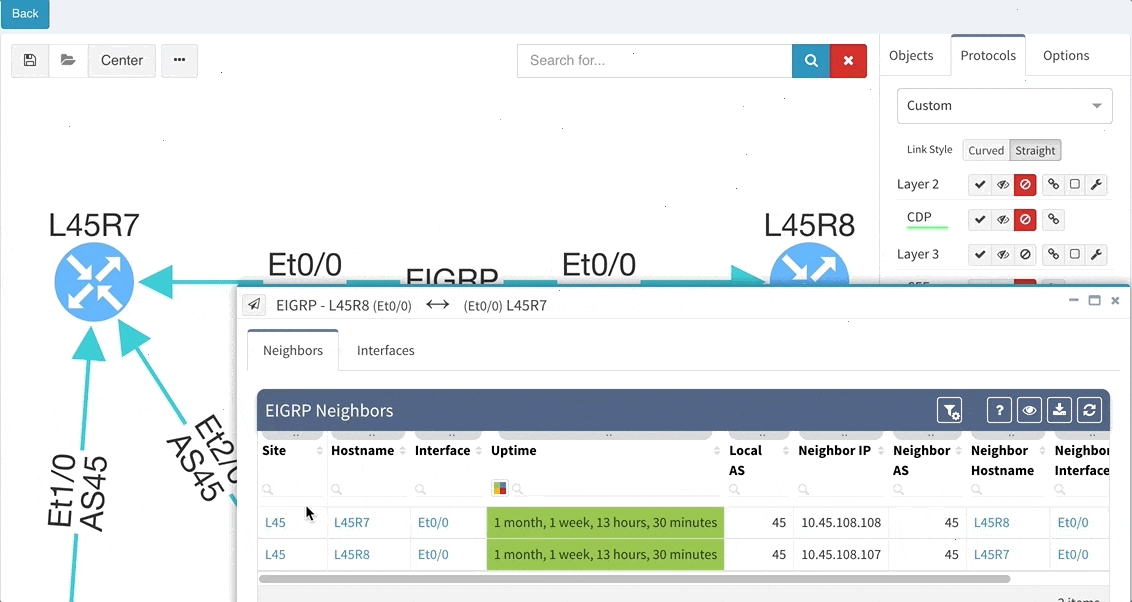
BGP support was also improved, providing out-of-the box information about internal and external peering as well as details on BGP session uptime. This is very helpful for troubleshooting flapping or recently converged BGP sessions.
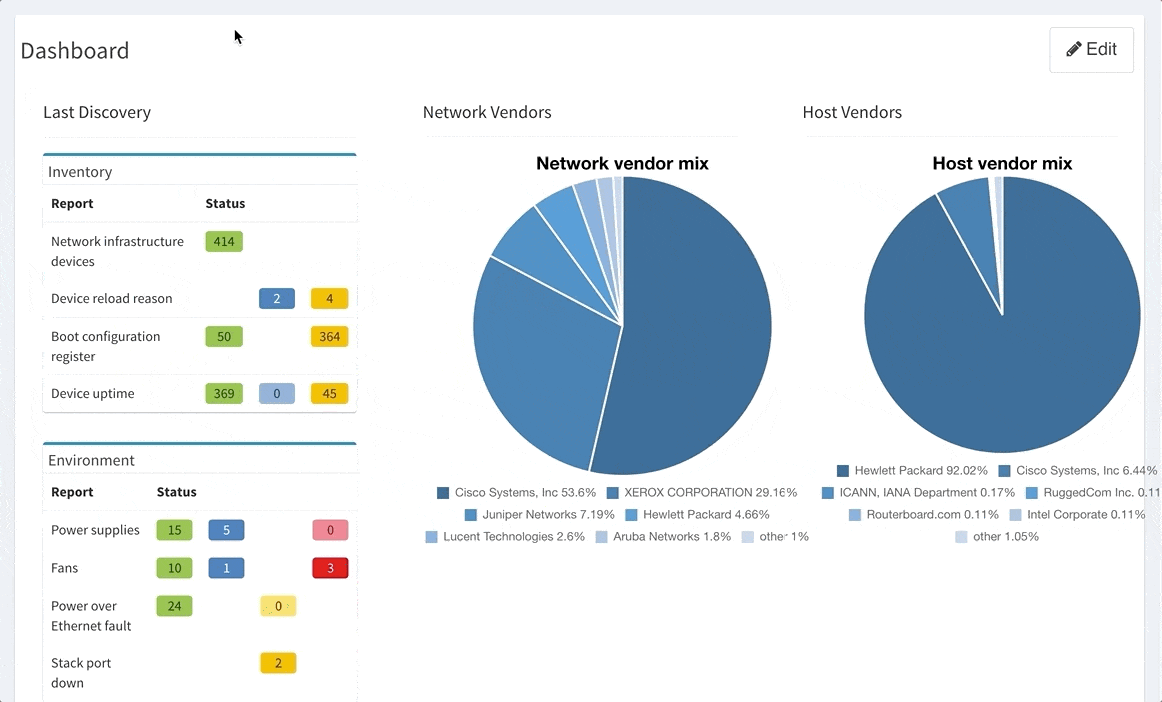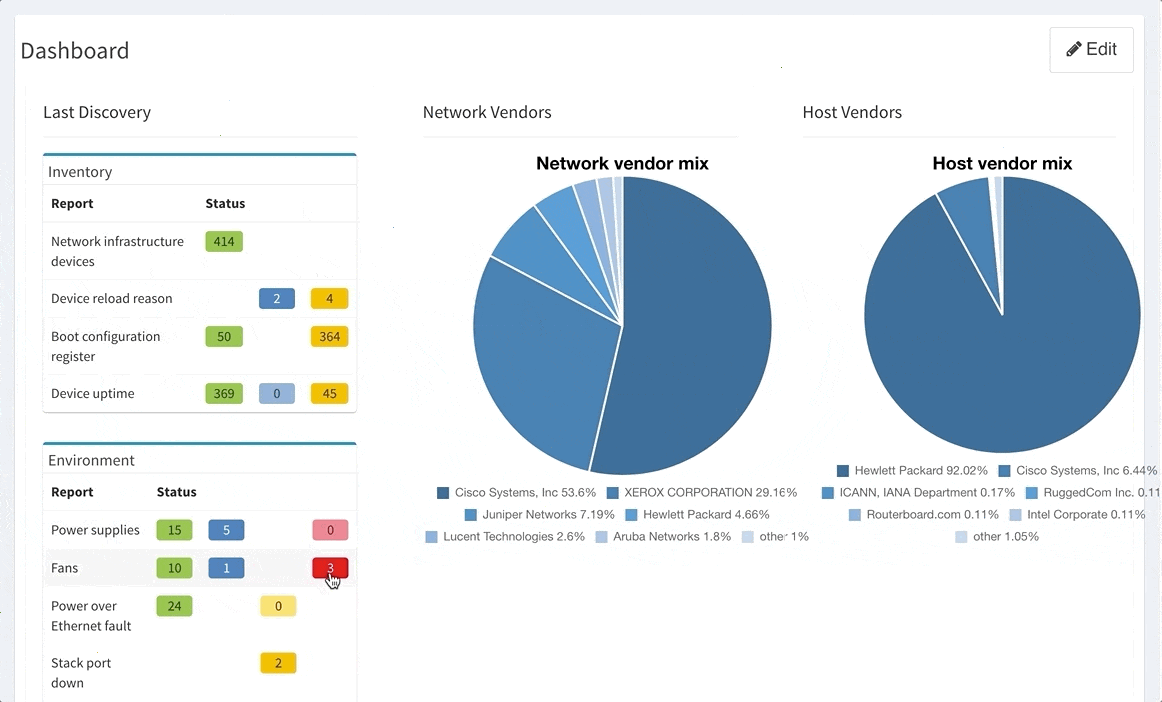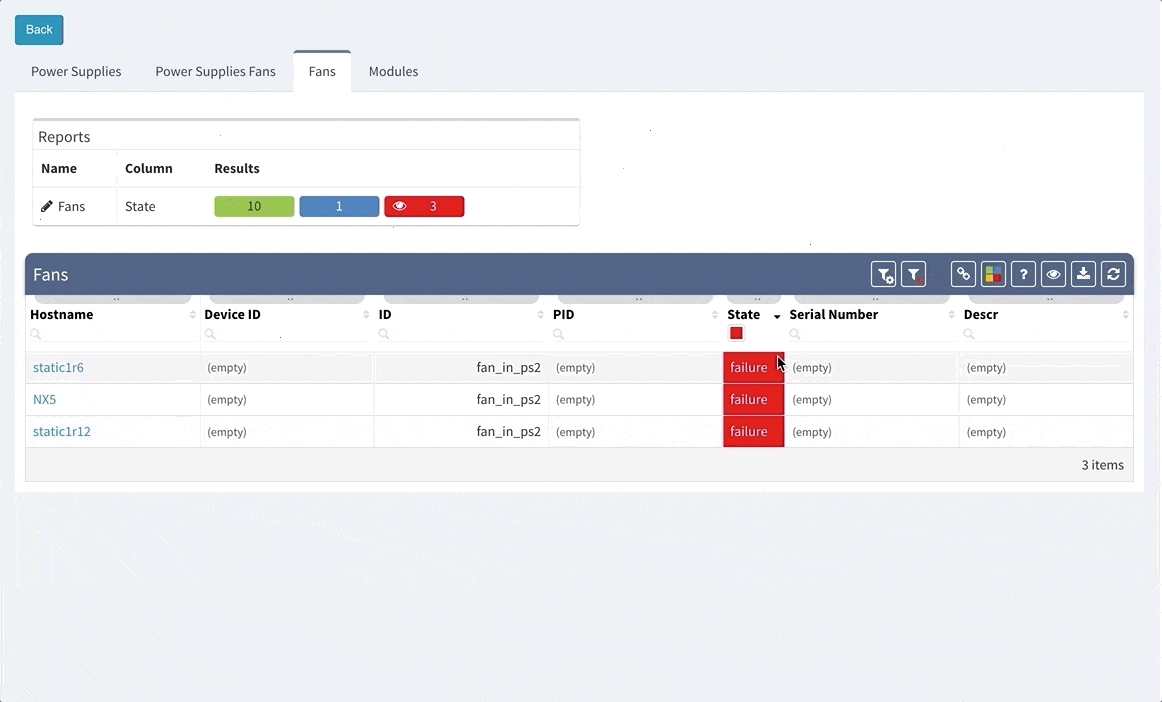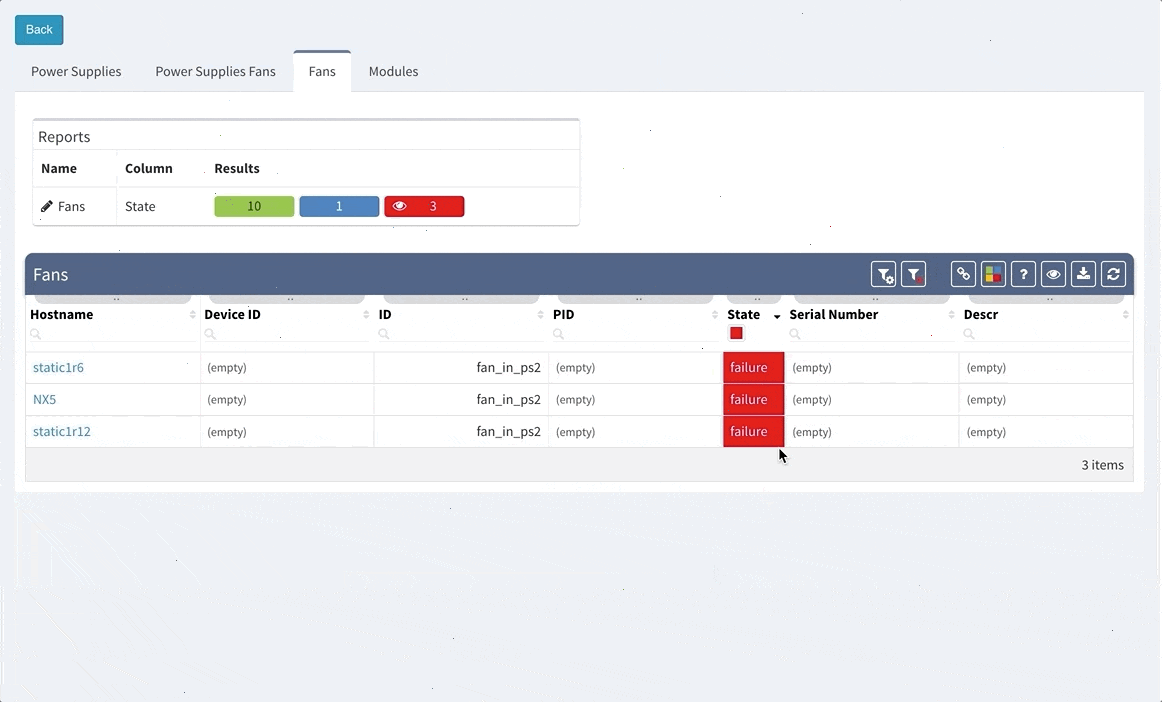
Last but not least, based on the feedback, we improved out-of-the-box verification reports to be more accurate and useful. In addition, we added DNS resolve support for the Connectivity report, which makes it easier identify the devices that have not been discovered properly.
If you’re interested in learning more about how IP Fabric’s platform can help you with analytics or intended network behavior reporting, contact us through our website, request a demo, follow this blog or sign up for our webinars.
Routing, one of the most important features in network world. It’s been at least a two decades since most of ISPs rely on Border Gateway Protocol (BGP) in their core, supported by Interior Gateway Protocols (IGP). Local area networks are running and routing with use of IGPs on their own and it’s already being utilized as an underlying protocol for other features like Virtual Extensible LANs and more. There’s no question that routing as a feature is holding technological world together, but as networks grow, it’s more and more obvious that administrator are more likely to miss an issue.
Command line interface is fast but when we try to see a bigger picture, we can easily miss the point while interacting with ten routers at once. That’s why routing protocol visualization itself become one of the most wanted features in IP Fabric since its start.
Routing table discovery has been implemented for a long time now and it’s not what will be discussed. Very recently we have been working on various parameters discovery for routing protocols, it started with OSPF support, while RIP support is in progress (and yes it’s still out there), Cisco native EIGRP and of course BGP. All have full Virtual Routing and Forwarding (VRF) instances support, which makes it a much more powerful as a feature for larger networks. The very next in line may be IS-IS, but I don’t want to speculate for now.
Open Shortest Path First (OSPF) may be one of the most used IGP protocol at this time. Again, I haven’t seen all networks in the world but my guess is, it would be so. It’s very wide-spread within vendors, easy to implement. IP Fabric currently supports OSPF on Cisco, Juniper and HP/Comware all with VRF support. Let’s have a quick tour in our lab.
In our virtual lab environment we ran discovery from IP Fabric and if in search of OSPF data, the best is to visit Technology > Routing > OSPF from the left-side menu.
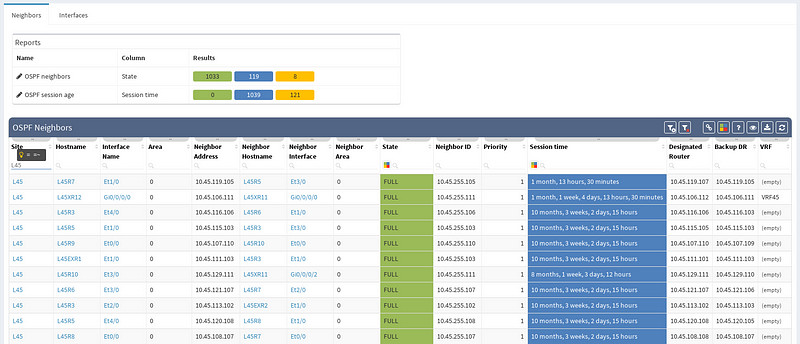
It’s very neat set of information, clear to all techs and the view is vendor neutral. For example the ‘Area’ information is formatted/translated to single integer, also for Juniper boxes where it’s standardly represented in IP/CIDR format. Again you can manipulate the view, remove or add columns or even change their order as you like, it’s all very flexible. Let’s switch to visual interpretation.
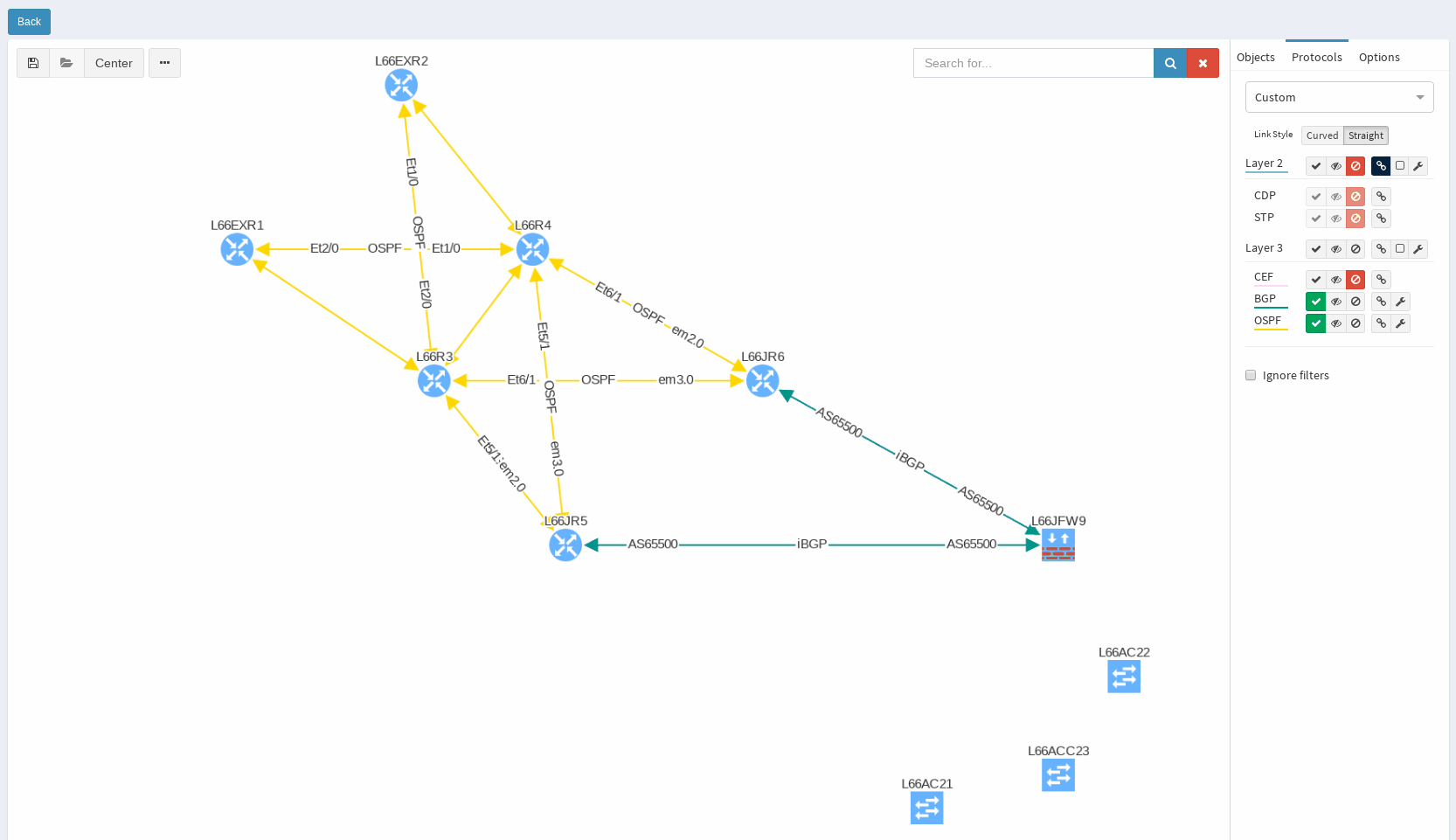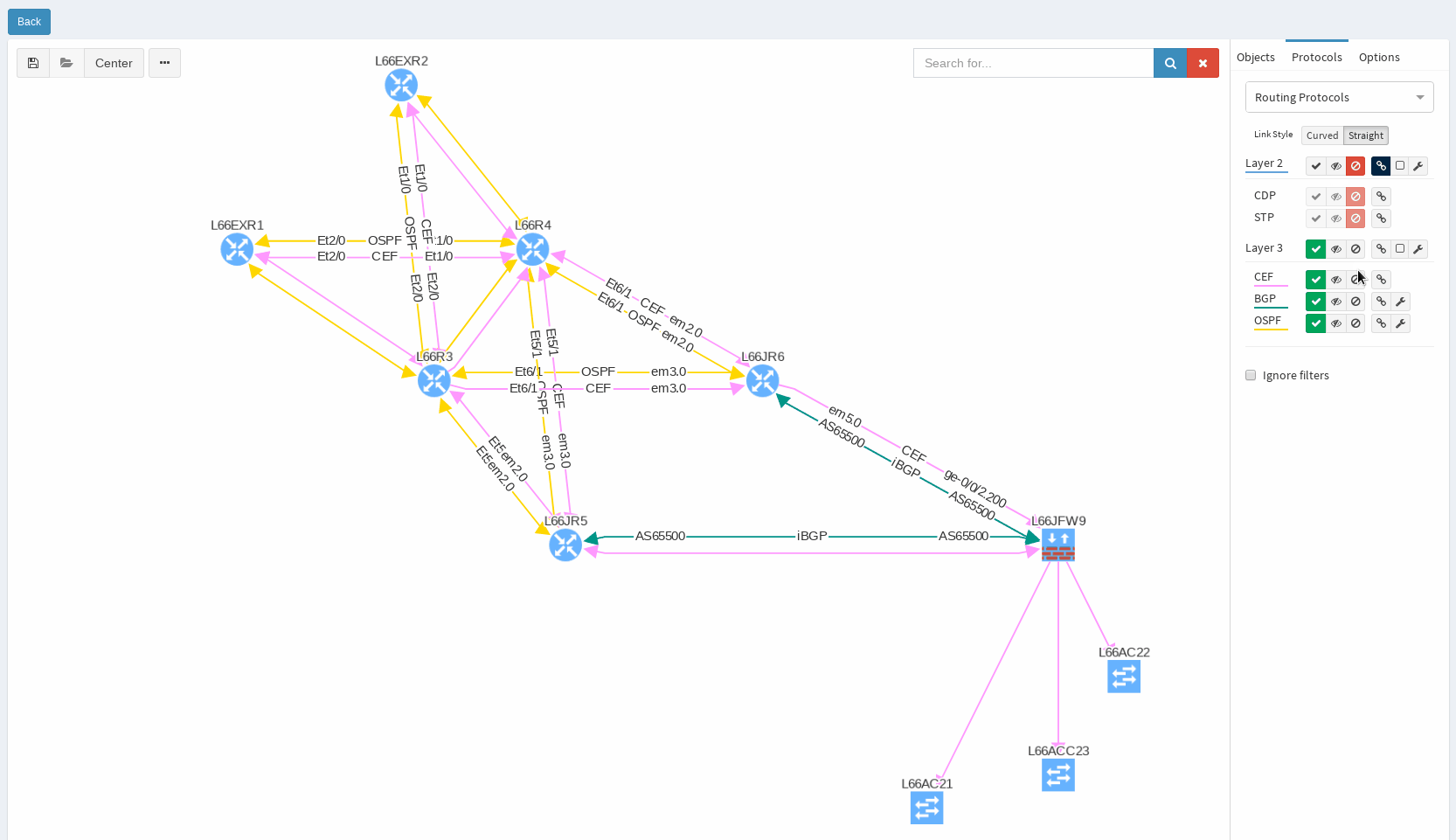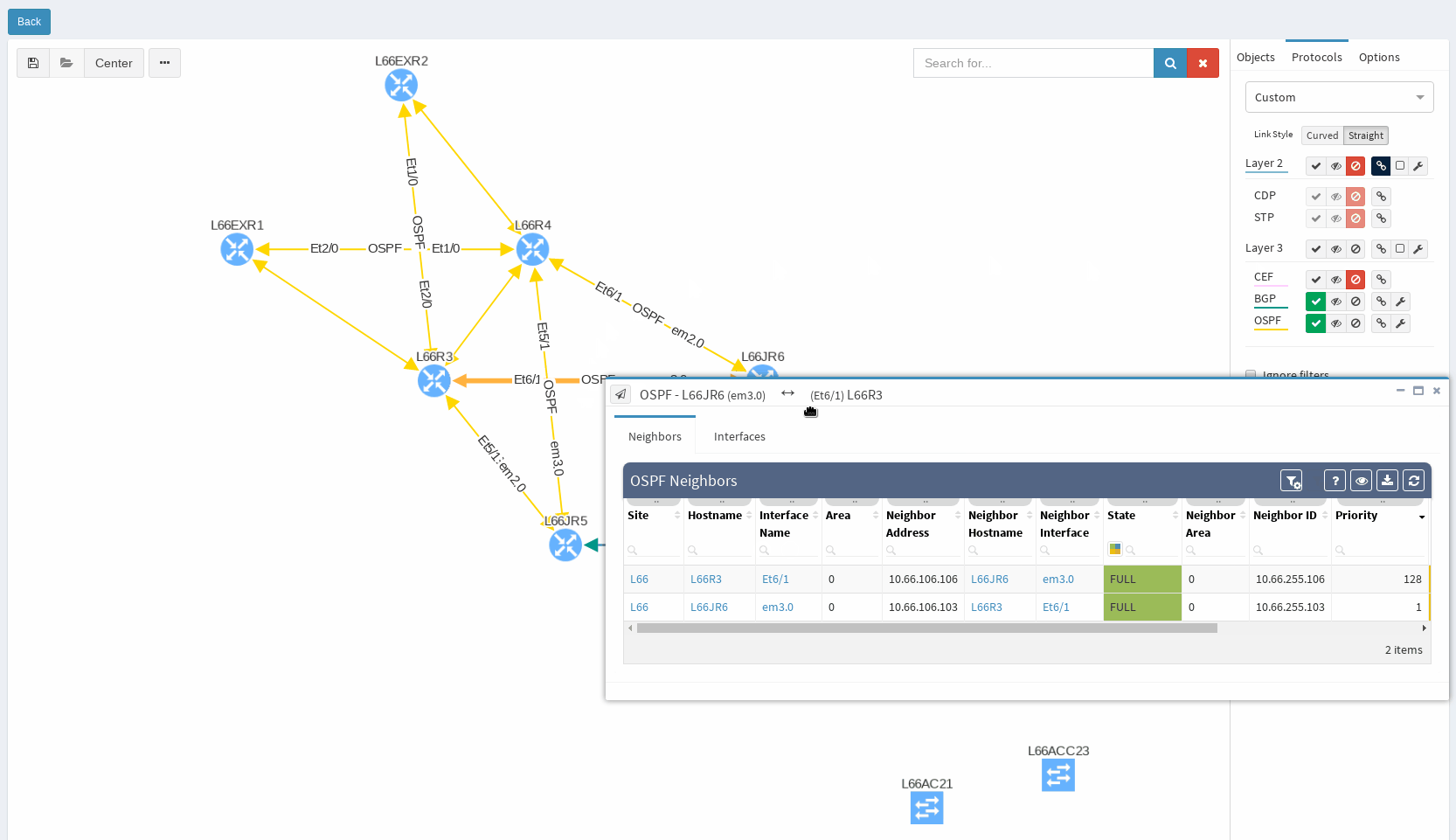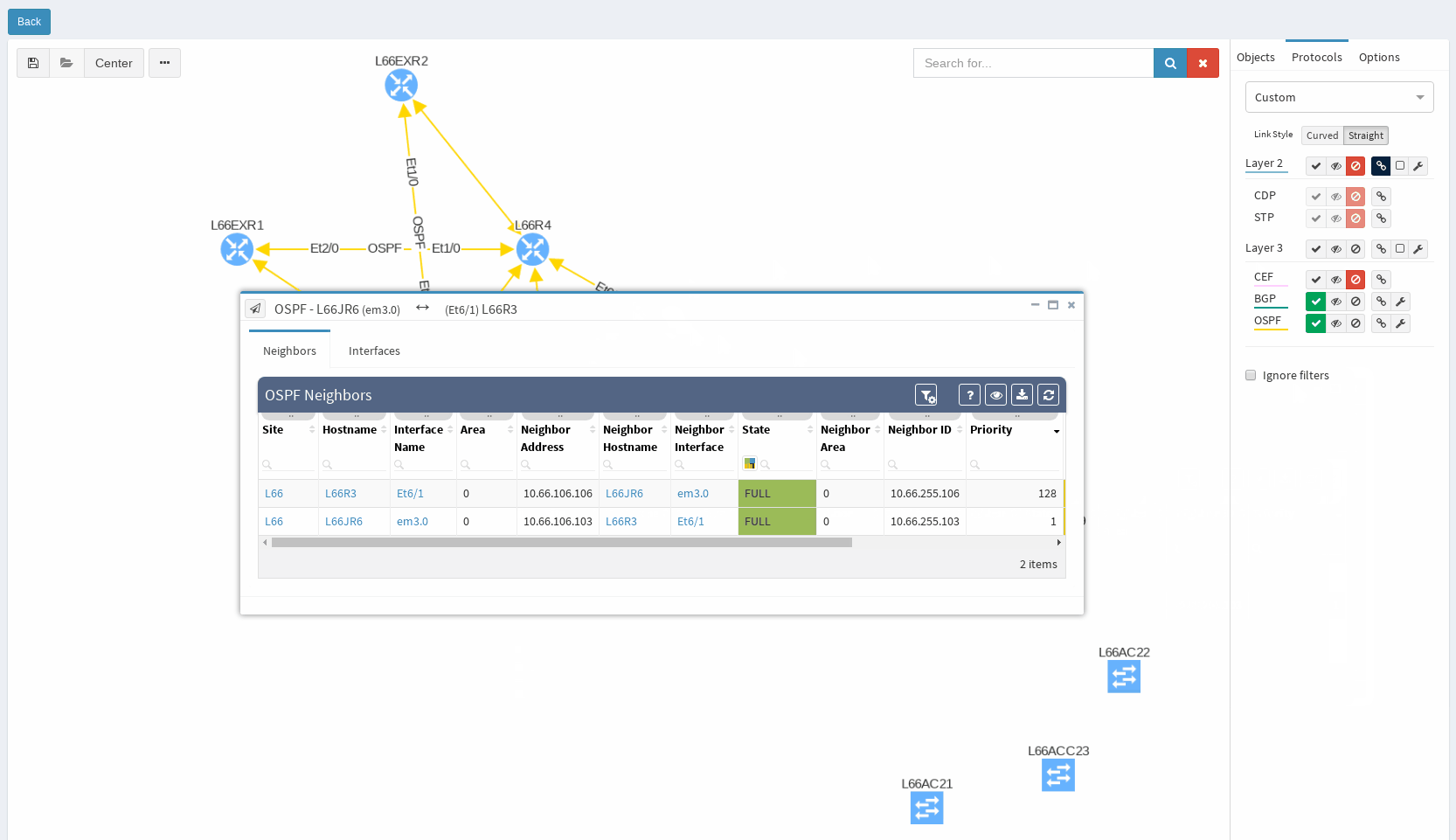
While in diagrams, all parameters pop-up as we need, those are the same as provided in OSPF neighbors table, but it’s filtered per diagram content. Same we can explore in BGP, we can even see Autonomous System numbers on connecting links. IP Fabric currently supports also site-to-site OSPF neighbourship when using tunnel interfaces of other technologies.
If you’re interested in learning more about how IP Fabric’s platform can help you with analytics or intended network behavior reporting, contact us through our website, request a demo, follow this blog or sign up for our webinars.


