This article was co-authored by Dan Kelcher, Solutions Architect at IP Fabric.
Congratulations, you've made it this far. You know what PCI compliance is, and why it is essential that your enterprise pass its compliance audit (covered in part 1). You now also know how to limit the scope of your upcoming audit to save you time, effort and a nasty headache thanks to the benefit of properly implemented network segmentation, aided by IP Fabric (covered in part 2). Surely it should be plain sailing now? Think again! Now you have to ensure that your enterprise network actually satisfies the 12 requirements set out by the PCI Security Standards Council (PCI SSC) in their Data Security Standards (PCI DSS).
As we have previously stated, IP Fabric can NOT help with all 12 requirements listed in the PCI DSS. What IP Fabric can do, however, is give you peace of mind and help you be sure that certain requirements are met. IP Fabric is a very useful tool that can help you at least partially cover some of these requirements. When utilized together with other means, you can be sure that you aren't left in the dark about your own network.
In this piece, we will begin to dive into how IP Fabric can be leveraged to cover some of the PCI DSS requirements by providing you with a complete network inventory, and an up-to-date visual representation of your network estate. Let's get into it!
The PCI DSS requirements relating to inventory are covered in point 12. It does seem odd to start with the last of the 12 requirements for PCI compliance, but ensuring you have the relevant, up-to-date documentation of your network inventory and end of life plans is essential to consider first. Doing so allows you to avoid any nasty surprises down the line. It's kind of like owning a house and trying to keep it secure from intruders. You need to know all of the access points in the house, and you can't lock a door that you don't know that you have.
Requirement 12.3.4 requires enterprises to review their in-use hardware and software technologies once every 12 months. This includes ensuring that the technologies receive security fixes from vendors, whilst continuing to support PCI DSS compliance, and that end of life (EoL) plans for technologies are in place. These plans also need to be documented and approved by senior management.
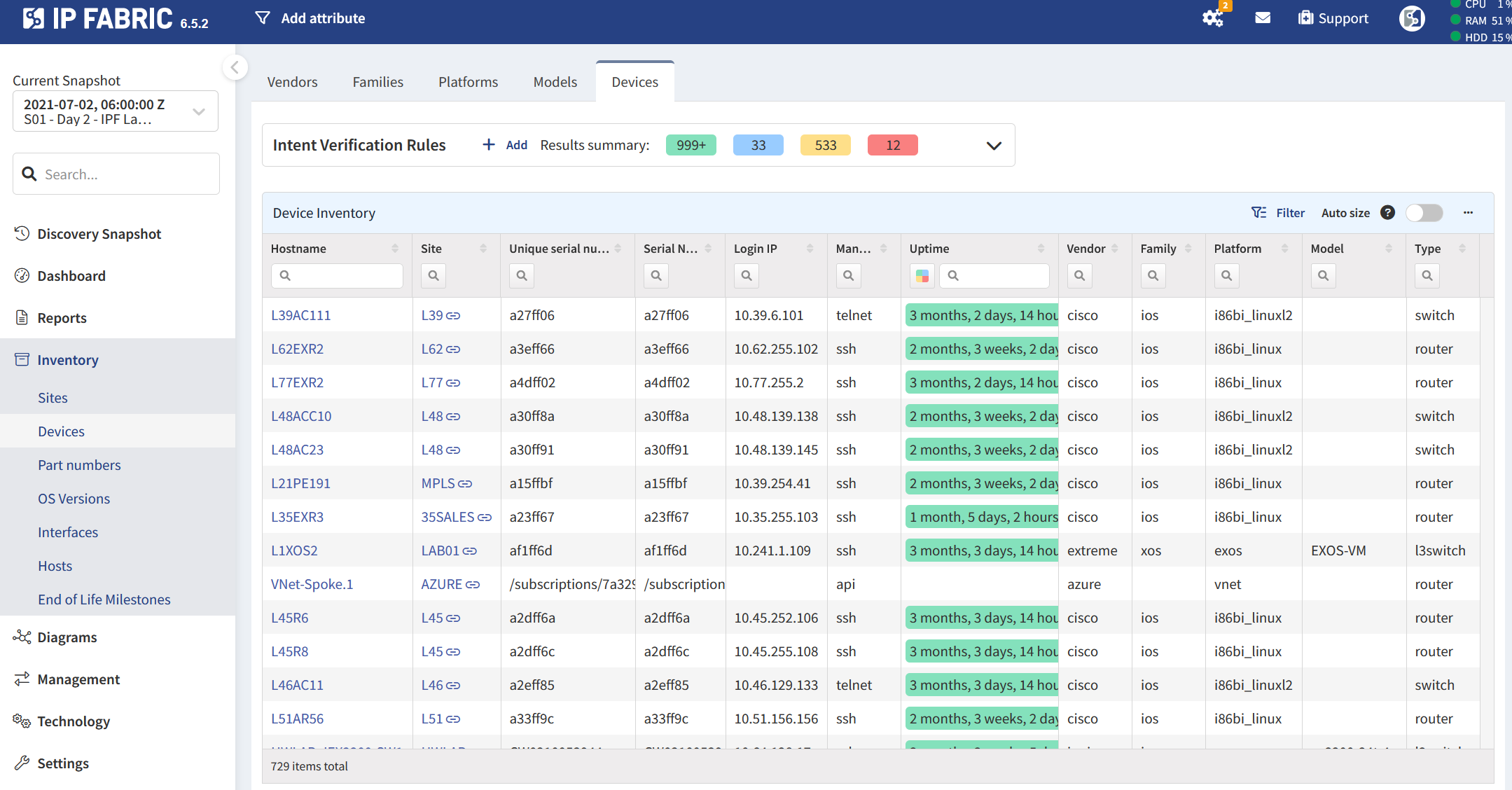
Requirement 12.5.1 obliges enterprises to have an inventory of system components that are in scope for PCI DSS, (including descriptions of their function/use), which is maintained and kept current. System components are defined as network devices, servers, computing device, virtual components (virtual machines, switches, routers etc.) as well as cloud components and software.
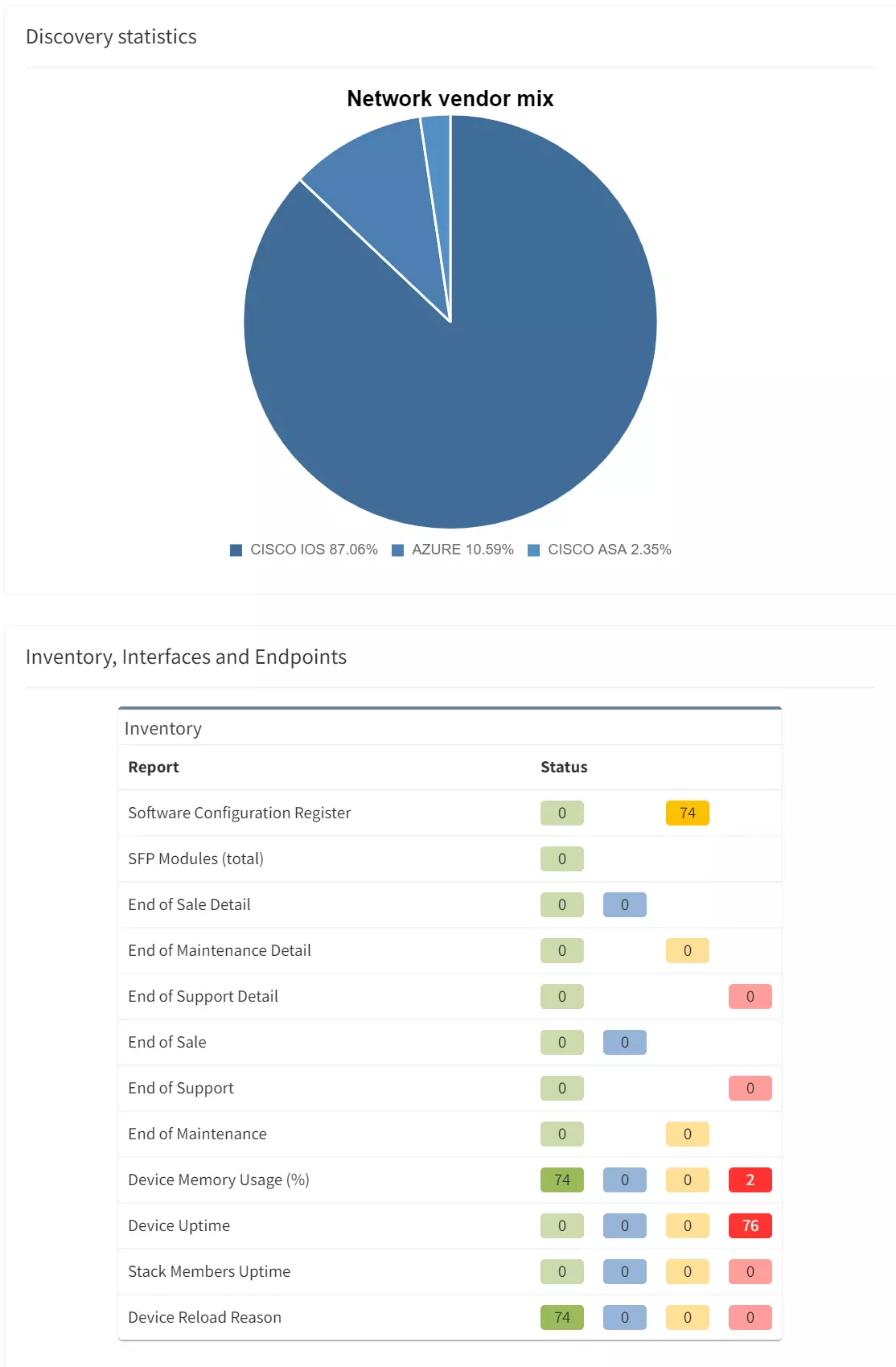
12.3.4 - During the discovery process, IP Fabric connects to supported network devices (there are hundreds of supported models across dozens of vendors) to collect configuration and state data, including make, model, and serial number. This is then compared against published EoL data from the hardware manufacturer.
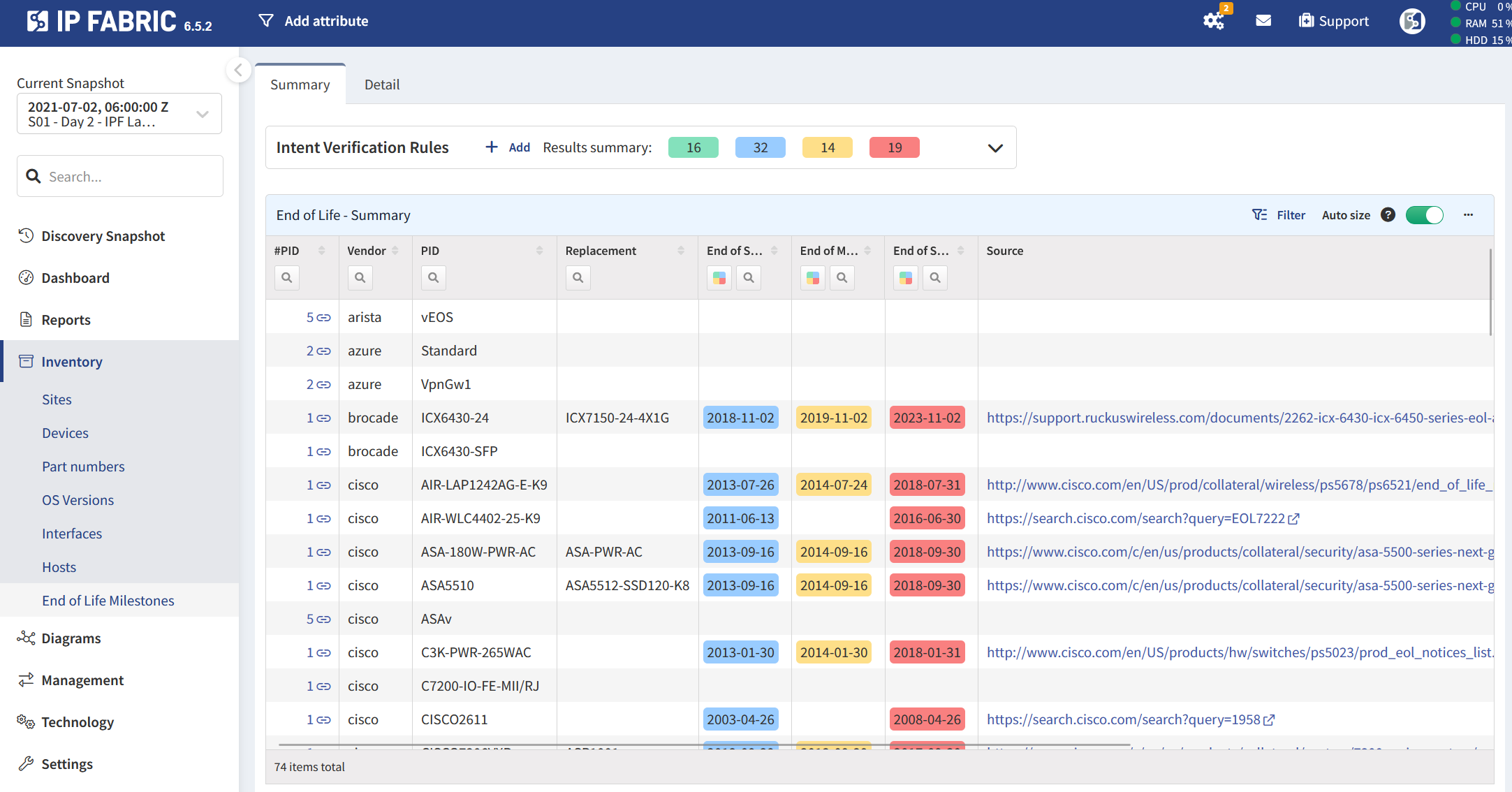
Published end of life data from several hardware manufacturers is included and updated per new IP Fabric releases to show the EoL status across the environment. With the information made readily available, you can begin to plan lifecycle management for your hardware. IP Fabric can help you formulate your plans by giving you the necessary information that you need.
Our platform can even help you take your lifecycle management planning to the next level. Wherever possible, the data presented in our platform will include vendor suggested replacements, meaning that you not only know when system components will reach end of life, but you also have the necessary information to ensure replacing them is as seamless as possible, and doesn't leave any gaps in your network.
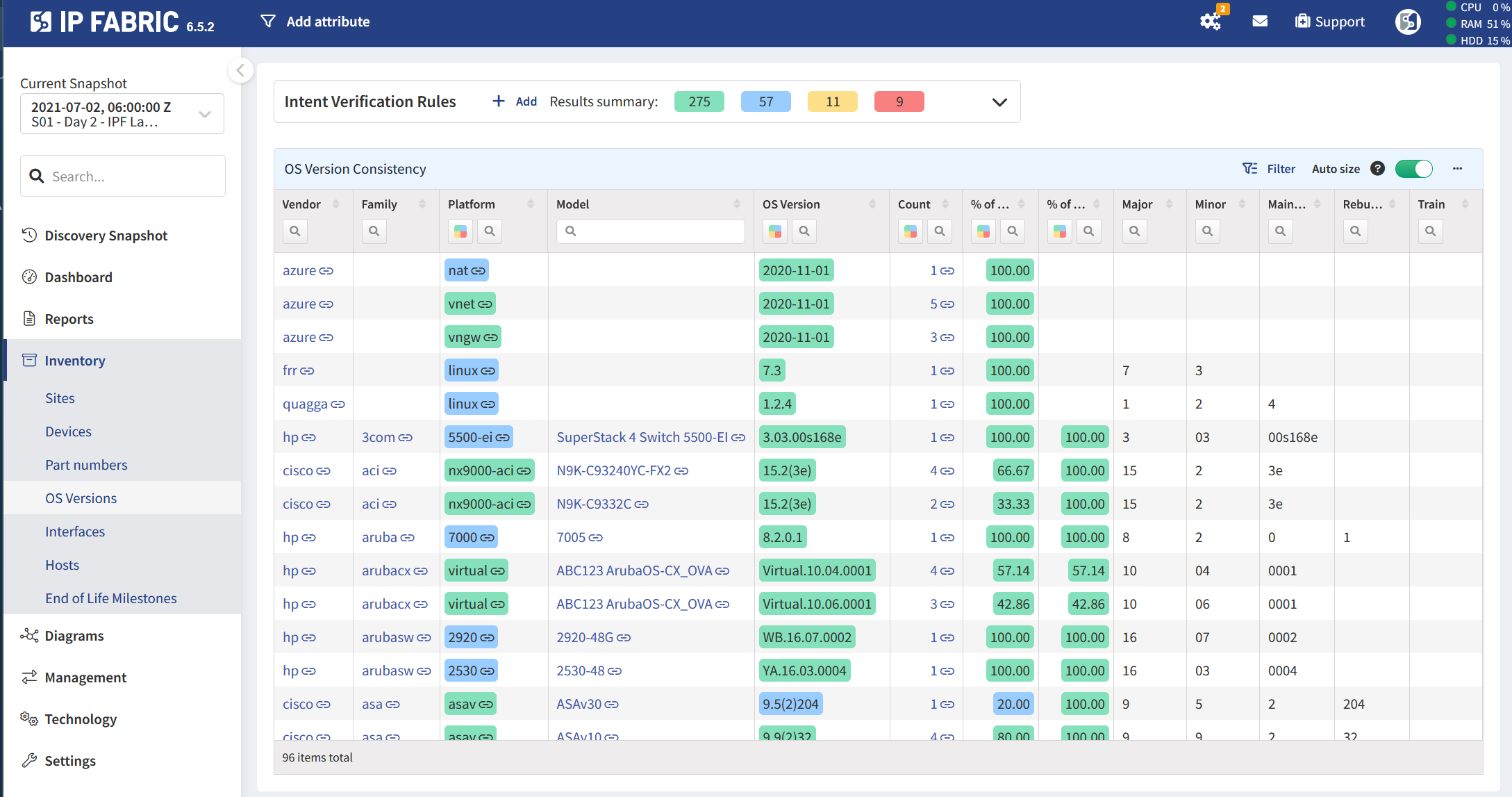
In addition to hardware information, software data is also collected. One of the most crucial features of IP Fabric is the ability to create intent rules. Intent rules can check to identify potential outliers or problematic areas within your network. An example of this would be to find what percentage of devices are running the same OS version. This could identify if OS updates aren’t being consistently applied, or if a device is running a version that hasn’t been validated. The intent rules feature will be covered in more detail in a future entry in this series!
12.5.1 - This one seems a little obvious given the nature of our platform. The snapshots that you can take using IP Fabric can be configured with granular scheduling, which might be at the start and end of standard maintenance windows, or at any other interval required. If a change occurs outside of a normal maintenance period, a snapshot can be manually created. The result is your diagrams are accurate at all times, ensuring that the inventory is "maintained and kept current', as stipulated by the PCI DSS.
Once you have taken a complete inventory of your network with IP Fabric, you can then move on to building a topology of your network. To accomplish this, IP Fabric uses state information learned from each device to build out the topology diagrams dynamically. The data can be used to path trace through your network to identify potential issues regarding your card data environment (CDE) - We will cover IP Fabric's path tracing capabilities and how they relate to PCI compliance in a future entry in this series. For now, the PCI DSS requirements relating to topology are contained in requirement 1.
Requirement 1.2.3 states that enterprises must maintain an "accurate network diagram" that shows all of the connections between the CDE and other networks, including wireless networks. 1.2.3.b also requires enterprises to verify that documentation and network diagrams are accurate and updated when there are changes to the environment.
Requirement 1.2.4 posits that enterprises possess an accurate data-flow diagram, maintained to meet the following: a) It shows all account data flows across systems and networks, and b) it is updated as needed upon changes to the environment.
1.2.3 - The snapshot process of IP Fabric discovers your network, then allows you to visualize your network in topological diagrams. Leveraging data from both Layer 2 (CDP, LLDP and MAC address tables) and Layer 3 (routing and ARP tables) protocols, IP Fabric builds a full view of the network. The output of this is a dynamic logical diagram that shows not only Layer 1 connectivity, but also Layer 2 and Layer 3 topology.
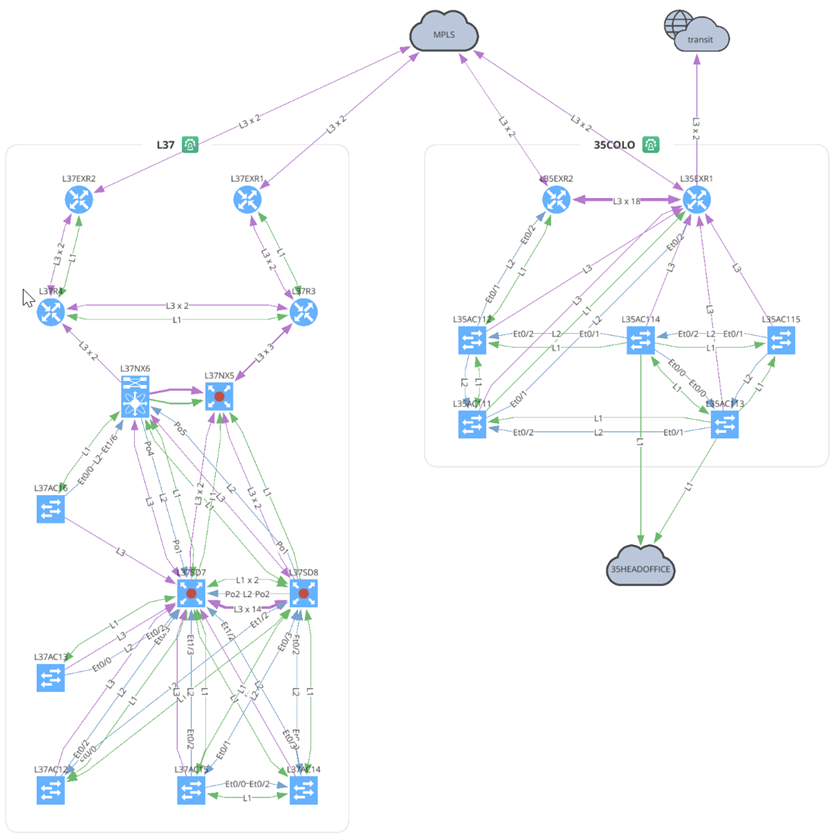
1.2.3.b - Here is another requirement that documentation and network diagrams be accurate. The dynamic nature of IP Fabric’s snapshot-based system ensures that network diagrams are regularly updated. This can be as often as the snapshots are scheduled to occur, or if a more current update is needed, a new manual snapshot can be performed, or individual devices can be refreshed in an existing snapshot. Additionally, a comparison can be performed to identify any topology changes that may have occurred between two snapshots.
1.2.4 – Provide the platform with a source and a destination, and IP Fabric can show the path taken through the network. These can be generated on-demand, or they can be configured to run automatically when new snapshots are created. We will cover this in more detail in a future entry in this series, but it is also worth noting here.
IP Fabric’s discovery and snapshot feature can be used to ensure that some of the essential PCI DSS requirements are satisfied before your next audit, by arming you with the essential information you need regarding your network inventory and topology. Whilst these capabilities only touch on some of the PCI DSS requirements, the ability to visualize your network estate is something we consider invaluable, especially with a PCI compliance audit on the horizon!
Check back soon for part 4 of our in-depth analysis on IP Fabric and PCI compliance, where we will cover how IP Fabric’s path tracing capabilities can be leveraged to cover more PCI DSS requirements. Feel free to follow us on LinkedIn, or on our blog, where new content will be emerging regularly. To find out more about how IP Fabric can help you take your network operations to the next level, request a demo here.
This article was co-authored by Dan Kelcher, Solutions Architect at IP Fabric.
This article was co-authored by Dan Kelcher, Solutions Architect at IP Fabric.
Congratulations, you've made it this far. You know what PCI compliance is, and why it is essential that your enterprise pass its compliance audit (covered in part 1). You now also know how to limit the scope of your upcoming audit to save you time, effort and a nasty headache thanks to the benefit of properly implemented network segmentation, aided by IP Fabric (covered in part 2). Surely it should be plain sailing now? Think again! Now you have to ensure that your enterprise network actually satisfies the 12 requirements set out by the PCI Security Standards Council (PCI SSC) in their Data Security Standards (PCI DSS).
As we have previously stated, IP Fabric can NOT help with all 12 requirements listed in the PCI DSS. What IP Fabric can do, however, is give you peace of mind and help you be sure that certain requirements are met. IP Fabric is a very useful tool that can help you at least partially cover some of these requirements. When utilized together with other means, you can be sure that you aren't left in the dark about your own network.
In this piece, we will begin to dive into how IP Fabric can be leveraged to cover some of the PCI DSS requirements by providing you with a complete network inventory, and an up-to-date visual representation of your network estate. Let's get into it!
The PCI DSS requirements relating to inventory are covered in point 12. It does seem odd to start with the last of the 12 requirements for PCI compliance, but ensuring you have the relevant, up-to-date documentation of your network inventory and end of life plans is essential to consider first. Doing so allows you to avoid any nasty surprises down the line. It's kind of like owning a house and trying to keep it secure from intruders. You need to know all of the access points in the house, and you can't lock a door that you don't know that you have.
Requirement 12.3.4 requires enterprises to review their in-use hardware and software technologies once every 12 months. This includes ensuring that the technologies receive security fixes from vendors, whilst continuing to support PCI DSS compliance, and that end of life (EoL) plans for technologies are in place. These plans also need to be documented and approved by senior management.
Requirement 12.5.1 obliges enterprises to have an inventory of system components that are in scope for PCI DSS, (including descriptions of their function/use), which is maintained and kept current. System components are defined as network devices, servers, computing device, virtual components (virtual machines, switches, routers etc.) as well as cloud components and software.
12.3.4 - During the discovery process, IP Fabric connects to supported network devices (there are hundreds of supported models across dozens of vendors) to collect configuration and state data, including make, model, and serial number. This is then compared against published EoL data from the hardware manufacturer.

Published end of life data from several hardware manufacturers is included and updated per new IP Fabric releases to show the EoL status across the environment. With the information made readily available, you can begin to plan lifecycle management for your hardware. IP Fabric can help you formulate your plans by giving you the necessary information that you need.
Our platform can even help you take your lifecycle management planning to the next level. Wherever possible, the data presented in our platform will include vendor suggested replacements, meaning that you not only know when system components will reach end of life, but you also have the necessary information to ensure replacing them is as seamless as possible, and doesn't leave any gaps in your network.

In addition to hardware information, software data is also collected. One of the most crucial features of IP Fabric is the ability to create intent rules. Intent rules can check to identify potential outliers or problematic areas within your network. An example of this would be to find what percentage of devices are running the same OS version. This could identify if OS updates aren’t being consistently applied, or if a device is running a version that hasn’t been validated. The intent rules feature will be covered in more detail in a future entry in this series!

12.5.1 - This one seems a little obvious given the nature of our platform. The snapshots that you can take using IP Fabric can be configured with granular scheduling, which might be at the start and end of standard maintenance windows, or at any other interval required. If a change occurs outside of a normal maintenance period, a snapshot can be manually created. The result is your diagrams are accurate at all times, ensuring that the inventory is "maintained and kept current', as stipulated by the PCI DSS.
Once you have taken a complete inventory of your network with IP Fabric, you can then move on to building a topology of your network. To accomplish this, IP Fabric uses state information learned from each device to build out the topology diagrams dynamically. The data can be used to path trace through your network to identify potential issues regarding your card data environment (CDE) - We will cover IP Fabric's path tracing capabilities and how they relate to PCI compliance in a future entry in this series. For now, the PCI DSS requirements relating to topology are contained in requirement 1.
Requirement 1.2.3 states that enterprises must maintain an "accurate network diagram" that shows all of the connections between the CDE and other networks, including wireless networks. 1.2.3.b also requires enterprises to verify that documentation and network diagrams are accurate and updated when there are changes to the environment.
Requirement 1.2.4 posits that enterprises possess an accurate data-flow diagram, maintained to meet the following: a) It shows all account data flows across systems and networks, and b) it is updated as needed upon changes to the environment.
1.2.3 - The snapshot process of IP Fabric discovers your network, then allows you to visualize your network in topological diagrams. Leveraging data from both Layer 2 (CDP, LLDP and MAC address tables) and Layer 3 (routing and ARP tables) protocols, IP Fabric builds a full view of the network. The output of this is a dynamic logical diagram that shows not only Layer 1 connectivity, but also Layer 2 and Layer 3 topology.

1.2.3.b - Here is another requirement that documentation and network diagrams be accurate. The dynamic nature of IP Fabric’s snapshot-based system ensures that network diagrams are regularly updated. This can be as often as the snapshots are scheduled to occur, or if a more current update is needed, a new manual snapshot can be performed, or individual devices can be refreshed in an existing snapshot. Additionally, a comparison can be performed to identify any topology changes that may have occurred between two snapshots.
1.2.4 – Provide the platform with a source and a destination, and IP Fabric can show the path taken through the network. These can be generated on-demand, or they can be configured to run automatically when new snapshots are created. We will cover this in more detail in a future entry in this series, but it is also worth noting here.
IP Fabric’s discovery and snapshot feature can be used to ensure that some of the essential PCI DSS requirements are satisfied before your next audit, by arming you with the essential information you need regarding your network inventory and topology. Whilst these capabilities only touch on some of the PCI DSS requirements, the ability to visualize your network estate is something we consider invaluable, especially with a PCI compliance audit on the horizon!
Check back soon for part 4 of our in-depth analysis on IP Fabric and PCI compliance, where we will cover how IP Fabric’s path tracing capabilities can be leveraged to cover more PCI DSS requirements. Feel free to follow us on LinkedIn, or on our blog, where new content will be emerging regularly. To find out more about how IP Fabric can help you take your network operations to the next level, request a demo here.
This article was co-authored by Dan Kelcher, Solutions Architect at IP Fabric.