Co-authored by Solution Architect Dan Kelcher and content specialist Alex Bonehill
So, you have a PCI compliance audit looming in the near future - You know what the requirements are, as set out by the PCI DSS, and you are aware of the multitude of potential penalties if you can't prove that your system is compliant. So you should have all the information you need to pass this audit, right? Not exactly. When a PCI compliance audit is performed, every single part of your network which touches, stores, or processes sensitive cardholder data (CHD) and/or sensitive authentication data (SAD) needs to be audited. This includes any areas of your network that may impact the security of the environment storing CHD/SAD.
To be more precise, PCI DSS requirements apply to system components, people, and processes that store, process, and transmit CHD/SAD, as well as system components that might not store, process, or transmit CHD/SAD, but that have "unrestricted connectivity" to the components that do. System components, as defined by the PCI SSC, include network devices, servers, computing devices, virtual components (virtual machines, switches, routers etc.), as well as cloud components and software.

Therefore, knowing the 12 requirements and the litany of sub-requirements essential for PCI compliance is not necessarily enough - You need to know exactly what in your network is considered in-scope for the audit. But your network may contain tens of thousands of interconnected devices, paths and configurations. It could also span across multiple international locations being maintained by different teams, and there may be a massive group of people with access to segments housing CHD, some unnecessarily so. Sorting through all of this manually will surely result in a stress-induced migraine, and massive costs for your next audit.
It is essential that you know exactly how much of your network is subject to audit before it starts - It could be a lot more, or a lot less than you think. IP Fabric can help you to limit the scope of your next PCI compliance audit, thus limiting the complexity, time and cost of your upcoming assessment. Let us explain how.
When preparing for an audit, we have already established that knowing your network is essential, as it allows you to determine how much of your estate actually needs to be audited. To this end, there is one particular best practice to consider here, which is even included by the PCI SSC in its document on Security Standards - Network segmentation. Network segmentation is the practice of using device rules or ACLs to restrict connections and access between specific devices and services within the internal network.

By controlling how traffic flows through the paths of your network, you can achieve granular-level control and insight regarding your network. The uses of network segmentation include limiting the flow within your network by source, destination, or by traffic type. When dealing with the CHD environment in your network, using segmentation means a reduction in the number of users and devices that would have access to segments on which CHD is stored.
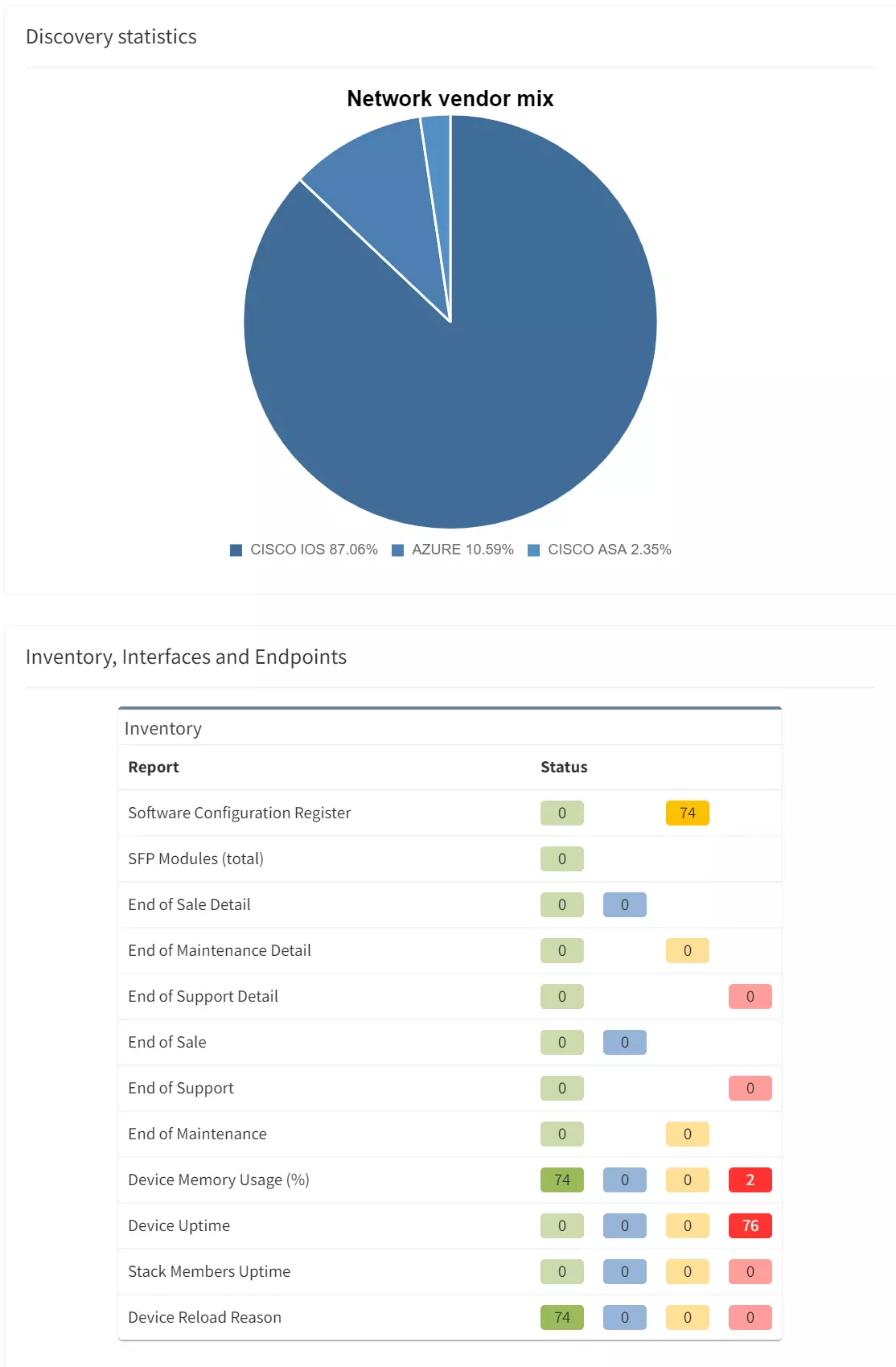
IP Fabric's comprehensive discovery feature allows you to visualize your entire network estate through topological diagrams, which can be viewed on different protocol levels. The feature utilizes snapshots, either scheduled, or on-demand, to discover the devices and applications within your network and how they are connected to each other. This feature can also be used to simulate entire end-to-end paths.
During the discovery process, IP Fabric connects to switchers, routers and firewalls and, based on state information, understands how devices are connected. Additionally, IP Fabric is able to interpret the rules applied to these connections, allowing for end-to-end simulation of traffic flows through the network.
Having access to the state information, topology and rulesets of your network, you can specify any network or device in the environment and identify if it is capable of accessing a destination which stores CHD/SAD. This allows you to validate whether the CHD environment is sufficiently isolated from the rest of your network. If so, these isolated areas do not needs to be audited. If the areas of your network that do house CHD are not sufficiently isolated from your other network components, then you have all the information you need to implement proper network segmentation, thanks to IP Fabric.
This last point, that is, the ability to validate the effectiveness of your network segmentation and adjust it accordingly, is particularly helpful when considering that a PCI compliance audit includes an examination of the segmentation implemented in a network. Using IP Fabric, you can not only limit the scope of your assessment, but also validate that you really are covered with effective segmentation, avoiding any nasty surprises come auditing time.
Identifying the network segments that store CHD also limits the number of people within an organization that need to be audited - The process of limiting the number of people subject to a PCI compliance audit is sometimes referred to as "descoping". Without IP Fabric, the cost of a compliance audit could be astronomical, given that you may not have a way of proving who has access to which parts of your network. If you can't say with certainty that a particular person DOESN'T have access, then they will be included in the audit for the sake of avoiding a potential, unnecessary data breach or running an incomplete assessment.

Unsure of whether your access restrictions are sufficiently configured or deployed correctly? The data collected from your network by IP Fabric includes the behavior of interconnection points between network segments and the deployed policy - The data collected can be viewed in tabular form or path lookup simulation to ensure data is flowing through these enforcement points as planned. The data is also accessible via API, which can be integrate into other tools.
Leveraging single sign-on (SSO) and role-based access control (RBAC), granular permissions to view this data can be applied to anyone in an organization, opening the door for data democratization. You can ensure that the relevant people are able to keep up to date on whether your network is correctly segmented with the appropriate level of security, ensuring that you can be certain regarding what is in, or out, of scope for your next audit.
Check back soon for part 3 of our in-depth analysis on IP Fabric and PCI Compliance, where we will cover the PCI DSS requirements that IP Fabric can lend a helping hand to.
Follow us on LinkedIn or on our blog, where new content is emerging regularly. To find out more about how IP Fabric can give you and your business peace of mind, request a demo here.
Co-authored by Solution Architect Dan Kelcher and content specialist Alex Bonehill
So, you have a PCI compliance audit looming in the near future - You know what the requirements are, as set out by the PCI DSS, and you are aware of the multitude of potential penalties if you can't prove that your system is compliant. So you should have all the information you need to pass this audit, right? Not exactly. When a PCI compliance audit is performed, every single part of your network which touches, stores, or processes sensitive cardholder data (CHD) and/or sensitive authentication data (SAD) needs to be audited. This includes any areas of your network that may impact the security of the environment storing CHD/SAD.
To be more precise, PCI DSS requirements apply to system components, people, and processes that store, process, and transmit CHD/SAD, as well as system components that might not store, process, or transmit CHD/SAD, but that have "unrestricted connectivity" to the components that do. System components, as defined by the PCI SSC, include network devices, servers, computing devices, virtual components (virtual machines, switches, routers etc.), as well as cloud components and software.

Therefore, knowing the 12 requirements and the litany of sub-requirements essential for PCI compliance is not necessarily enough - You need to know exactly what in your network is considered in-scope for the audit. But your network may contain tens of thousands of interconnected devices, paths and configurations. It could also span across multiple international locations being maintained by different teams, and there may be a massive group of people with access to segments housing CHD, some unnecessarily so. Sorting through all of this manually will surely result in a stress-induced migraine, and massive costs for your next audit.
It is essential that you know exactly how much of your network is subject to audit before it starts - It could be a lot more, or a lot less than you think. IP Fabric can help you to limit the scope of your next PCI compliance audit, thus limiting the complexity, time and cost of your upcoming assessment. Let us explain how.
When preparing for an audit, we have already established that knowing your network is essential, as it allows you to determine how much of your estate actually needs to be audited. To this end, there is one particular best practice to consider here, which is even included by the PCI SSC in its document on Security Standards - Network segmentation. Network segmentation is the practice of using device rules or ACLs to restrict connections and access between specific devices and services within the internal network.

By controlling how traffic flows through the paths of your network, you can achieve granular-level control and insight regarding your network. The uses of network segmentation include limiting the flow within your network by source, destination, or by traffic type. When dealing with the CHD environment in your network, using segmentation means a reduction in the number of users and devices that would have access to segments on which CHD is stored.
IP Fabric's comprehensive discovery feature allows you to visualize your entire network estate through topological diagrams, which can be viewed on different protocol levels. The feature utilizes snapshots, either scheduled, or on-demand, to discover the devices and applications within your network and how they are connected to each other. This feature can also be used to simulate entire end-to-end paths.
During the discovery process, IP Fabric connects to switchers, routers and firewalls and, based on state information, understands how devices are connected. Additionally, IP Fabric is able to interpret the rules applied to these connections, allowing for end-to-end simulation of traffic flows through the network.
Having access to the state information, topology and rulesets of your network, you can specify any network or device in the environment and identify if it is capable of accessing a destination which stores CHD/SAD. This allows you to validate whether the CHD environment is sufficiently isolated from the rest of your network. If so, these isolated areas do not needs to be audited. If the areas of your network that do house CHD are not sufficiently isolated from your other network components, then you have all the information you need to implement proper network segmentation, thanks to IP Fabric.
This last point, that is, the ability to validate the effectiveness of your network segmentation and adjust it accordingly, is particularly helpful when considering that a PCI compliance audit includes an examination of the segmentation implemented in a network. Using IP Fabric, you can not only limit the scope of your assessment, but also validate that you really are covered with effective segmentation, avoiding any nasty surprises come auditing time.
Identifying the network segments that store CHD also limits the number of people within an organization that need to be audited - The process of limiting the number of people subject to a PCI compliance audit is sometimes referred to as "descoping". Without IP Fabric, the cost of a compliance audit could be astronomical, given that you may not have a way of proving who has access to which parts of your network. If you can't say with certainty that a particular person DOESN'T have access, then they will be included in the audit for the sake of avoiding a potential, unnecessary data breach or running an incomplete assessment.

Unsure of whether your access restrictions are sufficiently configured or deployed correctly? The data collected from your network by IP Fabric includes the behavior of interconnection points between network segments and the deployed policy - The data collected can be viewed in tabular form or path lookup simulation to ensure data is flowing through these enforcement points as planned. The data is also accessible via API, which can be integrate into other tools.
Leveraging single sign-on (SSO) and role-based access control (RBAC), granular permissions to view this data can be applied to anyone in an organization, opening the door for data democratization. You can ensure that the relevant people are able to keep up to date on whether your network is correctly segmented with the appropriate level of security, ensuring that you can be certain regarding what is in, or out, of scope for your next audit.
Check back soon for part 3 of our in-depth analysis on IP Fabric and PCI Compliance, where we will cover the PCI DSS requirements that IP Fabric can lend a helping hand to.
Follow us on LinkedIn or on our blog, where new content is emerging regularly. To find out more about how IP Fabric can give you and your business peace of mind, request a demo here.