There are likely a number of shiny strategies you'd like to implement to help drive better network decisions. The allure of easier infrastructure management, streamlined workflows, and happy, efficient teams keep you returning to these strategies, whether promised by vendors, espoused by thought leaders in trend reports, or heralded as the next big thing by network peers.
But when it comes to concrete network strategy that you can practically implement, grand ideas and bold philosophy quickly fall way to what is pragmatic. If you don't have a clearly defined game plan underpinning your mission, it's going to be tough convincing anyone to play your game.
Automated network assurance is one of these hard-to-pin-down terms. We at IP Fabric have been singing about it for years, and our experience in doing so is that everyone has their own criteria for what constitutes proper assurance of a network. Here, we're sharing our definition. We've drilled down into the practical, specific components, to help you map out your plan for a fully assured network.
Frankly speaking, there's also the option to toss out the map and let our automated network assurance platform deliver you the goods. If you're ready for that, book a tailored demo with our team, but ready or not, you should probably still know exactly what an automated network assurance platform should deliver. Read on!
To have a truly holistic view of the network, you need to have easy access to these five elements:

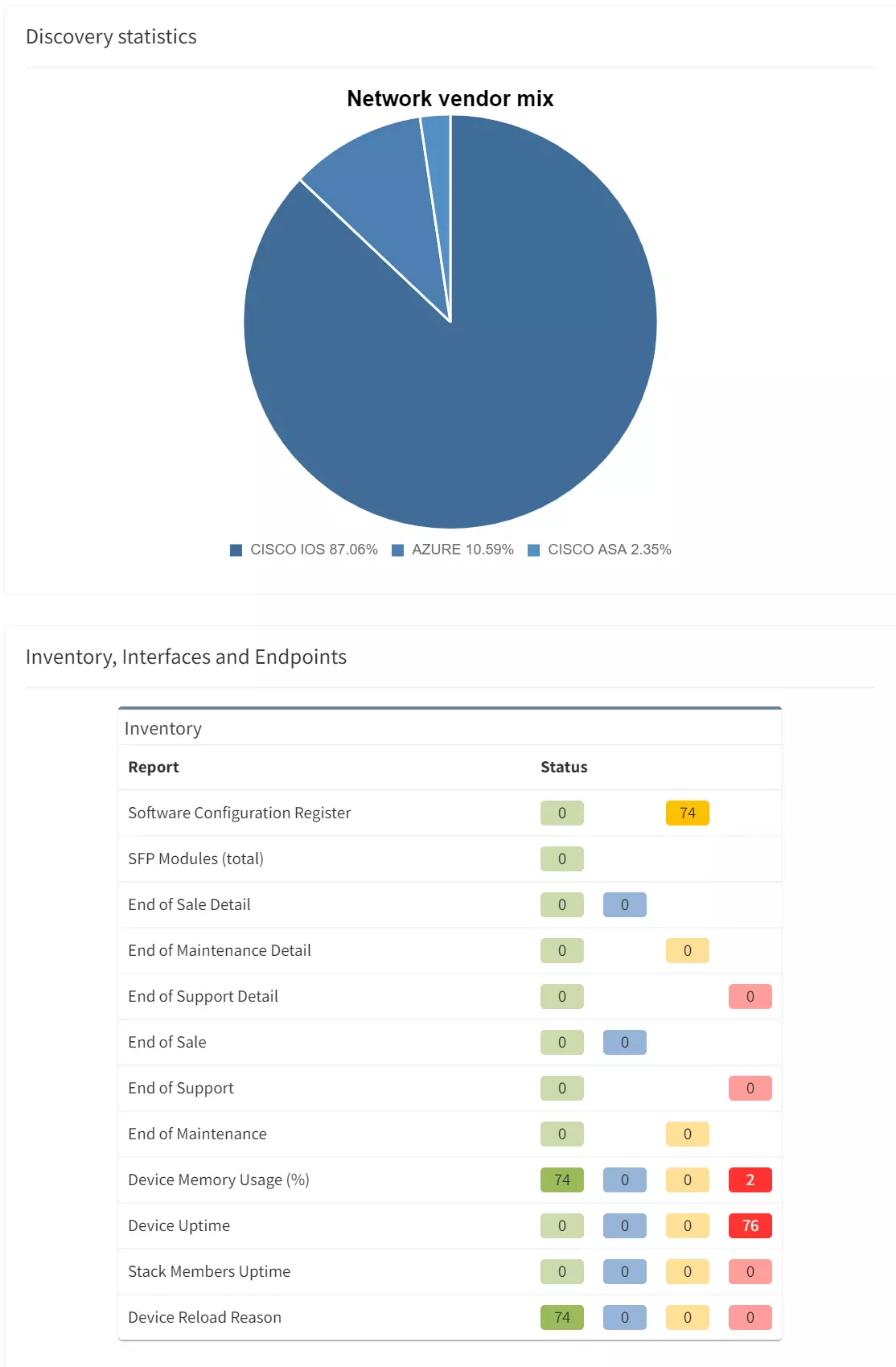
First up, you have to know - at any point in time - precisely which devices (what vendor, what model?) exist in your network, where they are located, and what code version is running on each device. Without this, anything else is purely a presumption.
Without automated network assurance: You can find and collate this information manually by consolidating disparate resources scattered across your organization, like your CMDB, spreadsheets, procurement systems, etcetera. If you're including static documents in this, it's likely they're outdated by the time you're using them to help centralize inventory information.
With automated network assurance: Every point-in-time network snapshot, taken on demand or as scheduled, contains network inventory information that has been acquired through lightweight, lightning-quick CLI-based discovery over Telnet, SSH or API.
It's essential to understand the desired configuration for your various network devices, and whether each device is actually configured according to the templates containing your intent.
Without automated network assurance: This lives in hand-built templates. If you're lucky, you have a configuration backup system. However, there's a good chance it may be incomplete or out of date.
With automated network assurance: Once again, configuration information is available automatically, acquired through lightweight, lightning-quick CLI-based discovery, and normalized for analysis. Built-in or custom intent checks also ensure you know about any misconfiguration present.
How is each device actually behaving at a particular point in time, and is it as you intended?
Without automated network assurance: There is not generally one place to go for this information; engineers have to manually mine this information by logging into each network device. This would only be done when troubleshooting involves a specific device; ultimately, a reactive approach.
With automated network assurance: This information is part of the discovery process and is included in an automatically generated network model. This means when reviewing, the state information sits alongside config info to give you a much more complete view of your network's behavior.
Using Inventory, Configuration, and State information, it's essential to draw out the layers of connectivity in your network, so you can understand the interconnectivity and different paths that data may take.
Without automated network assurance: This would be manually drawn by engineers who must investigate and gather information about the network from various disparate sources, using Visio or otherwise. Note that these are static, need maintenance, and do not represent the actual network state, only the expected state.
With automated network assurance: Topology maps of the whole network, including security information, are automatically generated. Note that these represent actual state at a particular point in time, which is very useful for comparing different snapshots for historical troubleshooting.
Without automated network assurance: To understand end-to-end behavior, engineers would have to look at different diagrams, and talk with different teams and people (e.g. security and cloud teams), cobbling together a view as best they can with what's available.
With automated network assurance: No patchworking needed. Ask your network anything! Run queries against this normalized data to see end-to-end paths of packets through the network, and understand the flow of a packet from endpoint to endpoint.
Having these five elements accessible and consumable in technology tables, dashboards, and topology maps forms your network baseline, and though this is really just the first step for companies adopting automated network assurance, it can be transformative.
For example, it's fairly common for IP Fabric customers to find previously unknown devices or misconfigurations in their network within an hour or so of kicking off their POC - that is, before full deployment in their network! With this evidence looking enterprise network leaders in the eye, it's tough to deny the value of automated network assurance.

Though a massive benefit, automating network assurance is not just a means to streamline operations and have faster access to network insights - it is essential to ensuring you have the right data, in a consumable manner.
In an enterprise environment, one could argue manual methods of collecting inventory, config, and state information, producing topologies and end-to-end paths will never be accurate or represent your actual network state, as the network is too dynamic.
So yes, technically, you could let your network teams run around collecting, collating, and visualizing this data manually, but it's likely a waste of their hard work and talent, as the results will never be that useful in a constantly changing network. Automating this, on the other hand, usually has surprising results beyond the expected benefits, as engineers have the capacity to be creative with network data and reimagine their approach to network operations.
Follow us on LinkedIn, and on our blog, where we regularly publish new content. Want to find out for yourself how IP Fabric can help you to revolutionize your networking operations and processes? Request a demo here.
Will you be at Cisco Live 2023? Let us know, and book some time with our team! Click below to see what Cisco Live means to us.

There are likely a number of shiny strategies you'd like to implement to help drive better network decisions. The allure of easier infrastructure management, streamlined workflows, and happy, efficient teams keep you returning to these strategies, whether promised by vendors, espoused by thought leaders in trend reports, or heralded as the next big thing by network peers.
But when it comes to concrete network strategy that you can practically implement, grand ideas and bold philosophy quickly fall way to what is pragmatic. If you don't have a clearly defined game plan underpinning your mission, it's going to be tough convincing anyone to play your game.
Automated network assurance is one of these hard-to-pin-down terms. We at IP Fabric have been singing about it for years, and our experience in doing so is that everyone has their own criteria for what constitutes proper assurance of a network. Here, we're sharing our definition. We've drilled down into the practical, specific components, to help you map out your plan for a fully assured network.
Frankly speaking, there's also the option to toss out the map and let our automated network assurance platform deliver you the goods. If you're ready for that, book a tailored demo with our team, but ready or not, you should probably still know exactly what an automated network assurance platform should deliver. Read on!
To have a truly holistic view of the network, you need to have easy access to these five elements:

First up, you have to know - at any point in time - precisely which devices (what vendor, what model?) exist in your network, where they are located, and what code version is running on each device. Without this, anything else is purely a presumption.
Without automated network assurance: You can find and collate this information manually by consolidating disparate resources scattered across your organization, like your CMDB, spreadsheets, procurement systems, etcetera. If you're including static documents in this, it's likely they're outdated by the time you're using them to help centralize inventory information.
With automated network assurance: Every point-in-time network snapshot, taken on demand or as scheduled, contains network inventory information that has been acquired through lightweight, lightning-quick CLI-based discovery over Telnet, SSH or API.
It's essential to understand the desired configuration for your various network devices, and whether each device is actually configured according to the templates containing your intent.
Without automated network assurance: This lives in hand-built templates. If you're lucky, you have a configuration backup system. However, there's a good chance it may be incomplete or out of date.
With automated network assurance: Once again, configuration information is available automatically, acquired through lightweight, lightning-quick CLI-based discovery, and normalized for analysis. Built-in or custom intent checks also ensure you know about any misconfiguration present.
How is each device actually behaving at a particular point in time, and is it as you intended?
Without automated network assurance: There is not generally one place to go for this information; engineers have to manually mine this information by logging into each network device. This would only be done when troubleshooting involves a specific device; ultimately, a reactive approach.
With automated network assurance: This information is part of the discovery process and is included in an automatically generated network model. This means when reviewing, the state information sits alongside config info to give you a much more complete view of your network's behavior.
Using Inventory, Configuration, and State information, it's essential to draw out the layers of connectivity in your network, so you can understand the interconnectivity and different paths that data may take.
Without automated network assurance: This would be manually drawn by engineers who must investigate and gather information about the network from various disparate sources, using Visio or otherwise. Note that these are static, need maintenance, and do not represent the actual network state, only the expected state.
With automated network assurance: Topology maps of the whole network, including security information, are automatically generated. Note that these represent actual state at a particular point in time, which is very useful for comparing different snapshots for historical troubleshooting.
Without automated network assurance: To understand end-to-end behavior, engineers would have to look at different diagrams, and talk with different teams and people (e.g. security and cloud teams), cobbling together a view as best they can with what's available.
With automated network assurance: No patchworking needed. Ask your network anything! Run queries against this normalized data to see end-to-end paths of packets through the network, and understand the flow of a packet from endpoint to endpoint.
Having these five elements accessible and consumable in technology tables, dashboards, and topology maps forms your network baseline, and though this is really just the first step for companies adopting automated network assurance, it can be transformative.
For example, it's fairly common for IP Fabric customers to find previously unknown devices or misconfigurations in their network within an hour or so of kicking off their POC - that is, before full deployment in their network! With this evidence looking enterprise network leaders in the eye, it's tough to deny the value of automated network assurance.

Though a massive benefit, automating network assurance is not just a means to streamline operations and have faster access to network insights - it is essential to ensuring you have the right data, in a consumable manner.
In an enterprise environment, one could argue manual methods of collecting inventory, config, and state information, producing topologies and end-to-end paths will never be accurate or represent your actual network state, as the network is too dynamic.
So yes, technically, you could let your network teams run around collecting, collating, and visualizing this data manually, but it's likely a waste of their hard work and talent, as the results will never be that useful in a constantly changing network. Automating this, on the other hand, usually has surprising results beyond the expected benefits, as engineers have the capacity to be creative with network data and reimagine their approach to network operations.
Follow us on LinkedIn, and on our blog, where we regularly publish new content. Want to find out for yourself how IP Fabric can help you to revolutionize your networking operations and processes? Request a demo here.
Will you be at Cisco Live 2023? Let us know, and book some time with our team! Click below to see what Cisco Live means to us.