Speak
Tech
To me!
Tech
To me!
Want to get right to the nuts and bolts of how IP Fabric’s automated network assurance platform works? Start here.
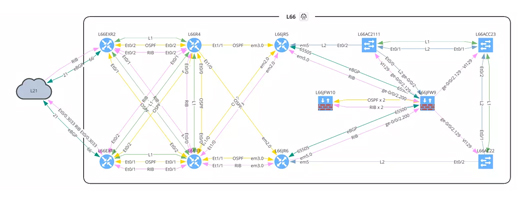
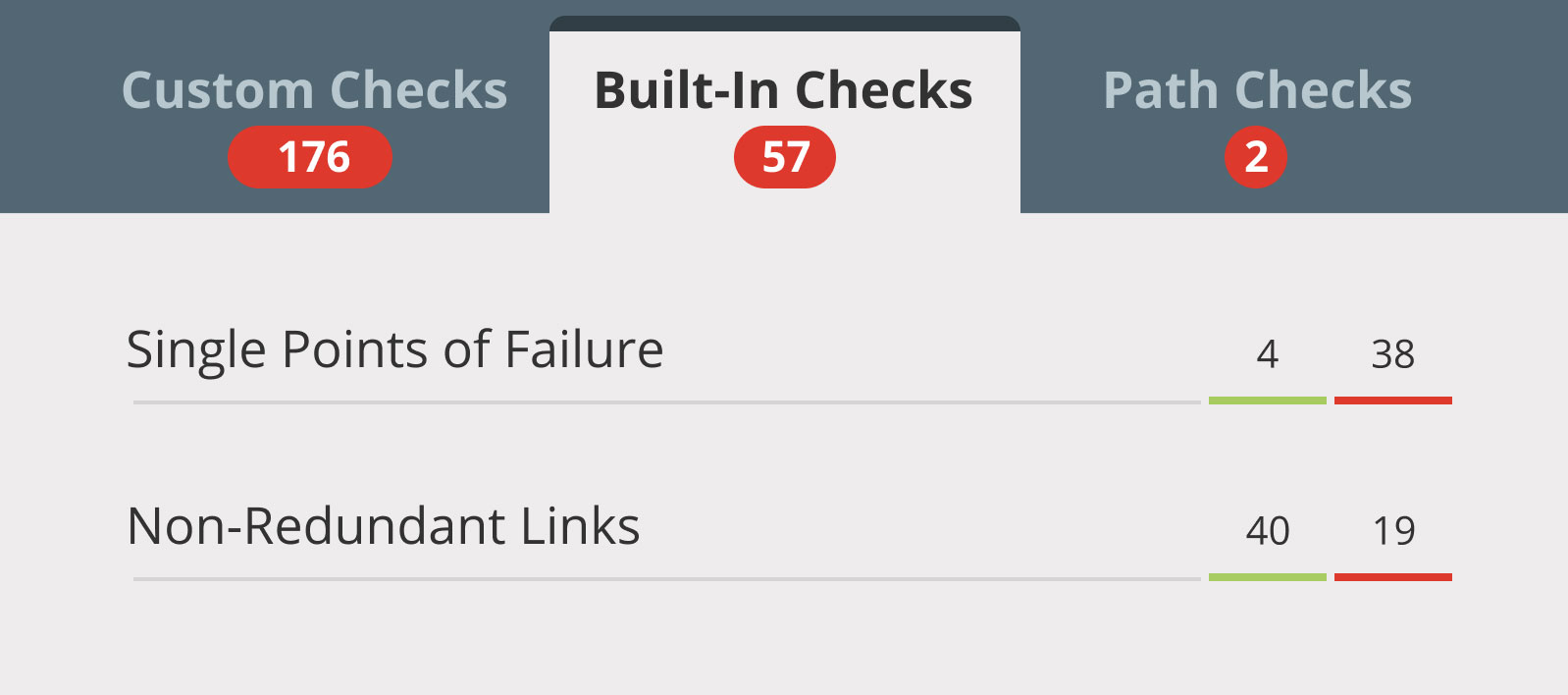
Our Approach to Network Discovery
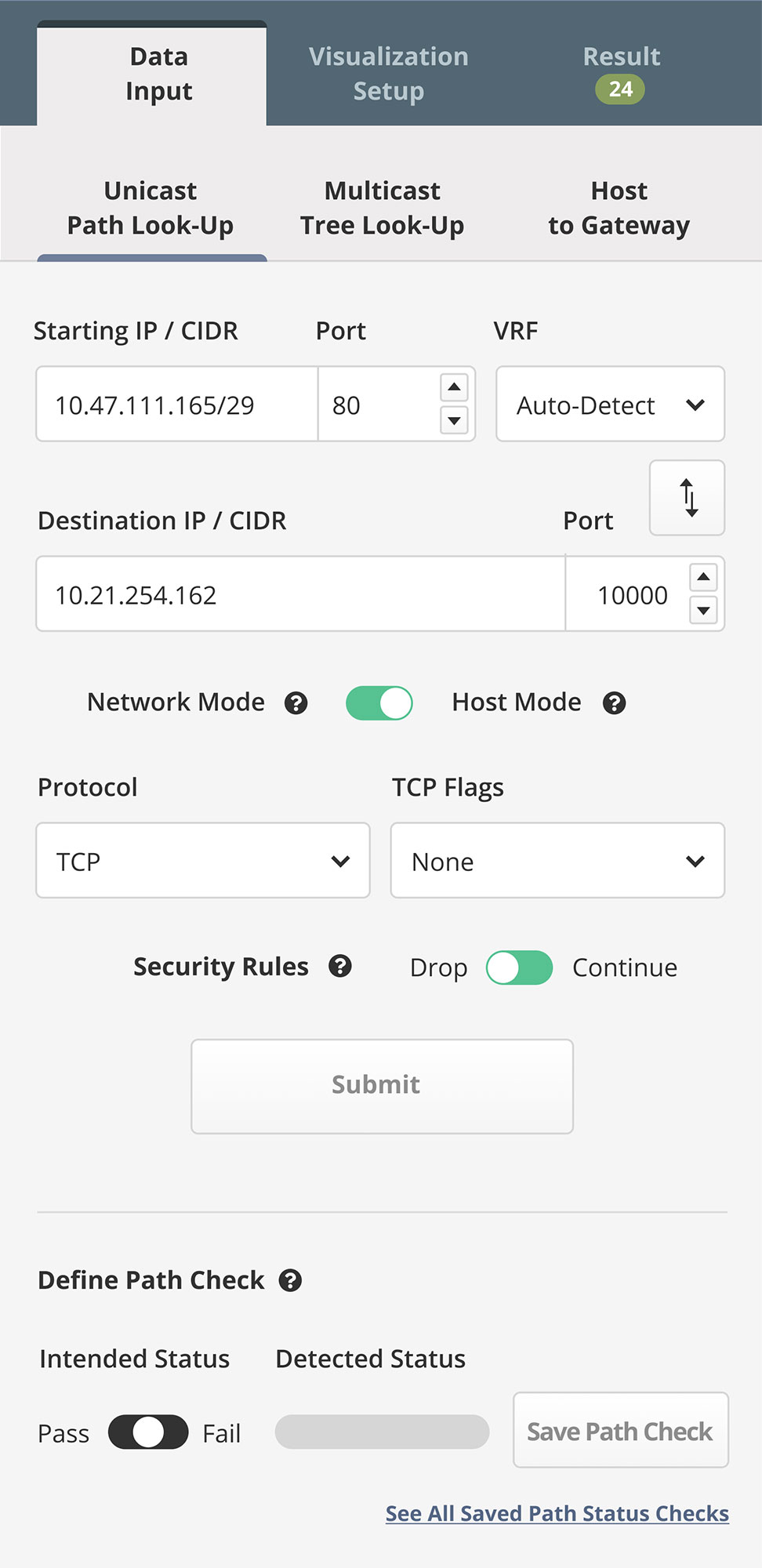
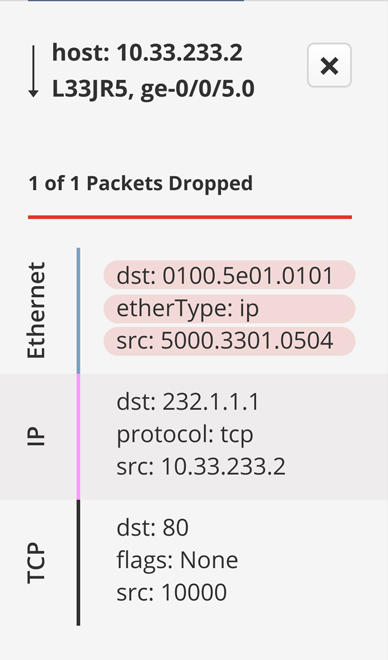
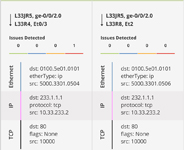
Data Modeling
Data Visualisation
Integrations via API
Product documentation